Posted by Helen Martin on Mar 1, 2019
 In a presentation at VB2018, Michael Daniel, President and CEO of the Cyber Threat Alliance, outlined exactly how threat sharing strengthens a company's competitive advantage. Today we release the recording of his presentation.
In a presentation at VB2018, Michael Daniel, President and CEO of the Cyber Threat Alliance, outlined exactly how threat sharing strengthens a company's competitive advantage. Today we release the recording of his presentation.
Posted by Martijn Grooten on Feb 25, 2019
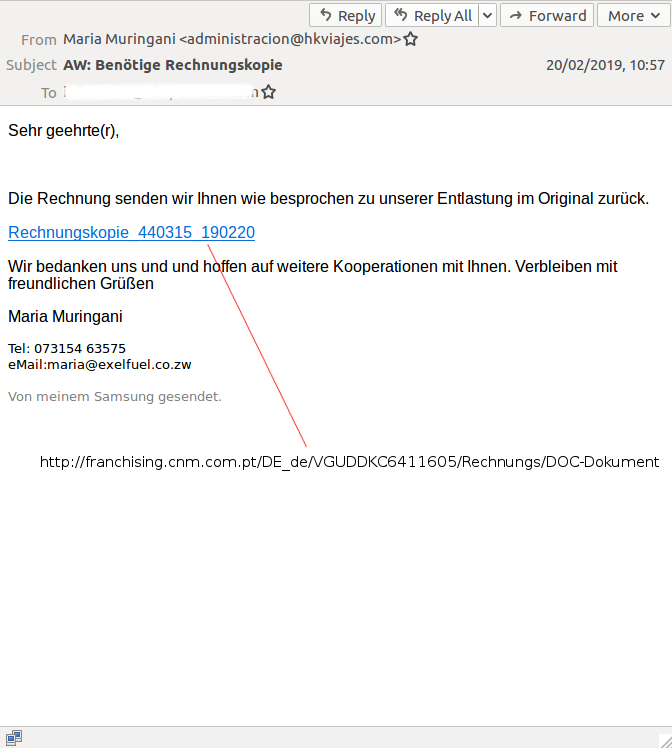 The set-up of the VBSpam test lab gives us a unique insight into the kinds of emails that are more likely to bypass email filters. This week we look at the malspam that was missed: a very international email with a link serving Emotet, an Italian Ursnif campaign with a password-protected ZIP and an email to which a clumsy spammer had attached a list of email addresses rather than a payload.
The set-up of the VBSpam test lab gives us a unique insight into the kinds of emails that are more likely to bypass email filters. This week we look at the malspam that was missed: a very international email with a link serving Emotet, an Italian Ursnif campaign with a password-protected ZIP and an email to which a clumsy spammer had attached a list of email addresses rather than a payload.
Posted by Martijn Grooten on Feb 22, 2019
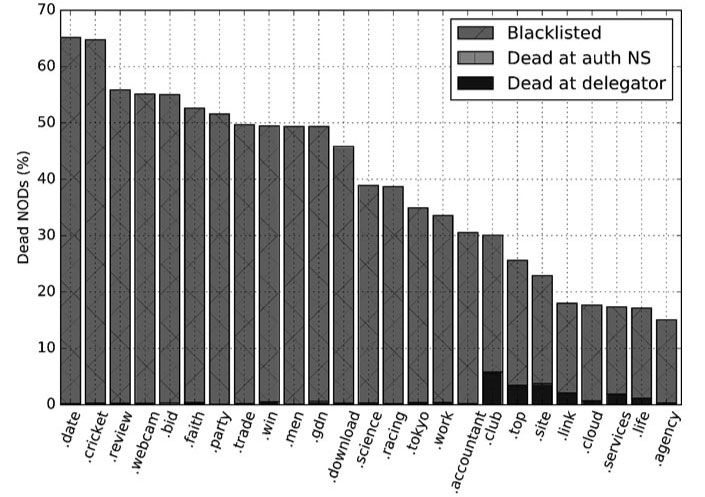 Domains play a crucial role in most cyber attacks, from the very advanced to the very mundane. Today, we publish a VB2018 paper by Paul Vixie (Farsight Security) who undertook the first systematic study into the lifetimes of newly registered domains.
Domains play a crucial role in most cyber attacks, from the very advanced to the very mundane. Today, we publish a VB2018 paper by Paul Vixie (Farsight Security) who undertook the first systematic study into the lifetimes of newly registered domains.
Posted by Martijn Grooten on Feb 20, 2019
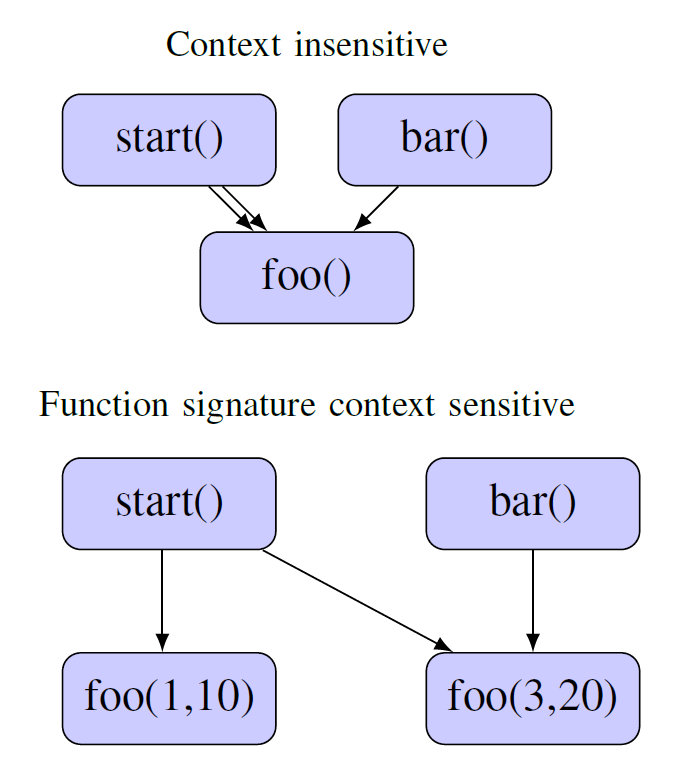 Constraint programming is a lesser-known technique that is becoming increasingly popular among malware analysts. In a paper presented at VB2018 Thaís Moreira Hamasaki presented an overview of the technique and explained how it can be applied to the analysis of (potentially) malicious binaries. Today, we publish both Thaís' paper and the video of her presentation.
Constraint programming is a lesser-known technique that is becoming increasingly popular among malware analysts. In a paper presented at VB2018 Thaís Moreira Hamasaki presented an overview of the technique and explained how it can be applied to the analysis of (potentially) malicious binaries. Today, we publish both Thaís' paper and the video of her presentation.
Posted by Martijn Grooten on Feb 19, 2019
 With a little less than a month before the deadline of the call for papers for VB2019, Virus Bulletin encourages submissions from experienced speakers and newcomers alike.
With a little less than a month before the deadline of the call for papers for VB2019, Virus Bulletin encourages submissions from experienced speakers and newcomers alike.
Posted by Helen Martin on Feb 13, 2019
 At VB2018 in Montreal, Ixia researcher Stefan Tanase presented a thought-provoking paper on the current state of the Internet and the worrying tendency towards raising borders and restricting the flow of information. Today we publish both his paper and the recording of his presentation.
At VB2018 in Montreal, Ixia researcher Stefan Tanase presented a thought-provoking paper on the current state of the Internet and the worrying tendency towards raising borders and restricting the flow of information. Today we publish both his paper and the recording of his presentation.
Posted by Martijn Grooten on Feb 11, 2019
 The set-up of the VBSpam test lab gives us a unique insight into the kinds of emails that are more likely to bypass email filters. This week we look at the malspam that was missed: banking and email phishing, Emotet and Bushaloader.
The set-up of the VBSpam test lab gives us a unique insight into the kinds of emails that are more likely to bypass email filters. This week we look at the malspam that was missed: banking and email phishing, Emotet and Bushaloader.
Posted by Helen Martin on Feb 8, 2019
 The cybersecurity skills gap has been described as one of the biggest challenges facing IT leaders today. At VB2018 in Montreal, ESET's Lysa Myers outlined some of the things the industry can do to help address the problem. Today we publish Lysa's paper and the recording of her presentation.
The cybersecurity skills gap has been described as one of the biggest challenges facing IT leaders today. At VB2018 in Montreal, ESET's Lysa Myers outlined some of the things the industry can do to help address the problem. Today we publish Lysa's paper and the recording of her presentation.
Posted by Martijn Grooten on Feb 5, 2019
 We look forward the Nullcon 2019 conference in Goa, India, at which VB Editor Martijn Grooten will give a talk on the state of malware.
We look forward the Nullcon 2019 conference in Goa, India, at which VB Editor Martijn Grooten will give a talk on the state of malware.
Posted by Martijn Grooten on Feb 3, 2019
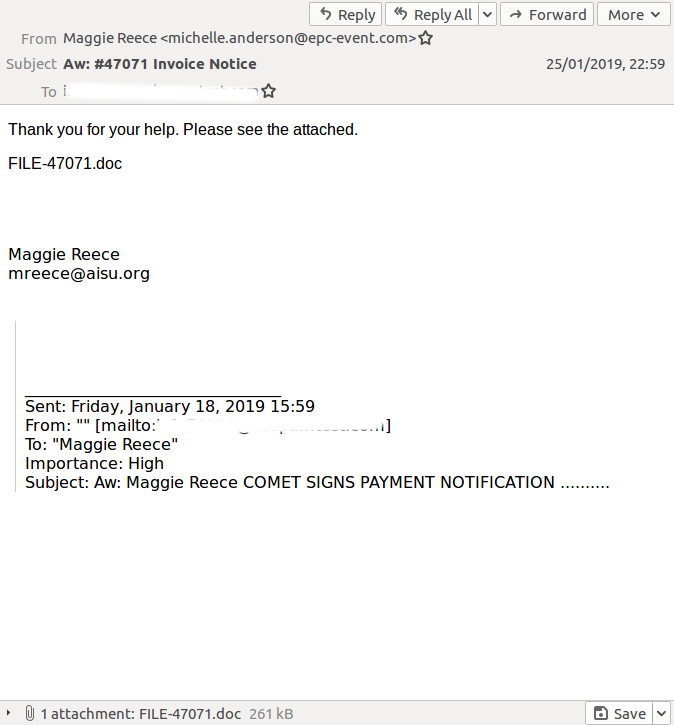 We see a lot of spam in the VBSpam test lab, and we also see how well such emails are being blocked by email security products. Recently some of the emails that bypassed security products included a broken Amazon phishing campaign, a large fake UPS campaign and malicious emails carrying Emotet and Lokibot.
We see a lot of spam in the VBSpam test lab, and we also see how well such emails are being blocked by email security products. Recently some of the emails that bypassed security products included a broken Amazon phishing campaign, a large fake UPS campaign and malicious emails carrying Emotet and Lokibot.