Posted by Martijn Grooten on Feb 11, 2019
This blog post was put together in collaboration with VB test engineers Adrian Luca and Ionuţ Răileanu. Virus Bulletin uses email feeds provided by Abusix and Project Honey Pot.
This year, Virus Bulletin's VBSpam test lab turns ten years old. Just as malicious and unwanted emails have evolved over the years, so has the lab. We continue to publish quarterly reports on the performance of email security products, but we also provide weekly feedback to the test participants, some of which have opted not to be included in the public reports but use this feedback to help improve their products and understand their performance in relation to that of competitor products.
This set-up also gives us a unique insight into the kinds of emails that are more likely to bypass email filters. On our blog, we regularly report on the malware and phishing emails for which this is the case.
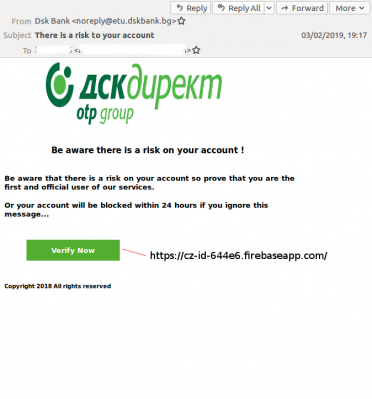
During the past week there were two phishing emails (in our definition phishing emails include those with a malicious link) that bypassed most of the email security products in our lab: one that masqueraded as a message (in English) from a Bulgarian bank, and another that masqueraded as a message from Microsoft Office 365. Banks have, for obvious reasons, long been a target of phishing campaigns, while email account credentials are valuable both for the content of the mailbox and for the ability to send emails from them.
The bank email linked to a site hosted on Firebase, a Google-owned app development platform, while the Microsoft email linked to a URL on a compromised website. The use of legitimate services or compromised domains for links helps the emails bypass domain-based blocklists, which is a first step towards bypassing email filters.
 |
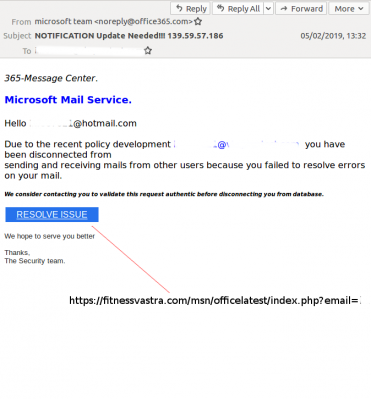 |
Left: Email masquerading as message from a Bulgarian bank. Right: Email masquerading as a message from Microsoft.
A better way to achieve high delivery rates, though, is to send the emails in small, very targeted batches. This explains why delivery rates for both phishing and malware tend to be many times higher than those of ordinary spam, which is still sent in very large numbers with only a tiny fraction of the messages making it to inboxes.
Given the lower delivery rate of larger campaigns, we were somewhat surprised this week to see two fairly large malware campaigns with quite high delivery rates.
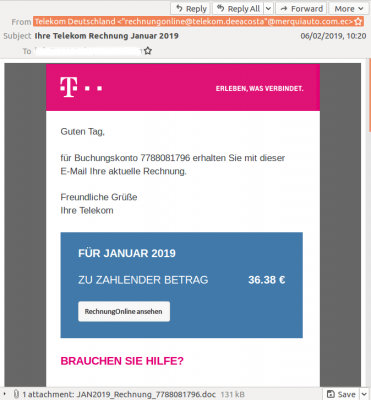
Emails in German claiming to contain a bill from Deutsche Telekom (a large telecommunications provider) were spreading Emotet, a malware family that is commonly spread via spam campaigns. Emotet is known to have been used as a stepping stone in some pretty damaging malware campaigns, including recent Ryuk infections. Emotet infections can thus be rather costly.
A second large and quite poorly blocked malware campaign was based on an email sent in Italian which claimed to contain an invoice. The attachment was a RAR archive which included a single .vbs file, an instance of the Bushaloader downloader. Though we did not analyse the malware in this case, there was a similar campaign in November that served the Danabot banking trojan.
 |
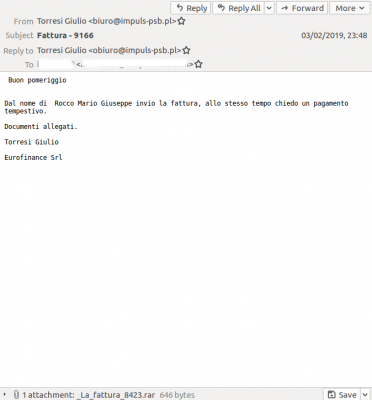 |
Left: Email claiming to contain a bill from Deutsche Telekom. Right: Email in Italian claiming to contain an invoice.
If you would like your product to be tested in our lab, to receive weekly updates on its performance and, optionally, be included in our quarterly public reports, or if you have a question about our research, don't hesitate to contact us at [email protected].
Emotet (.doc attachments; SHA256)
40c9e3b16e84ffbf7c1584aacd2e1888e33fb8ef6e3f7481c89da1ffeb217648
766533f5d447ec654ef6d99b9a755f3a45dfa5d20f06ba9adc08a27ece9fe181
aca76ed51926cab89416a4ec88bf7011ee6ee401ad3ed85e4d1ddd68efdef324
b64aa55d7a84cec25829a46c9a714c8649aaf1966f3e3a30d1890b70e9c3a17b
bb7f1524770d7ab49b7c4e3171059ddad674bac19b114610565fb3b8f6896612
d5ac5183d4ca6e96e81243a5f102c8b3a4ebab61714d4be11c0ad5bdfdb470d3
e490438fad86371a3f7a77ab06e42067cac03d07b68a80edf1276c964030a595
f1ee64c36fb96a8b2496915eabc7beb81a61778b82e32ebbab25a22ba34e7c53
f2667d8ffd157a7d19d913be1f19a6d585061fadde8196782d2b636a73f97e44
Bushaloader (.rar attachments; SHA256)
25f1c205f4936c4c112d709dc7bd859efc070bca464ba872ed025032d1798278
399ff526fc6c3c6e408e442fad76825c6d2a4558363354654c626d98e810cc42
510496ce3730492851975f50cbefbf912ceea8bb22dc3fcfd093991e0ab48466
6c8038be2e16ee02bc674bc413e8dfcc35f2246af872f6f0543668125a52f147
af7504ee7f8dff077a7a3d976b452738ff74654515ae6d2484558f6a95a60ea3
d396ff3a539c74469ee5375884f1d5c97aef17735d6435049620bab2ae456b2e
f7e41ded5efc99591de0cff3df37da8a01d62984342e218e1c3ced605fd51d2a
fd01b91276935f6dd56651b69aa0f8438d454d666fa54213893db26cf284ede2