Posted by Martijn Grooten on Feb 3, 2019
This blog post was put together in collaboration with VB test engineers Adrian Luca and Ionuţ Răileanu.
On this blog, we regularly look at those phishing and malware emails that we notice bypassing email security products in our test lab – something which they do at much a higher rate than ordinary spam emails. This is especially noticeable in phishing emails: last week the average phishing email had a seven per cent chance of bypassing a product in our lab.
As always, the spam feeds we used were provided by Abusix and Project Honey Pot. If you would like your product to be tested in our lab, to receive weekly updates on its performance and, optionally, be included in our quarterly public reports, please contact us at [email protected].
Update further investigation showed that we unfairly blamed the spammers for breaking the emails. In fact, it was a bug on our end that broke this particular email. This may have caused some products to miss it.
One thing that continues to surprise us is the fact that a lot of spam is broken in one way or another. Recently, this included a 419 spam campaign in which the subject line of the email included the credentials of the compromised email account from which the spam was to be sent, as well as an Amazon phishing email that was missed by the majority of products in our lab.
The phishing email did actually use a simple but clever trick: the body of the email consisted of a single embedded image that looked like a genuine Amazon receipt. The whole image linked to a phishing site. It is easy to see how this could trick both users and email security products.
However, those behind the campaign had made a basic mistake in the Quoted-Printable encoding and it is likely that most mail clients wouldn't have been able to display it correctly. It is possible that this contributed to the low block rate of the email.
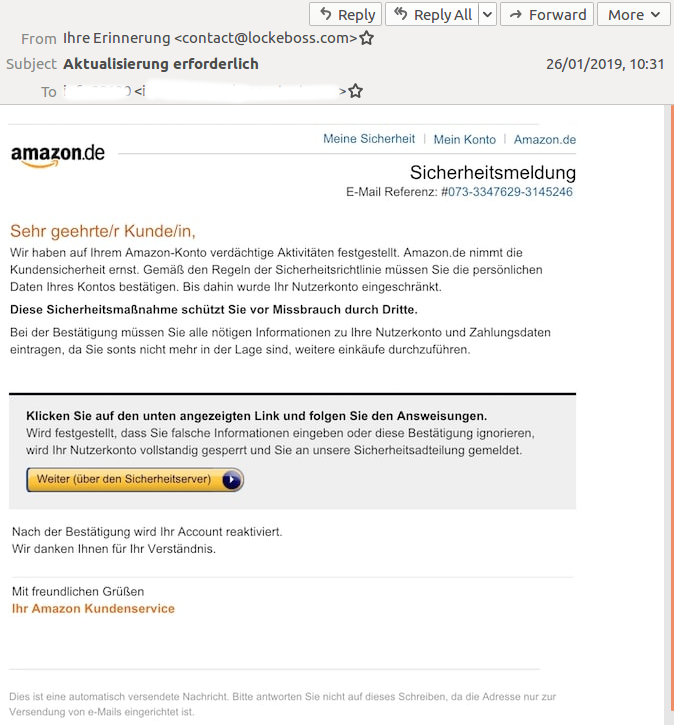
The email as it was meant to look.
No mistakes appear to have been made in the more than 80 UPS phishing emails we saw being sent in a short period of time. What was notable was the high miss rate: the first email in this campaign was missed by no fewer than 11 products in our lab and subsequent emails continued to be missed, often by half a dozen products or more. Usually, large campaigns tend to have very high block rates.
We plotted the delivery times of the emails (in UTC on 29 January) against the number of products that failed to block them and noticed only a small downward trend. It is, of course, possible that this was actually a very targeted campaign and we were simply 'lucky' to have received so many of them.
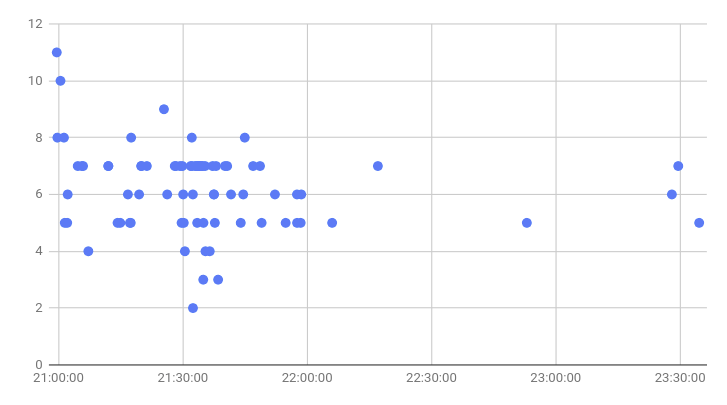 The number of products that missed UPS phishing emails plotted against the time (UTC) the emails were delivered.
The number of products that missed UPS phishing emails plotted against the time (UTC) the emails were delivered.
As for the emails themselves, they linked to different URLs, all of which were hosted on the same IP address (167.88.161.62), which had previously been used to spread Gandcrab. However, when we checked, the payload had been taken down and all URLs were serving a one-byte file. The majority of domains, which we think had probably had their DNS compromised, still point to the same IP address though.
 Though the emails used different subject lines and links, they all looked virtually the same.
Though the emails used different subject lines and links, they all looked virtually the same.
Emotet continues to be prominent, not only among malicious emails in general but also among those emails missed by multiple products in our lab. The sophistication of Emotet's operation was detailed in a recent research paper by Trend Micro, while Cisco Talos noted how the spam-sending component of the malware checks various IP-based blacklists before deciding whether to send emails. Indeed, we often see Emotet delivered from IP addresses not listed on various blacklists.
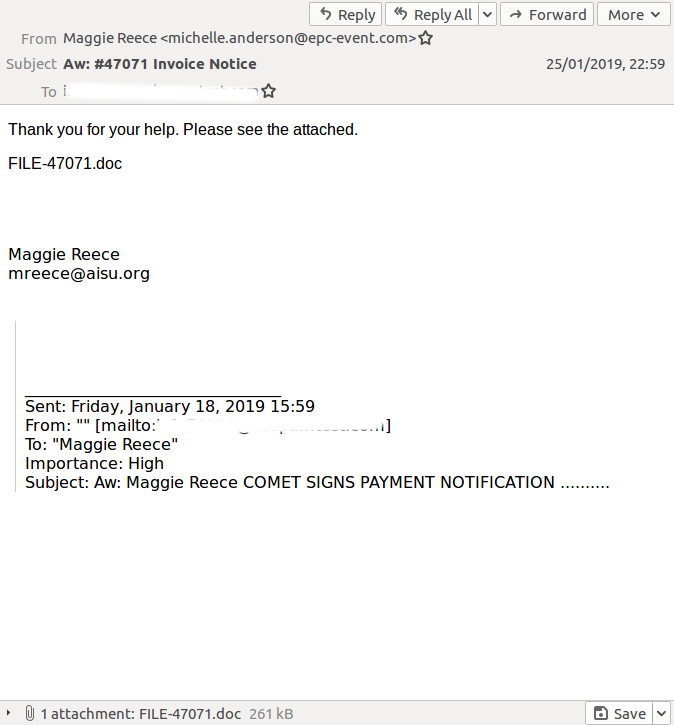
This fake invoice (attachment SHA256: 7f7c9f6de90cbfeca9441f1ef560a1da77718c364cc68f6bf7fba2b148e14cd7) was missed by six products in our lab.
Another email that several products missed carried an RTF attachment that circumstantial evidence suggests would download either Formbook or AZORult. VB recently published a VB2018 paper by Deloitte researcher Gabriela Nicolao on Formbook.
Four email security products blocked an email with an .ace attachment. ACE is a lesser-known proprietary archiving format that has been used to deliver malware for quite some time. It does provide a clear benefit, as can be seen by the difference in the number of static detections on VirusTotal of the .ace attachment compared with that of the executable (a sample of Lokibot) stored inside it.
However, it is unlikely that the average recipient would have the tools on their machine to open such an .ace file, especially since it was compressed using the newer 2.0 format. The email did not provide instructions on how to open the file.
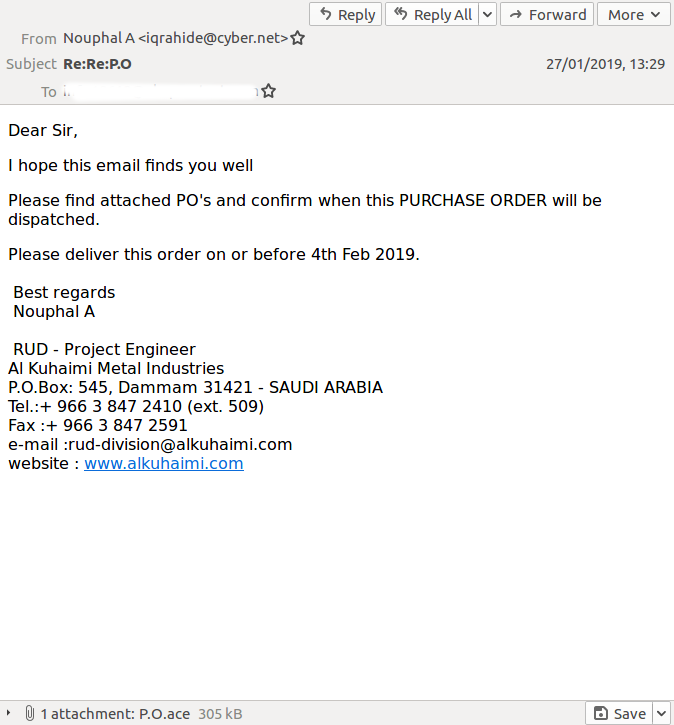
The fake purchase order email that 'aced' its way past several email security products.