Posted by Martijn Grooten on Feb 25, 2019
This blog post was put together in collaboration with VB test engineers Adrian Luca and Ionuţ Răileanu. Virus Bulletin uses email feeds provided by Abusix and Project Honey Pot.
In our VBSpam test lab, we continue to receive spam from around the world, including a fair number of emails carrying malware, or with a malicious or deceptive link. Products participating in our VBSpam tests receive weekly feedback on their performance (including an overview of those emails that were missed), while those that opt for public testing are also included in our quarterly reports and qualify to obtain VBSpam certification.
In this blog post, we look at some of the interesting 'malspam' we have spotted recently, mostly through its ability to bypass security products.
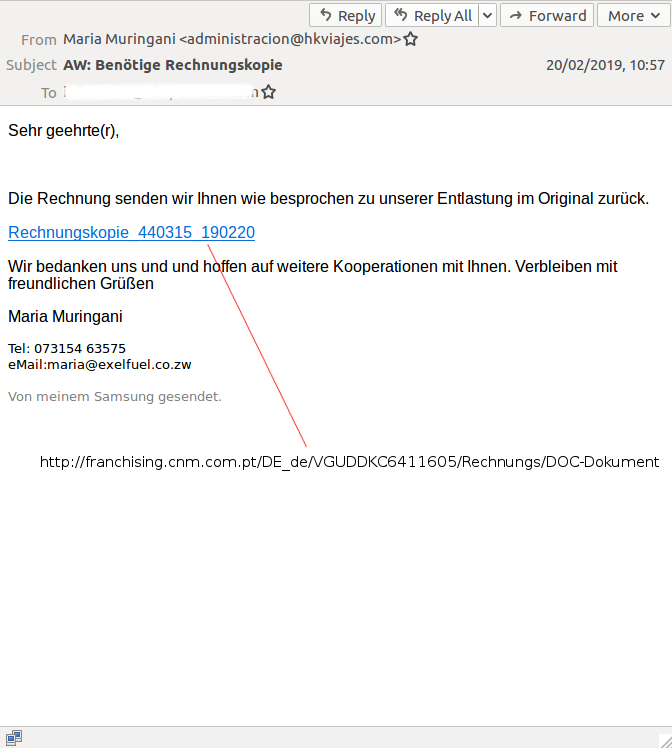
Emotet often gets a mention in these blog posts as its campaigns, whether they use a malicious link or an attachment, often bypass email security products. We recently saw a very international email with a link to Emotet that was missed by no fewer than nine of the products in our lab, as well as by most IP- and domain-based blacklists.
The email was written in German but was sent in the name of a Zimbabwean individual that a Google search suggests exists – though it seems unlikely that she sends email from a domain belonging to a Uruguayan firm. It also seems unlikely that would she send her emails from a (possibly compromised) server in the US, or link to Russian malware hosted on a compromised Portuguese site. That malware, VirusTotal confirms, was an Emotet downloader (the site has since been fixed).
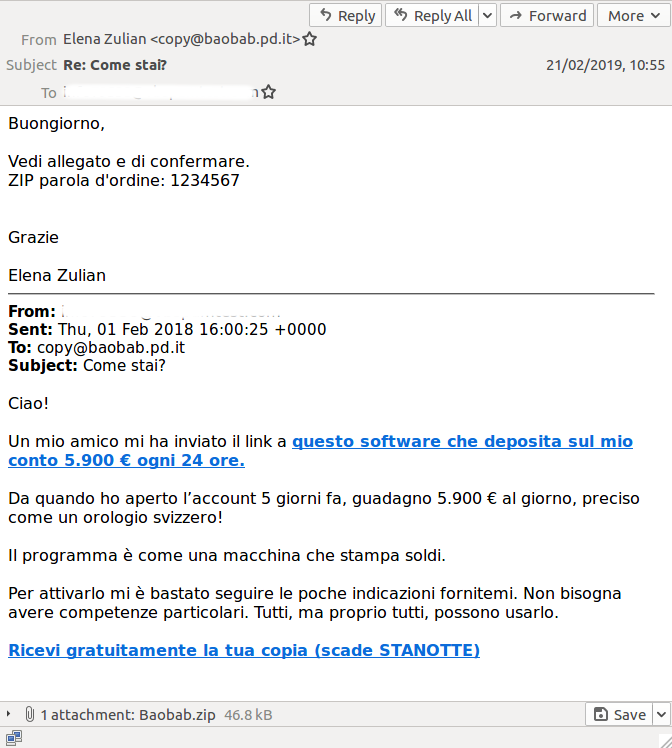
Emails with a malicious attachment tend to have slightly higher block rates, but we still found one that was missed by six products. It was written in Italian, delivered Ursnif, and it appeared to be a reply to an email previously sent by the recipient (in this case the reply was to a spam email). Ursnif was seen using this technique last year.
This time, however, there was a twist: the attachment was put inside a password-protected zip with the password ('1234567') in the body of the email. This made a big difference in the detection of the attachment: the zip file itself (SHA256: c7473aa1979fbf85120f50b994f5787297bb41d7610c2603e634648abeb3312f) wasn't detected by any product on VirusTotal, while the Word document inside (SHA256: bcb7da68a6ea609adb7531706f120d4079fef3e82d1a2357d4dcbea9661bf08b) was detected by 20 products.
The point here is not to comment on the 20 detections, for there are often valid reasons why a downloader isn't detected statically, but to point to the difference that putting an attachment inside a password-protected ZIP file makes. As it happens, '1234567' is a password that has previously been used in such campaigns (which are hardly a novelty), yet anti-virus engines may be reluctant to attempt to 'crack' a file, for fear of interfering with the sender's or recipient's privacy.
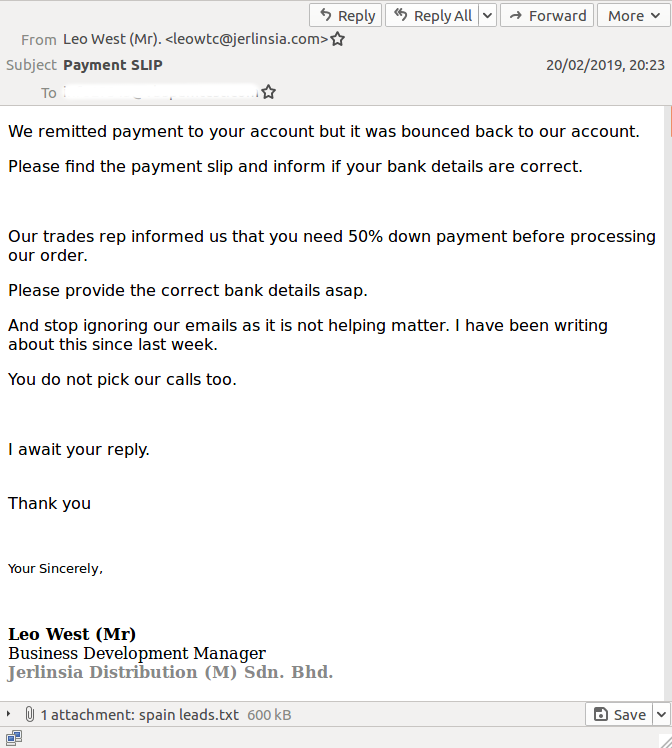
The most notable spam email we spotted this week didn't stand out because of its low block rates, but because of a clumsy mistake made by the sender: as an attachment it included a list of 25,907 addresses rather than a piece of malware.
It is not hard to see how a spammer could have made this mistake: a typical spam campaign is managed through a web interface where one has to upload an email template, a recipient list and an attachment. The spammer simply selected the wrong file as the email attachment.
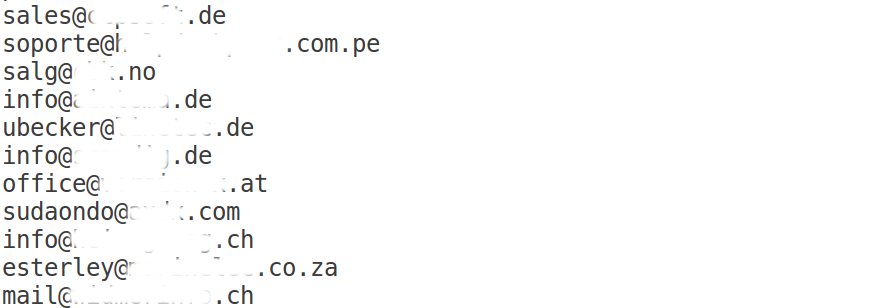
However, the list of email addresses does give us some interesting insight into how targets are chosen for a typical malspam campaign. The prevalence of contact@ and info@ addresses stands out, which suggests that these are addresses scraped off websites. Indeed, a random selection confirmed that these addresses were present on the web.
Not only does this mean that this list is the result of scraping the web for email addresses, it also suggests that either this scraping has been done recently, or the scraper has checked back to confirm the addresses are still present. This would probably help them avoid spam traps, which in turn helps keep a campaign under the radar.
And this also explains why the list of just over 25k addresses is very small compared to the typical spam campaign that sends emails to millions of recipients.
Note: though the attachment is called 'spain_leads.txt', there is nothing to suggest the list of addresses is in any way related to Spain. Spanish email addresses make up just a little over 1 per cent of those in the list.
Would you like your product to be added to our test lab for regular testing? Don't hesitate to contact [email protected] for the various options available.