Posted by Helen Martin on Apr 25, 2019
 A former reporter by profession, Andrew Brandt's curiosity was piqued when he came across what appeared at first glance to be the website of a small-town newspaper based in Illinois, but under scrutiny, things didn’t add up. At VB2018 he presented a paper in which he shared the results of his investigation of the site. Today, we publish his paper and the recording of his presentation.
A former reporter by profession, Andrew Brandt's curiosity was piqued when he came across what appeared at first glance to be the website of a small-town newspaper based in Illinois, but under scrutiny, things didn’t add up. At VB2018 he presented a paper in which he shared the results of his investigation of the site. Today, we publish his paper and the recording of his presentation.
Posted by Martijn Grooten on Apr 24, 2019
 In a new paper published today, independent researcher Nikolaos Tsapakis writes about the possibilities of malware using NTP as a covert communication channel and how to stop this.
In a new paper published today, independent researcher Nikolaos Tsapakis writes about the possibilities of malware using NTP as a covert communication channel and how to stop this.
Posted by Martijn Grooten on Apr 5, 2019
 VB is excited to reveal the details of an interesting and diverse programme for VB2019, the 29th Virus Bulletin International Conference, which takes place 2-4 October in London, UK.
VB is excited to reveal the details of an interesting and diverse programme for VB2019, the 29th Virus Bulletin International Conference, which takes place 2-4 October in London, UK.
Posted by Martijn Grooten on Mar 27, 2019
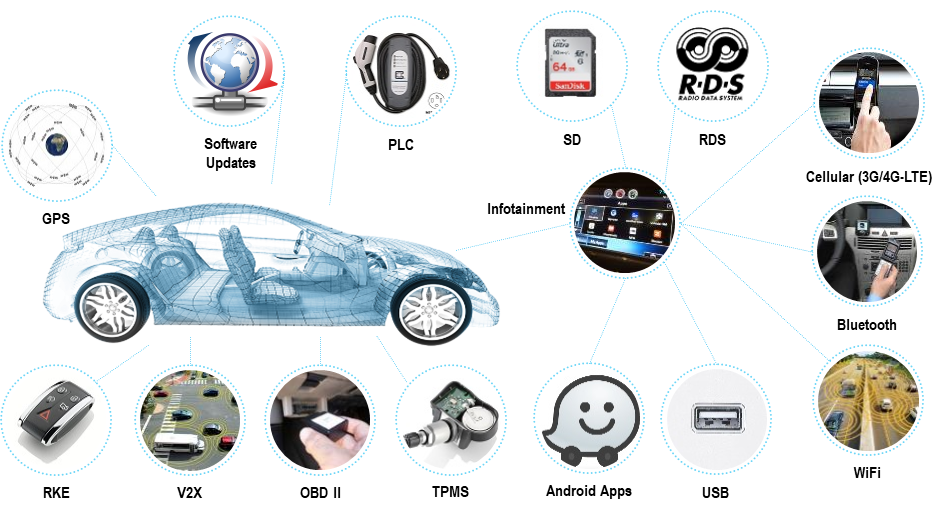 Car hacking has become a hot subject in recent years, and at VB2018 in Montreal, Argus Cyber Security's Inbar Raz presented a paper that provides an introduction to the subject, looking at the complex problem, examples of car hacks, and the challenges ahead. Today, we publish both Inbar's paper and the recording of his presentation.
Car hacking has become a hot subject in recent years, and at VB2018 in Montreal, Argus Cyber Security's Inbar Raz presented a paper that provides an introduction to the subject, looking at the complex problem, examples of car hacks, and the challenges ahead. Today, we publish both Inbar's paper and the recording of his presentation.
Posted by Martijn Grooten on Mar 20, 2019
 Static analysis and dynamic analysis each have their shortcomings as methods for analysing potentially malicious files. Today, we publish a VB2018 paper by Check Point researchers Yoni Moses and Yaniv Mordekhay, in which they describe a method that combines static and dynamic analysis to defeat app obfuscation in Android binaries. We also publish the video of their presentation.
Static analysis and dynamic analysis each have their shortcomings as methods for analysing potentially malicious files. Today, we publish a VB2018 paper by Check Point researchers Yoni Moses and Yaniv Mordekhay, in which they describe a method that combines static and dynamic analysis to defeat app obfuscation in Android binaries. We also publish the video of their presentation.
Posted by Martijn Grooten on Mar 15, 2019
 The call for papers for VB2019 closes on 17 March, and while we've already received many great submissions, we still want more!
The call for papers for VB2019 closes on 17 March, and while we've already received many great submissions, we still want more!
Posted by Martijn Grooten on Mar 13, 2019
 Registration for VB2019, the 29th Virus Bulletin International Conference, is now open, with an early bird rate available until 1 July.
Registration for VB2019, the 29th Virus Bulletin International Conference, is now open, with an early bird rate available until 1 July.
Posted by Martijn Grooten on Mar 8, 2019
 When we are calling for papers for the Virus Bulletin conference as we are doing now, we really mean a written paper. But don't worry if you've never written a paper - we can help!
When we are calling for papers for the Virus Bulletin conference as we are doing now, we really mean a written paper. But don't worry if you've never written a paper - we can help!
Posted by Martijn Grooten on Mar 8, 2019
 Amit Serper first analysed the OSX/Pirrit adware in 2016, highlighting some of its malware-like techniques, and soon afterwards started receiving legal threats from the company behind it. At VB2018 Amit gave a presentation in which he discussed both the adware and the legal threats he received for calling it malware. Today, we publish the video of Amit's presentation.
Amit Serper first analysed the OSX/Pirrit adware in 2016, highlighting some of its malware-like techniques, and soon afterwards started receiving legal threats from the company behind it. At VB2018 Amit gave a presentation in which he discussed both the adware and the legal threats he received for calling it malware. Today, we publish the video of Amit's presentation.
Posted by Martijn Grooten on Mar 5, 2019
 In December 2016, the CRASHOVERRIDE malware framework was used to cause a blackout in Ukraine. At VB2018 in Montreal, Dragos researcher Joe Slowik presented a detailed paper on the framework, explaining how the malware works and how it targets various protocols used to operate the electric grid. Today we publish both Joe's paper and the recording of his presentation.
In December 2016, the CRASHOVERRIDE malware framework was used to cause a blackout in Ukraine. At VB2018 in Montreal, Dragos researcher Joe Slowik presented a detailed paper on the framework, explaining how the malware works and how it targets various protocols used to operate the electric grid. Today we publish both Joe's paper and the recording of his presentation.