Posted by Martijn Grooten on Feb 1, 2019
 At VB2018 in Montreal, researchers from Fraunhofer SIT looked at privacy vulnerabilities in legitimate Android family-tracking apps that leaked location data. Today, we publish both their paper and the video of their presentation.
At VB2018 in Montreal, researchers from Fraunhofer SIT looked at privacy vulnerabilities in legitimate Android family-tracking apps that leaked location data. Today, we publish both their paper and the video of their presentation.
Posted by Martijn Grooten on Jan 29, 2019
 Threat intelligence teams would do well to recruit journalists, whose experience is crucial in today's threat landscape.
Threat intelligence teams would do well to recruit journalists, whose experience is crucial in today's threat landscape.
Posted by Martijn Grooten on Jan 28, 2019
 Using data from our VBSpam lab, we looked at the malicious emails that have been missed recently by a large number of email security products.
Using data from our VBSpam lab, we looked at the malicious emails that have been missed recently by a large number of email security products.
Posted by Martijn Grooten on Jan 25, 2019
 The Formbook information-stealing trojan may not be APT-grade malware, but its continuing spread means it can still be effective. At VB2018 in Montreal, Gabriela Nicolao, a researcher from Deloitte in Argentina, presented a short paper in which she looked at Formbook's background and history and analysed a sample of the malware. Today, we publish Gabriela's paper.
The Formbook information-stealing trojan may not be APT-grade malware, but its continuing spread means it can still be effective. At VB2018 in Montreal, Gabriela Nicolao, a researcher from Deloitte in Argentina, presented a short paper in which she looked at Formbook's background and history and analysed a sample of the malware. Today, we publish Gabriela's paper.
Posted by Martijn Grooten on Jan 24, 2019
 With the VB2019 Call for Papers having opened last week, we explain how the selection procedure works, which may help you during your abstract submission.
With the VB2019 Call for Papers having opened last week, we explain how the selection procedure works, which may help you during your abstract submission.
Posted by Martijn Grooten on Jan 18, 2019
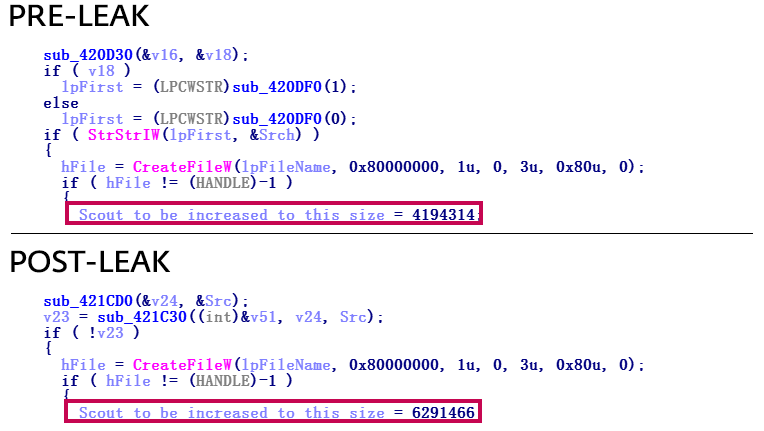 Today we publish the VB2018 paper and video by ESET researcher Filip Kafka, who looked at the new malware by Hacking Team, after the company had recovered from the 2015 breach.
Today we publish the VB2018 paper and video by ESET researcher Filip Kafka, who looked at the new malware by Hacking Team, after the company had recovered from the 2015 breach.
Posted by Martijn Grooten on Jan 17, 2019
 We see a lot of spam in the VBSpam test lab, and we also see how well such emails are being blocked by email security products. Worryingly, it is often the emails with a malicious attachment or a phishing link that are most likely to be missed.
We see a lot of spam in the VBSpam test lab, and we also see how well such emails are being blocked by email security products. Worryingly, it is often the emails with a malicious attachment or a phishing link that are most likely to be missed.
Posted by Helen Martin on Jan 17, 2019
 Mydoom turns 15 this month, and is still being seen in email attachments. This Throwback Thursday we look back to March 2004, when Gabor Szappanos tracked the rise of W32/Mydoom.
Mydoom turns 15 this month, and is still being seen in email attachments. This Throwback Thursday we look back to March 2004, when Gabor Szappanos tracked the rise of W32/Mydoom.
Posted by Martijn Grooten on Jan 15, 2019
 Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2019 is now open and we want to hear from you!
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2019 is now open and we want to hear from you!
Posted by Martijn Grooten on Jan 14, 2019
 Today, we publish a VB2018 paper by Google researcher Maddie Stone in which she looks at one of the most interesting anti-analysis native libraries in the Android ecosystem. We also release the recording of Maddie's presentation.
Today, we publish a VB2018 paper by Google researcher Maddie Stone in which she looks at one of the most interesting anti-analysis native libraries in the Android ecosystem. We also release the recording of Maddie's presentation.