Posted by Martijn Grooten on May 30, 2017
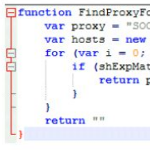 In a VB2016 last-minute presentation, Jaromír Horejší and Jan Širmer looked at Retefe, a trojan that has targeted banks in several European countries and used malicious proxy auto-config filesto redirect users' traffic to a server controlled by the attackers. A recording of their presentation is now available to view on our YouTube channel.
In a VB2016 last-minute presentation, Jaromír Horejší and Jan Širmer looked at Retefe, a trojan that has targeted banks in several European countries and used malicious proxy auto-config filesto redirect users' traffic to a server controlled by the attackers. A recording of their presentation is now available to view on our YouTube channel.
Posted by Martijn Grooten on May 17, 2017
 Perhaps the question we should be asking about WannaCry is not "why do so many organizations allow unpatched machines to exist on their networks?" but "why doesn't patching work reasonably well most of the time?"
Perhaps the question we should be asking about WannaCry is not "why do so many organizations allow unpatched machines to exist on their networks?" but "why doesn't patching work reasonably well most of the time?"
Posted by Martijn Grooten on May 15, 2017
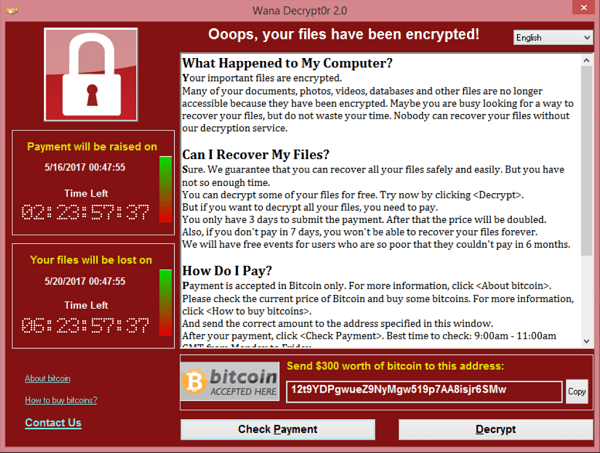 The WannaCry ransomware has affected many organisations around the world, making it probably the worst and most damaging of its kind. But modern security is not necessarily powerless against such threats.
The WannaCry ransomware has affected many organisations around the world, making it probably the worst and most damaging of its kind. But modern security is not necessarily powerless against such threats.
Posted by Helen Martin on May 11, 2017
 This week sees the 11th International CARO Workshop taking place in Krakow, Poland – a prestigious annual meeting of anti-malware and security experts. As a founding member of CARO, Fridrik Skulason was well placed, in August 1994, to shed some light on the organization, to explain in detail CARO's main activities and functions, as well as the reasons behind its strict membership regulations.
This week sees the 11th International CARO Workshop taking place in Krakow, Poland – a prestigious annual meeting of anti-malware and security experts. As a founding member of CARO, Fridrik Skulason was well placed, in August 1994, to shed some light on the organization, to explain in detail CARO's main activities and functions, as well as the reasons behind its strict membership regulations.
Posted by Martijn Grooten on May 10, 2017
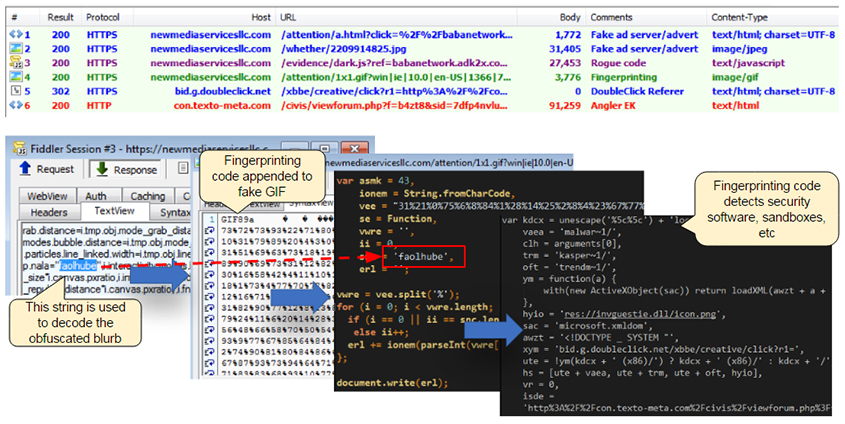 Malicious advertising, a.k.a. malvertising, has evolved tremendously over the past few years to take a central place in some of today’s largest web-based attacks. It is by far the tool of choice for attackers to reach the masses but also to target them with infinite precision and deliver such payloads as ransomware. Today, we publish a paper presented at VB2016 in Denver by Malwarebytes researchers Jérôme Segura and Chris Boyd, in which they look at the advertising ecosystem, how it is used, and at what techniques are being utilised to spread malware
Malicious advertising, a.k.a. malvertising, has evolved tremendously over the past few years to take a central place in some of today’s largest web-based attacks. It is by far the tool of choice for attackers to reach the masses but also to target them with infinite precision and deliver such payloads as ransomware. Today, we publish a paper presented at VB2016 in Denver by Malwarebytes researchers Jérôme Segura and Chris Boyd, in which they look at the advertising ecosystem, how it is used, and at what techniques are being utilised to spread malware
Posted by Helen Martin on May 4, 2017
 As DDoS attacks become costlier to fix and continue to increase in both number and diversity, we turn back the clock to 2000, when Aleksander Czarnowski took a look at the DDoS tools of the day.
As DDoS attacks become costlier to fix and continue to increase in both number and diversity, we turn back the clock to 2000, when Aleksander Czarnowski took a look at the DDoS tools of the day.
Posted by Martijn Grooten on May 4, 2017
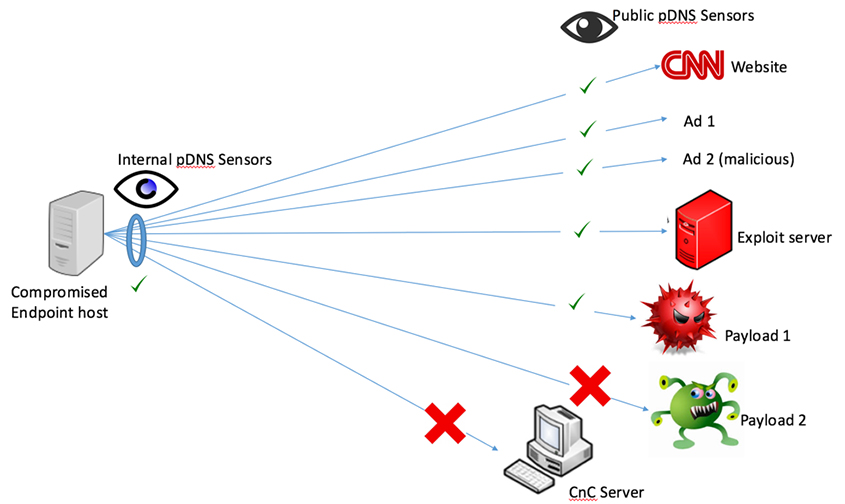 At VB2016, Splunk researchers Kathy Wang and Steve Brant presented a Splunk app that can be used to locally collect passive DNS data. A recording of their presentation is now available to view on our YouTube channel.
At VB2016, Splunk researchers Kathy Wang and Steve Brant presented a Splunk app that can be used to locally collect passive DNS data. A recording of their presentation is now available to view on our YouTube channel.
Posted by Martijn Grooten on Apr 28, 2017
In a VB2016 last-minute presentation, ESET researchers Peter Kalnai and Martin Jirkal looked at the OS X malware threats KeRanger and Keydnap, that both spread through a compromised BitTorrent client. A recording of their presentation is now available to view on our YouTube channel.
Read morePosted by Martijn Grooten on Apr 25, 2017
Consumer spyware is a growing issue and one that can have serious consequences: its use is increasingly common in domestic violence. But do our threat models consider the attacker with physical access to, and inside knowledge of the victim?
Read morePosted by Martijn Grooten on Apr 24, 2017
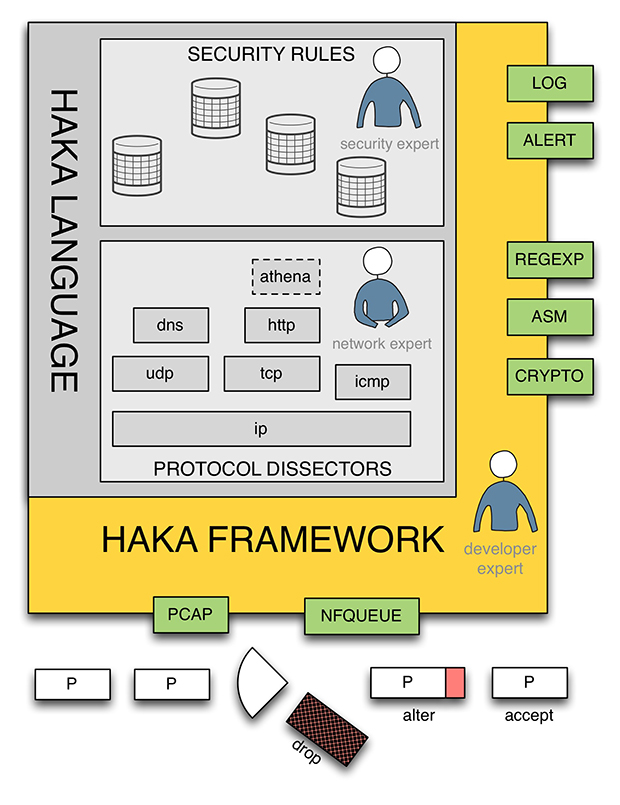 In their VB2016 paper, Stormshield researchers Benoît Ancel and Mehdi Talbi introduced Haka, an open-source language to monitor, debug and control malicious network traffic. Both their paper and the video recording of their presentation are now available to read/view on www.virusbulletin.com.
In their VB2016 paper, Stormshield researchers Benoît Ancel and Mehdi Talbi introduced Haka, an open-source language to monitor, debug and control malicious network traffic. Both their paper and the video recording of their presentation are now available to read/view on www.virusbulletin.com.