Posted by Martijn Grooten on May 15, 2017
We have become used to the idea of cybersecurity stories sometimes making the mainstream news, but the UK's newspapers across the spectrum, from broadsheets to tabloids, all opening with the same cybersecurity story – as they did on Saturday – is unprecedented. The reason for such a heightened level of interest was the crippling of the country's National Health Service (NHS) thanks to a ransomware attack that infected machines across the country and throughout the healthcare organisation.

Though the attack wasn't restricted to the NHS, or even the UK, hospitals having to send non-emergency patients home, and having to cancel operations and appointments, is probably the best illustration of the severe damage done by WannaCry, as the malware was named.
Just about every security company has written an analysis of the malware; I will just link to the blog post by security researcher MalwareTech, whose registration of one of the malware's C&C domains prevented it from spreading further.
Part of the reason why WannaCry was so damaging was that it spread via an SMB exploit, which allowed it to affect many computers within an organisation without user interaction. What made the story extra interesting is that the SMB exploit was first discovered by the NSA and leaked by the Shadow Brokers last month, when it turned out that Microsoft had already patched the vulnerabilities. (In an unprecedented move, Microsoft has now released a patch for Windows XP, three years after the company stopped supporting the operating system.)
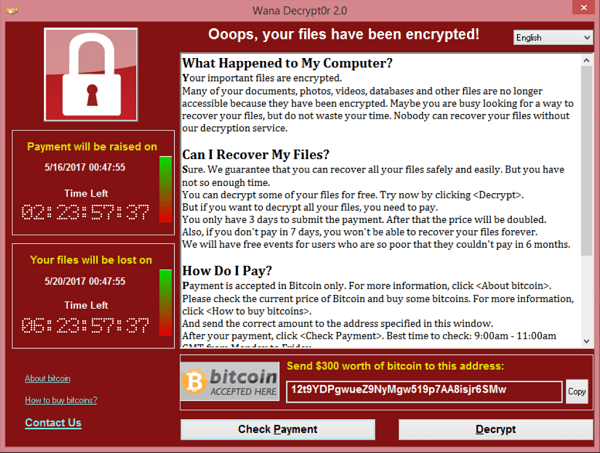
This also means that a fully patched machine would not have been affected by the ransomware; hence the urgent advice from security experts to patch all systems. A second important piece of advice is to turn off services one doesn't need. Finally, one should always make sure one has workable backups, thus making a ransomware infection a nuisance, rather than a full-scale disaster.
Easy though this may sound, it is a lot harder in practice, especially when operating within the constraints of a large organisation whose priority is to make people, rather than computers, better. And this is why, on top of following all these best practices, people are also advised to run security software.
But would anti-virus have stopped WannaCry from infecting a PC?
All anti-virus vendors will have updated their products' signatures to detect the versions of WannaCry that are circulating. This matters, as such signatures are the most reliable way of detecting malware. And because WannaCry is a worm, it will still be trying to infect new machines – for example those of people turning up at work on Monday morning. (The 'kill switch' programmed in the ransomware should also prevent the malware from spreading further, but there may be new variants without a kill switch; moreover the kill switch doesn't work when one is behind a proxy.)
Such static signatures wouldn't have helped the first victims on Friday, who were infected before the signatures were written. But signatures may still have helped avoid infection, as WannaCry wasn't new and the latest strain may have been detected through heuristics. Still, it's possible that the authors of the malware made sure their latest creation bypassed those signatures too. Luckily, modern anti-virus often includes signature-less components, which blocks malware based on its behaviour.
Now, a lot of malware tries to be as stealthy as possible to avoid behavioural detection. This won't work for ransomware though, as the encryption of many files on the hard drive isn't an activity that can be hidden. Indeed, this anti-ransomware technique was introduced in a paper (PDF) presented by K7 Computing researchers Samir Mody and Gregory Panakkal at VB2015 in Prague; you can find the video of their presentation below. Techniques like this can be found in many modern anti-virus products.
Without hard evidence, we cannot be sure how many WannaCry infections would have been stopped by anti-virus products. Of course, the malware only affected unpatched systems, and there is probably a strong correlation between people not updating their anti-virus (or not running it at all) and people not installing patches. Still, it is important to note that anti-virus can potentially stop such attacks, even before researchers have seen a sample.
Using anti-virus as a reason not to follow security best practice remains as bad an idea as ever. But being over confident in one's ability to follow such practices may be equally bad.
At VB2017 Jelena Milosevic, an independent security researcher who also happens to work as a nurse, will showcase the security problems in healthcare, the challenges faced when working within such an organisation, and describe what the consequences can be.
Registration for VB2017 is now open - register before 30 June 2017 to qualify for the early bird rate!