Posted by Helen Martin on Aug 2, 2016
 In 1994, along with the Olympic Games came an Olympic virus, from a group of Swedish virus authors calling themselves ‘Immortal Riot’. We look back at Mikko Hyppönen's analysis in the VB archive.
In 1994, along with the Olympic Games came an Olympic virus, from a group of Swedish virus authors calling themselves ‘Immortal Riot’. We look back at Mikko Hyppönen's analysis in the VB archive.
Posted by Martijn Grooten on Aug 1, 2016
 Announcing the VB2016 call for last-minute papers and a number of discounts on the conference registration rate.
Announcing the VB2016 call for last-minute papers and a number of discounts on the conference registration rate.
Posted by Virus Bulletin on Jul 28, 2016
In the run up to VB2016, we invited the conference sponsors to write guest posts for our blog. In the second of this series, ESET's Matías Porolli writes about malicious Visual Basic and JavaScript gaining prevalence in Brazil.
Read morePosted by Martijn Grooten on Jul 28, 2016
 The website of the Carol Davila University of Medicine and Pharmacy has been compromised to inject a hidden iframe into the site's source code that serves the Neutrino exploit kit and may infect visitors with ransomware.
The website of the Carol Davila University of Medicine and Pharmacy has been compromised to inject a hidden iframe into the site's source code that serves the Neutrino exploit kit and may infect visitors with ransomware.
Posted by Martijn Grooten on Jul 26, 2016
 While there are no actually risks involved in using MD5s in malware analyses, it reinforces bad habits and we should all start using SHA-256 instead.
While there are no actually risks involved in using MD5s in malware analyses, it reinforces bad habits and we should all start using SHA-256 instead.
Posted by Helen Martin on Jul 21, 2016
 In 2001, ‘Code Red’ caused White House administrators to change the IP address of the official White House website, and even penetrated Microsoft’s own IIS servers.
In 2001, ‘Code Red’ caused White House administrators to change the IP address of the official White House website, and even penetrated Microsoft’s own IIS servers.
Posted by Martijn Grooten on Jul 20, 2016
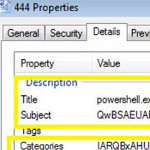 A new paper by FireEye researcher Ankit Anubhav provides an overview of evasion techniques applied by recently discovered malware.
A new paper by FireEye researcher Ankit Anubhav provides an overview of evasion techniques applied by recently discovered malware.
Posted by Virus Bulletin on Jul 15, 2016
 Recently, ESET researchers uncovered a new espionage toolkit targeting targeting Central and Eastern Europe. They provide some details in a guest post.
Recently, ESET researchers uncovered a new espionage toolkit targeting targeting Central and Eastern Europe. They provide some details in a guest post.
Posted by Martijn Grooten on Jul 8, 2016
 Anti-virus vendor Avast has announced the acquisition of its rival AVG for 1.3 billion US dollars.
Anti-virus vendor Avast has announced the acquisition of its rival AVG for 1.3 billion US dollars.
Posted by Helen Martin on Jul 7, 2016
 Passwords have long been a weak point in the security chain, despite efforts to encourage users to pick strong ones. 13 years ago, Martin Overton wrote an article highlighting the weakness and explaining why it is the human element that presents the biggest risk to computer security - something that rings as true today as it did 13 years ago.
Passwords have long been a weak point in the security chain, despite efforts to encourage users to pick strong ones. 13 years ago, Martin Overton wrote an article highlighting the weakness and explaining why it is the human element that presents the biggest risk to computer security - something that rings as true today as it did 13 years ago.