Posted by Martijn Grooten on Aug 22, 2019
 Researchers from the Czech Technical University in Prague will present a very comprehensive overview of the Machete APT group.
Researchers from the Czech Technical University in Prague will present a very comprehensive overview of the Machete APT group.
Posted by Martijn Grooten on Aug 19, 2019
 Last week, VB Editor Martijn Grooten travelled to the Kenyan capital Nairobi to speak at the 6th edition of the AfricaHackon event.
Last week, VB Editor Martijn Grooten travelled to the Kenyan capital Nairobi to speak at the 6th edition of the AfricaHackon event.
Posted by Martijn Grooten on Aug 5, 2019
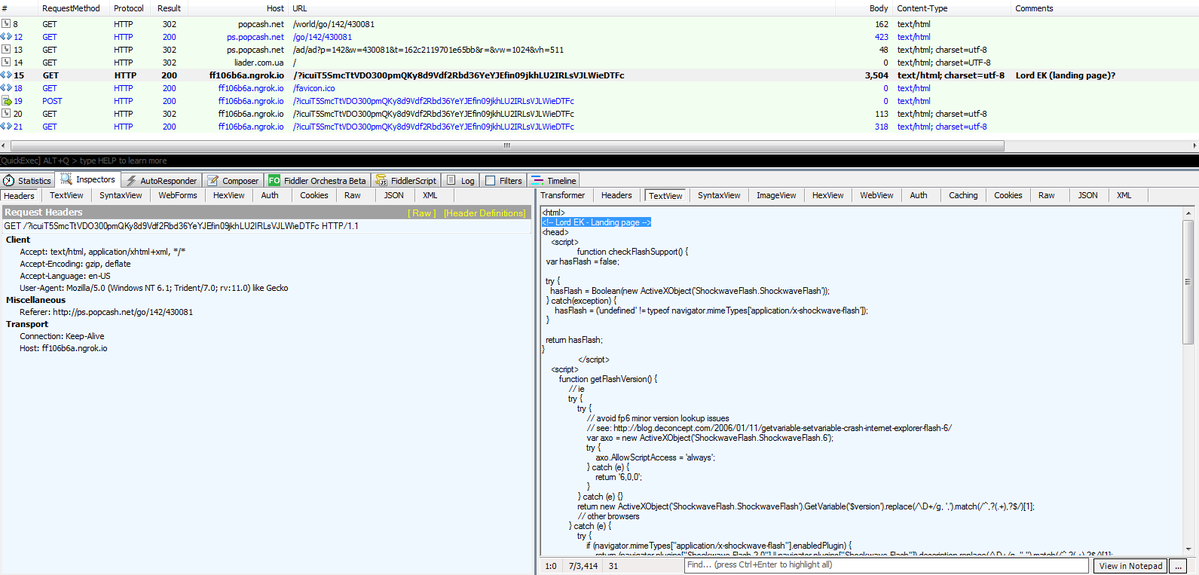 Still in-development kit thus far only targets Flash Player vulnerabilities
Still in-development kit thus far only targets Flash Player vulnerabilities
Posted by Martijn Grooten on Jul 29, 2019
 The call for last-minute papers for VB2019 is now open. Submit before 1 September to have your abstract considered for one of the nine slots reserved for 'hot' research.
The call for last-minute papers for VB2019 is now open. Submit before 1 September to have your abstract considered for one of the nine slots reserved for 'hot' research.
Posted by Martijn Grooten on Jul 4, 2019
 Virus Bulletin is seeking nominations for the sixth annual Péter Szőr Award.
Virus Bulletin is seeking nominations for the sixth annual Péter Szőr Award.
Posted by Martijn Grooten on Jun 25, 2019
 New additions to the VB2019 conference programme include a closing keynote address from Thinkst duo Haroon Meer and Adrian Sanabria and a talk on attacks against payment systems.
New additions to the VB2019 conference programme include a closing keynote address from Thinkst duo Haroon Meer and Adrian Sanabria and a talk on attacks against payment systems.
Posted by Martijn Grooten on Jun 21, 2019
 Virus Bulletin is excited to announce that, thanks to generous sponsorship from Google Android, we are able to offer 20 free tickets to students who want to attend VB2019.
Virus Bulletin is excited to announce that, thanks to generous sponsorship from Google Android, we are able to offer 20 free tickets to students who want to attend VB2019.
Posted by Martijn Grooten on Jun 4, 2019
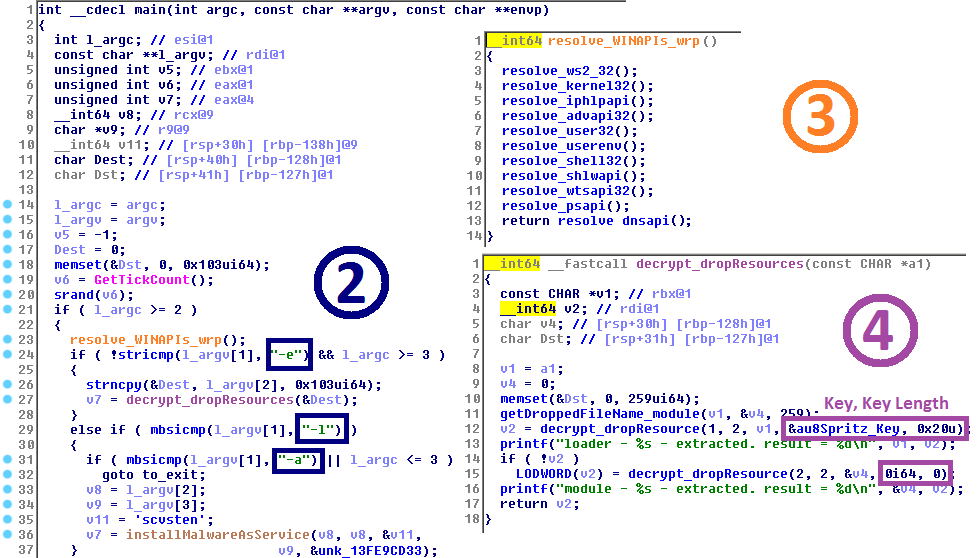 The Lazarus Group, generally linked to the North Korean government, is one of the most notorious threat groups seen in recent years. At VB2018 ESET researchers Peter Kálnai and Michal Poslušný presented a paper looking at the group's various campaigns. Today, we publish their paper and the recording of their presentation.
The Lazarus Group, generally linked to the North Korean government, is one of the most notorious threat groups seen in recent years. At VB2018 ESET researchers Peter Kálnai and Michal Poslušný presented a paper looking at the group's various campaigns. Today, we publish their paper and the recording of their presentation.
Posted by Virus Bulletin on May 29, 2019
 Virus Bulletin is proud to sponsor this year's BSides London conference, which will take place next week, and we have a number of tickets to give away.
Virus Bulletin is proud to sponsor this year's BSides London conference, which will take place next week, and we have a number of tickets to give away.
Posted by Virus Bulletin on May 15, 2019
 We are excited to announce the first 11 companies to partner with VB2019, whose support will help ensure a great event.
We are excited to announce the first 11 companies to partner with VB2019, whose support will help ensure a great event.