Many websites put barriers in front of visitors who use the Tor network. If we want to make the web more accessible through Tor, we need to be honest about why this is done, rather than cry wolf about a dislike for privacy, Martijn Grooten says.
If you regularly browse the web through the Tor network, you will have noticed that many websites are either inaccessible, or have strong barriers (in the form of difficult… https://www.virusbulletin.com/blog/2016/05/make-tor-work-better-web-we-need-be-honest-about-it/
A new paper by CYREN researcher Lordian Mosuela takes a close look at Gatak, or Stegoloader, a piece of malware that was discovered last year and that is controlled via malicious code embedded in a PNG image, a technique known as steganography.
Sometimes a picture says more than a thousand words. And sometimes in computer security, a picture contains a thousand words, or rather a lot of commands, used by malware authors… https://www.virusbulletin.com/blog/2016/04/paper-how-it-works-steganography-hides-malware-image-files/
We have announced 37 papers (and four reserve papers) that will be presented at VB2016 in Denver, Colorado, USA in October. Registration for the conference has opened; make sure you register before 1 July to benefit from a 10% early bird discount.
We are excited to officially announce the programme for VB2016, the 26th International Virus Bulletin Conference, which will take place in Denver, Colorado, USA 5-7 October this… https://www.virusbulletin.com/blog/2016/04/vb2016-programme-announced-registrations-opened/
The Virus Bulletin Virus Prevalence Table, which ran from 1992 until 2013, gave users a regular snapshot of what was really going on in the virus (and later malware) world, recording the number of incidents of each virus reported to VB in the preceding mo…
The Virus Bulletin Virus Prevalence Table, which ran from 1992 until 2013, gave users a regular snapshot of what was really going on in the virus (and later malware) world, each… https://www.virusbulletin.com/blog/2016/04/throwback-thursday-number-beasts1/
Word and Excel’s internal file formats used to be something in which few were interested – until macro viruses came along and changed all that. In 1996, Andrew Krukov provided an overview of the new breed of viruses.
Microsoft has recently introduced a new feature to Office 2016: the ability to block macros,in an attempt to curb the spread of macro malware, which is once again on the rise.… https://www.virusbulletin.com/blog/2016/03/throwback-thursday-beginning-was-word/
You have until the early hours (GMT) of Monday 21 March to submit an abstract for VB2016! The VB2016 programme will be announced in the first week of April.
If you read our blog or follow us on social media, you can't have missed the fact that the deadline for submissions for VB2016 is 18 March. That's today!
If you haven't… https://www.virusbulletin.com/blog/2016/03/vb2016-call-papers-deadline/
SHA-1 collisions may be found in the next few months, but that doesn't mean that fake SHA-1-based certificates will be created in the near future. Nevertheless, it is time for everyone, and those working in security in particular, to move away from outdat…
Earlier this month, I gave a talk entitled "How Broken Is Our Crypto Really?" at the RSA Conference in San Francisco. In the presentation, I looked at vulnerabilities found in… https://www.virusbulletin.com/blog/2016/03/how-broken-sha-1-really/
This Throwback Thursday we go back to 2004, when the entire crypto community was abuzz with the news that a group of Chinese researchers had demonstrated flaws in a whole set of hash functions - VB took a closer look to clarify the situation and draw less…
Just last week, VB Editor Martijn Grooten addressed an audience at the RSA Conference in San Francisco on the topic of cryptographic protocols that have supposedly been broken in… https://www.virusbulletin.com/blog/2016/03/throwback-thursday-hash-woes/
This Throwback Thursday VB heads back to 1996 when - long before the days of driveby downloads and exploit kits - VB published a report on the state of viruses on the Internet.
This Throwback Thursday VB heads back to 1996 when VB published a report on the state of viruses on the Internet.
In the mid-1990s, long before the days of driveby downloads… https://www.virusbulletin.com/blog/2016/02/throwback-thursday-viruses-internet-blog/
Next week, Virus Bulletin Editor Martijn Grooten will attend the RSA conference in San Francisco, where he will give a talk entitled "How Broken Is Our Crypto Really?" He will also speak at BSides San Francisco, where he will give a talk entitled "Ellipti…
Next week, almost everyone with a stake in or an opinion on IT security will be in San Francisco for the annual RSA Conference.
I will be there as well, and although Virus… https://www.virusbulletin.com/blog/2016/02/rsa-and-bsides-san-francisco/
 Researchers from the Czech Technical University in Prague will present a very comprehensive overview of the Machete APT group.
Researchers from the Czech Technical University in Prague will present a very comprehensive overview of the Machete APT group.
 Last week, VB Editor Martijn Grooten travelled to the Kenyan capital Nairobi to speak at the 6th edition of the AfricaHackon event.
Last week, VB Editor Martijn Grooten travelled to the Kenyan capital Nairobi to speak at the 6th edition of the AfricaHackon event.
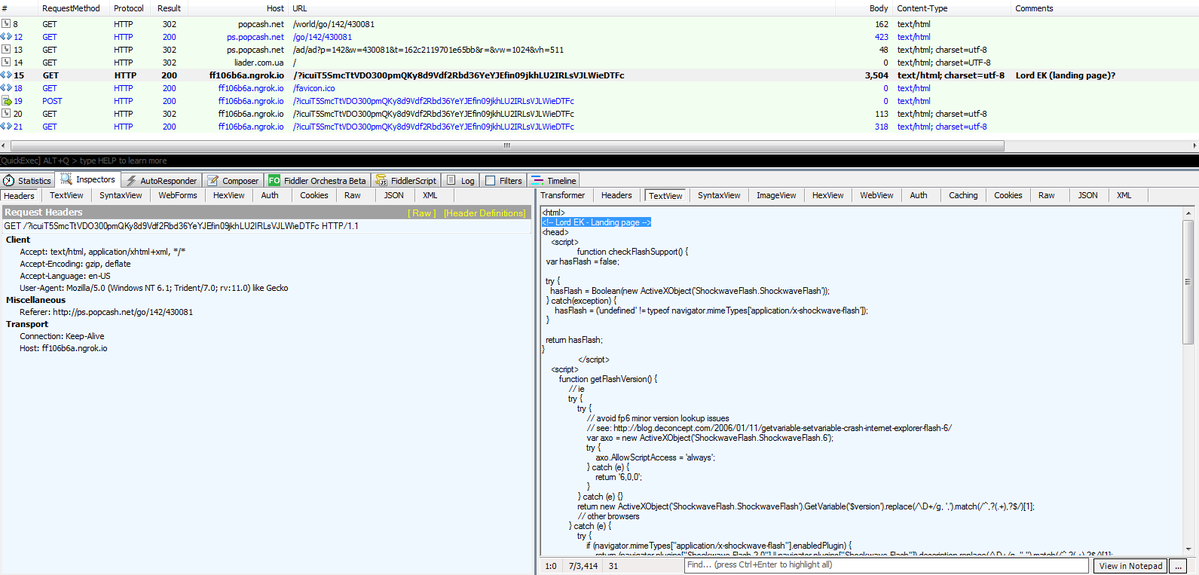 Still in-development kit thus far only targets Flash Player vulnerabilities
Still in-development kit thus far only targets Flash Player vulnerabilities
 The call for last-minute papers for VB2019 is now open. Submit before 1 September to have your abstract considered for one of the nine slots reserved for 'hot' research.
The call for last-minute papers for VB2019 is now open. Submit before 1 September to have your abstract considered for one of the nine slots reserved for 'hot' research.
 Virus Bulletin is seeking nominations for the sixth annual Péter Szőr Award.
Virus Bulletin is seeking nominations for the sixth annual Péter Szőr Award.
 New additions to the VB2019 conference programme include a closing keynote address from Thinkst duo Haroon Meer and Adrian Sanabria and a talk on attacks against payment systems.
New additions to the VB2019 conference programme include a closing keynote address from Thinkst duo Haroon Meer and Adrian Sanabria and a talk on attacks against payment systems.
 Virus Bulletin is excited to announce that, thanks to generous sponsorship from Google Android, we are able to offer 20 free tickets to students who want to attend VB2019.
Virus Bulletin is excited to announce that, thanks to generous sponsorship from Google Android, we are able to offer 20 free tickets to students who want to attend VB2019.
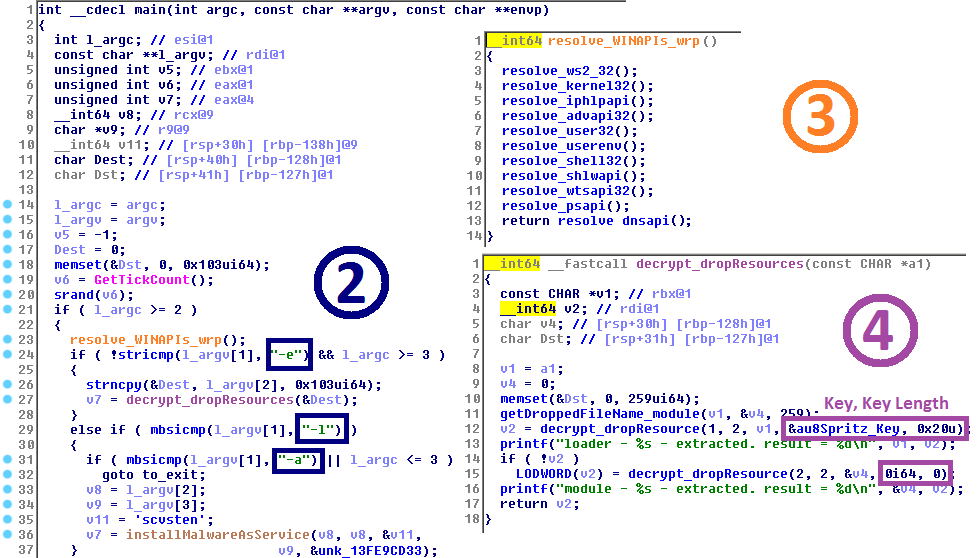 The Lazarus Group, generally linked to the North Korean government, is one of the most notorious threat groups seen in recent years. At VB2018 ESET researchers Peter Kálnai and Michal Poslušný presented a paper looking at the group's various campaigns. Today, we publish their paper and the recording of their presentation.
The Lazarus Group, generally linked to the North Korean government, is one of the most notorious threat groups seen in recent years. At VB2018 ESET researchers Peter Kálnai and Michal Poslušný presented a paper looking at the group's various campaigns. Today, we publish their paper and the recording of their presentation.
 Virus Bulletin is proud to sponsor this year's BSides London conference, which will take place next week, and we have a number of tickets to give away.
Virus Bulletin is proud to sponsor this year's BSides London conference, which will take place next week, and we have a number of tickets to give away.
 We are excited to announce the first 11 companies to partner with VB2019, whose support will help ensure a great event.
We are excited to announce the first 11 companies to partner with VB2019, whose support will help ensure a great event.