Posted by Virus Bulletin on Sep 16, 2019
 Security researcher Paul Baccas reviews Eddy Willems' book 'Cyberdanger'.
Security researcher Paul Baccas reviews Eddy Willems' book 'Cyberdanger'.
Posted by Martijn Grooten on Sep 13, 2019
 In the mini-summit, which forms part of VB2019 (the 29th Virus Bulletin International Conference), eight sessions will focus on all aspects of threat intelligence collecting, using and sharing.
In the mini-summit, which forms part of VB2019 (the 29th Virus Bulletin International Conference), eight sessions will focus on all aspects of threat intelligence collecting, using and sharing.
Posted by Virus Bulletin on Sep 12, 2019
 In a guest blog post by VB2019 Silver partner TotalAV, Matthew Curd, the software’s Technical Expert, considers the changes in the cybersecurity landscape.
In a guest blog post by VB2019 Silver partner TotalAV, Matthew Curd, the software’s Technical Expert, considers the changes in the cybersecurity landscape.
Posted by Virus Bulletin on Sep 4, 2019
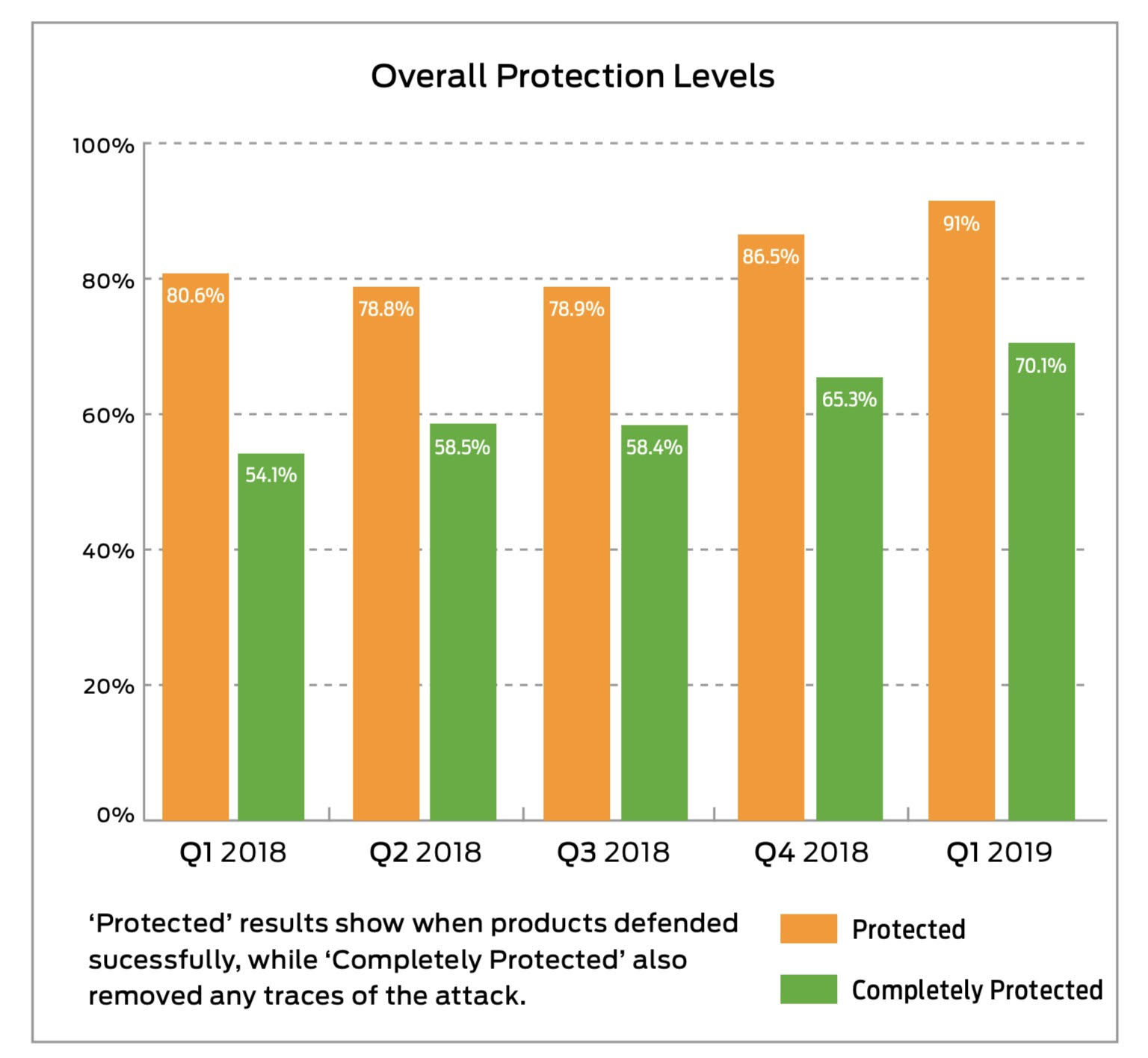 Over the last few years SE Labs has tested more than 50 different security products against over 5,000 targeted attacks. In this guest blog post Stefan Dumitrascu, Chief Technical Officer at SE Labs, looks at the different attack tools available, how effective they are at helping attackers bypass anti-malware products, and how security vendors have been handling this type of threat for over a year.
Over the last few years SE Labs has tested more than 50 different security products against over 5,000 targeted attacks. In this guest blog post Stefan Dumitrascu, Chief Technical Officer at SE Labs, looks at the different attack tools available, how effective they are at helping attackers bypass anti-malware products, and how security vendors have been handling this type of threat for over a year.
Posted by Martijn Grooten on Sep 3, 2019
 We preview the five Small Talks on the VB2019 programme in which important topics are discussed in a less formal atmosphere.
We preview the five Small Talks on the VB2019 programme in which important topics are discussed in a less formal atmosphere.
Posted by Martijn Grooten on Sep 2, 2019
 We preview the VB2019 paper by Endgame researcher Bobby Filar, who created a graph-based framework designed to detect malicious use of legitimate binaries through parent-child relationships.
We preview the VB2019 paper by Endgame researcher Bobby Filar, who created a graph-based framework designed to detect malicious use of legitimate binaries through parent-child relationships.
Posted by Martijn Grooten on Aug 30, 2019
 We preview the VB2019 paper by RiskIQ researcher Yonathan Klijnsma on the Magecart web skimming attacks.
We preview the VB2019 paper by RiskIQ researcher Yonathan Klijnsma on the Magecart web skimming attacks.
Posted by Martijn Grooten on Aug 29, 2019
 Your last chance to get a speaking slot on the VB2019 programme with a talk on hot research!
Your last chance to get a speaking slot on the VB2019 programme with a talk on hot research!
Posted by Martijn Grooten on Aug 29, 2019
 Record number of partner organisations for the Virus Bulletin Conference reflects very broad and international event.
Record number of partner organisations for the Virus Bulletin Conference reflects very broad and international event.
Posted by Martijn Grooten on Aug 26, 2019
 We preview the VB2019 paper by Sophos researcher Luca Nagy, who dives deeply into the notorious Emotet malware.
We preview the VB2019 paper by Sophos researcher Luca Nagy, who dives deeply into the notorious Emotet malware.