2010-04-01
Abstract
Terry Zink looks at the increasingly common phenomenon of hacktivism and details three recent cyber warfare attacks.
Copyright © 2010 Virus Bulletin
In 2010, the problem of botnets is apparent to everyone in the cyber security industry. Botnets are used to send spam, host fast flux domains, perform black search engine optimization, distribute viruses, and so forth. But the problem of botnets is not limited to the transmission of email.
In today’s world, hostilities between different nations may include cyber warfare and electronic espionage. Countries no longer need ‘merely’ to worry about physical attacks; they need to be concerned with attacks on their economic infrastructure. There are forms of cyber attack that can seriously cripple a country’s infrastructure and which are almost as severe as a physical attack – such as a DDoS attack [1] on a country’s banks, web servers, or root name servers.
However, while these cyber attacks are political in nature, they are not necessarily political in origin. It wouldn’t take a lot for someone who is ideologically driven, and who has the necessary connections, to talk to his friends in the botnet space and coordinate a full-scale cyber attack against a particular target. The result would be largely the same as if a government had done it. For example, Internet search giant Google recently suffered a cyber attack originating from China in which sensitive information was either targeted or stolen [2], yet – despite US Secretary of State Hillary Clinton intimating that the Chinese government ought to own up to the attack – it is not known whether it was state-sponsored or driven by a private individual (or group) with very powerful connections.
Was Secretary Clinton right to accuse China of state-sponsored theft of (American) corporations’ intellectual property? Or is it possible that there are individuals out there with the skills necessary to pull off such a sophisticated feat?
The term ‘hacktivism’ is an amalgamation of the words ‘hack’ and ‘activism’. It is defined as the non-violent use of illegal or legally ambiguous digital tools for political ends. Hacktivism is becoming increasingly common, and the complexity of these attacks makes it nearly impossible to determine whether they are state sponsored, or whether they have been perpetrated by an individual (or individuals) with access to an army of bots. The cost of technology has been driven down immensely thanks to Moore’s Law [3], but unfortunately this also allows those with malicious intent to do a great deal of damage.
Estonia is one of the most wired countries in eastern Europe. It relies on the Internet for a substantial portion of everyday life – communications, financial transactions, news, shopping and restaurant reservations to name just a few. Indeed, in 2000, the Estonian government declared Internet access a basic human right. It was this growing dependence on the Internet that left the country particularly vulnerable to a large-scale cyber attack in April 2007.
The attack is thought to have coincided with an event in downtown Tallinn. During the night of 26 April 2007, government workers relocated a Soviet-era monument commemorating World War II – ‘the Bronze Soldier’ – and also moved some war graves in downtown Talinn. This sparked protests from some 500 ethnic Russian Estonians. For the Kremlin – and Russians in general – such a move in a former Soviet republic was considered a grave insult.

By 10 p.m. local time on 27 April 2007, digital intruders had begun probing Estonian Internet networks, looking for weak points and marshalling resources for an all-out assault. Most of the attacks that affected the general public were DDoS-type attacks ranging from various low-tech methods like ping floods, to the rental of botnets usually involved in spam distribution. Spamming of the commentaries of bigger news portals and website defacements, including that of the Estonian Reform Party, also occurred. Once they gained control of the sites, hackers posted a fake letter from Estonian Prime Minister Andrus Ansip apologizing for ordering the removal of the monument.
This was a concerted cyber attack on Estonia. Some observers reckoned that the onslaught on the country was of a sophistication not seen before. The case was studied intensively by other countries and military planners.
A couple of days after the attacks began, networks and routers in Estonia were being pressed to their limits. Although not all servers were taken offline, the functionality of the Internet in the country was severely compromised. Security specialists erected firewalls and barriers but as time passed, these barriers started to break down. Eventually, the government started taking down sites and making them available only to users within Estonia. This was seen as a temporary fix – and although it worked for a country as small as Estonia, it would not have worked for a larger nation where the traffic is much more international.
Two weeks later, the cyber war on Estonia intensified. On 9 May – the date Russia celebrates victory over Germany in World War II – the scale of the attacks increased. More than 50 websites and servers may have been disabled at once, with a data stream crippling many other parts of the system. This continued until late in the evening of 10 May – which was perhaps when the rental of the botnets and the contracts with the cyber mercenaries expired. After 10 May, the attacks slowly decreased as Estonian authorities managed to take botnets offline by working with phone companies and ISPs to trace the IP addresses of attacking computers and shut down their connections.
Many of the computers used in the attacks were traced back to machines in Russian government offices. At the time, the Estonian Foreign Minister accused the Kremlin of direct involvement in the attacks. However, Estonia’s defence minister later admitted that he had no evidence linking the attacks to Russian authorities. What could not be determined was whether the computers involved were simply ‘zombie’ machines that had been hijacked by bots and which were not under the control of the Russian government, or whether they were actively being used and controlled by government personnel.
So who was responsible? At the time, Dmitry Peskov, the Kremlin’s chief spokesman, told the BBC’s Russian Service there was ‘no way the [Russian] state [could] be involved in cyber terrorism’ [4]. Two years later, in a panel discussion between Russian and American experts on information warfare in the 21st century, Russian State Duma politician Sergei Markov claimed that his assistant was responsible. According to Markov, his aide (who he did not name) had decided that ‘something bad had to be done to these fascists’ [5]. In other interviews in 2009, Konstantin Goloskokov, a ‘commissar’ of pro-Russian youth movement Nashi, claimed responsibility for the attacks [6]. Goloskokov had been in his early 20s and working as an aide to Sergei Markov when he carried out the attacks, and he claims no regrets. While stressing that the Russian state had no involvement, he said he believed that the Internet represented the most effective weapon to avenge what he saw as a grave national insult [7].
Essentially, the Estonian attacks were a cyber riot: someone with some serious connections in the world of botnets decided to teach the government (of another country) a lesson – and nearly brought the country to a standstill in the process.
Estonia was particularly vulnerable to this type of attack, but the lesson is clear for the broader developed world. A concerted effort made by either a government or a person (or group of people) with a grudge or political agenda can wreak serious havoc on a country’s economy. It is clear that, if Goloskokov’s claims are true, one need not have state sponsorship in order to launch a crippling cyber attack.
A year later, a war in Central Asia was preceded by a cyber attack on a nation’s infrastructure. The incident was the 2008 South Ossetia War, also known as the Russia-Georgia War [8].
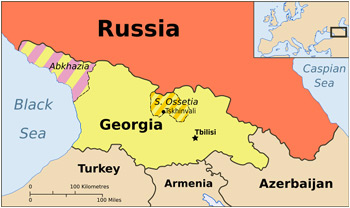
The 1991–1992 South Ossetia War between Georgians and Ossetians left most of South Ossetia under de facto control of a Russian-backed, internationally unrecognized government. In 2004, the Georgian government embarked on a movement to retake South Ossetia. Whereas previously Russia had only sought to maintain the status-quo, a brief battle in 2004 became a turning point for its policy in the region. Russia now felt that the security of the whole Caucasus region depended on the situation in South Ossetia, and took the side of the self-proclaimed republic. During 2008, both Georgia and Russia accused each other of preparing for war, and in August 2008 Georgia invaded South Ossetia and Russia invaded in response, ultimately forcing Georgia to withdraw.
Against this background of military force, Georgia, like Estonia a year before it, had been the victim of a large-scale cyber attack. Two and a half weeks prior to the military action, the website of Georgian president Mikheil Saakashvili was the target of a DDoS attack and was knocked offline for more than 24 hours. A command-and-control (C&C) centre had taken aim at the site and flooded it with TCP, ICMP and HTTP requests. Three days before the invasion, the website for the South Ossetian OSInform News Agency was hacked and replaced with a feed from Alania TV, a Georgian TV station aimed at television audiences in South Ossetia (Alania TV later denied any involvement) [9].
In the lead-up to the conflict, there had been much activity on several Russian chat forums. This culminated in a series of coordinated cyber attacks against Georgia’s Internet infrastructure. Several government websites were hacked and defaced, and more government sites were flooded in DDoS attacks and knocked offline. In response, the government was forced to relocate the servers to the United States, and the Georgian Ministry of Foreign Affairs resorted to using a Google Blogspot account to release information. Perhaps not so coincidentally, the date of the cyber attacks corresponded to the escalation of the military conflict.
Both public and private sector websites were attacked, including the following:
The Ministry of Education and Science in Georgia
The Parliament of Georgia
The President of the Republic of Georgia
Georgia’s largest commercial bank
The Association Press
A private television company
Those responsible for the attack were not particularly secretive. In the time leading up to the attacks, several Russian chat forums carried lists of which government websites to target. Tools for carrying out DoS attacks were provided for download along with instructions on how to flood the Georgian websites. Lists of other Georgian sites that were known to be vulnerable to attack were also distributed. In other words, people were openly plotting to make a move against the Georgian government and making the necessary tools publicly available.
While the timing of the cyber attacks immediately prior to the Russian military intervention does seem almost too convenient not to have been coordinated by the government, it makes no sense for the government to plot their cyber war in plain sight. While the timing is suspicious, we must be careful not to mistake coincidence for conspiracy. A group of pro-nationalists with access to botnets can choose to do a lot of damage if they put their botnets together.
One of my top ten spam stories of the year 2009 (see VB, January 2010, p.11) was that of Twitter suffering a DDoS attack. On 7 August the social networking site was hit hard enough to be taken down for several hours. Other social networking sites including Facebook, LiveJournal, YouTube and Blogger were also hit.
The attacks occurred close to the first anniversary of the Russia-Georgia war. A brief investigation revealed that a targeted attack had been launched against pro-Georgian blogger ‘Cyxymu’ who had accounts on each of the social networking services involved. Cyxymu, who posted extensively on the suffering of Georgian civilians during and after the war in Abkhazia, accused Russian authorities of trying to silence him using cyber attacks.
We still don’t know exactly what happened, who was behind the attacks, or the reason for them, but we can speculate and use historical precedent to come up with a reasonable theory.
The attacks against the social networking sites coincided with a very large spam run. The messages in this spam run all contained links to Cyxymu’s pages at Blogger, Facebook, LiveJournal, and so on. One theory is that Cyxymu was responsible for the spam run, and when people all across the Internet received the spam in their inboxes, they all started clicking on the links in the messages, driving piles of traffic to the sites. With so many people checking out Cyxymu’s pages, Twitter, Facebook, et al. couldn’t handle the load and shut down. In other words, the shutdown of the sites was an accident – Cyxymu was too good at proclaiming his message to the world.
Yet this theory is fraught with problems. First, a spam run like this would have to get past spam filtering services. It is not easy to bypass filters with only a handful of links before they get added to URL blocklists. Secondly, few users, if any, actually click on links in spam messages – particularly politically charged messages. There simply wouldn’t have been enough traffic generated to take a site down. Several hundred thousand users would have had to access the pages simultaneously, which would have required the sending of several hundred million spam messages. No offence to Cyxymu, but it’s unlikely that he single-handedly built the infrastructure necessary to send out enough spam in such a short time frame to bring down Twitter. It doesn’t mesh well with what we know about the more sophisticated spamming operations that are in effect today.
A more credible theory is that the spam run was used as a cover. Certain pro-Russians were well aware that Cyxymu was preaching his message on the various social networking websites, and decided that something had to be done to stop him. The attackers had botnets under their control which flooded the sites with DoS attacks and took them offline. The fact that all the sites were taken down at around the same time indicates that this was a coordinated attack – this was not the result of people clicking on links in their spam email. This theory makes a great deal more sense since a targeted flood of ping requests is much easier to achieve using a botnet than relying on users to click on links in spam messages.
Yet if this was the case, what was the purpose of the spam run with links to Cyxymu’s pages? The organizers of the attack were attempting to discredit Cyxymu by making it look as if he was responsible for sending out a huge wave of spam advertising his pages. The attackers assumed that, when word got back to Facebook or Twitter that Cyxymu was spamming the rest of the world to drive traffic to their sites, they would see this as violating their Terms of Service and shut down his account. In other words, it was all a set-up; the attackers were attempting to frame him.
While containing some outlandish elements, the second theory is more credible than the first.
Who was behind the attack? Was it the Russian government? Did they engage in state sponsorship of cyber warfare? While it is possible that Russian authorities were involved, the attack follows a similar pattern to that of the previous two cases:
The Estonian government was attacked by a pro-Russian independent player who claims to have been acting on his own behalf. This was sparked by what he saw as anti-Russian actions and was an attempt to ‘make Estonia pay’.
The Georgian government was (allegedly) attacked by a pro-Russian group or player, acting on their own behalf. This was sparked by what they saw as anti-Russian actions and was an attempt to ‘make Georgia pay’.
A number of social networking sites including Twitter, Facebook and LiveJournal were attacked by a pro-Russian group or player (one of which might have been the government). The attacks were sparked by what they saw as anti-Russian actions and were an attempt to ‘make the blogger pay’.
The Russian government would have no need to get involved in matters like this because there are enough people out there who are sufficiently well connected in the malware space to launch sophisticated botnet attacks without state involvement. No doubt, some states may be pleased to see their opponents suffering from such sophisticated attacks, but they can plausibly deny any involvement. Malware and botnets have uses other than sending out spam and pushing fake pills.
This is the difficulty when it comes to cyber warfare – state sponsorship is not required in order to launch attacks on other states. The face of warfare has evolved to include cyber riots, and those who are vulnerable are at risk even if the respective governments do not intend to actually attack each other.
In the movies, we sometimes see hackers breaking into government systems or private corporations. These types of actions, while entertaining, used not to be realistic. Individual players acting on their own behalf didn’t have the necessary resources to cripple a nation’s infrastructure or pilfer a company’s covert information.
Yet, as the cost of technology has fallen and botnets have proliferated, it has become much easier to accomplish these tasks. Foreign governments don’t need to conduct cyber warfare, private citizens will do the job for them. We already have three examples of this.
And that brings us back to the issue of the attacks on Google. Who was responsible? Was it the government of China? Was it someone trying to steal information from Google and give it to a competitor? I don’t know the answer, but neither of the above would surprise me.
[1] A denial-of-service (DoS) attack or a distributed denial-of-service (DDoS) attack is an attempt to make a computer resource unavailable to its intended users. Although the means to carry out, motives for, and targets of a DoS attack may vary, it generally consists of the concerted efforts of a person or people to prevent an Internet site or service from functioning efficiently or at all, temporarily or indefinitely, see http://en.wikipedia.org/w/index.php?title=Denial-of-service_attack&oldid=349367424.
[8] Wikipedia has a good summary of the timeline of the war: http://en.wikipedia.org/w/index.php?title=Timeline_of_the_2008_South_Ossetia_war&oldid=346178264.
[9] For a full analysis of the Georgia cyber attacks, see CCDCOE’s report at http://www.carlisle.army.mil/DIME/documents/Georgia%201%200.pdf.