Posted by Martijn Grooten on Sep 9, 2016
 At VB2016, four researcher from Bitdefender will present a paper in which they look at vulnerabilities in four "smart" power outlets.
At VB2016, four researcher from Bitdefender will present a paper in which they look at vulnerabilities in four "smart" power outlets.
Posted by Martijn Grooten on Sep 7, 2016
 Malvertising, in which legitimate ad networks are abused to silently infect users with malware, has become a real plague in recent years. A VB2016 paper by Malwarebytes researchers Jérôme Segura and Chris Boyd will look at the issue.
Malvertising, in which legitimate ad networks are abused to silently infect users with malware, has become a real plague in recent years. A VB2016 paper by Malwarebytes researchers Jérôme Segura and Chris Boyd will look at the issue.
Posted by Martijn Grooten on Sep 6, 2016
 Many people have already registered for VB2016 and the conference hotel is rapidly filling up - registration for the event will remain open right up until the start of the conference, but here, we provide some advice about booking accommodation.
Many people have already registered for VB2016 and the conference hotel is rapidly filling up - registration for the event will remain open right up until the start of the conference, but here, we provide some advice about booking accommodation.
Posted by Martijn Grooten on Sep 6, 2016
 At VB2016, Cylance researcher Brian Wallace will reveal a multi-platform tool that runs on the endpoint and uses various techniques to detect ongoing man-in-the-middle attacks.
At VB2016, Cylance researcher Brian Wallace will reveal a multi-platform tool that runs on the endpoint and uses various techniques to detect ongoing man-in-the-middle attacks.
Posted by Martijn Grooten on Sep 5, 2016
 More than a dozen companies and organizations are lending their support to VB2016 as conference sponsors and supporting organizations.
More than a dozen companies and organizations are lending their support to VB2016 as conference sponsors and supporting organizations.
Posted by Virus Bulletin on Sep 2, 2016
In a guest blog, Webroot researcher Jesse Lopez looks at another variant in the massive crop of malware that takes users’ files hostage: Nemucod ransomware.
Read morePosted by Martijn Grooten on Sep 1, 2016
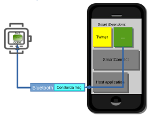 At VB2016 in Denver, Fortinet researcher Axelle Apvrille will discuss how analysing a device's complementary mobile app can help a great deal in understanding the architecture of a smart device.
At VB2016 in Denver, Fortinet researcher Axelle Apvrille will discuss how analysing a device's complementary mobile app can help a great deal in understanding the architecture of a smart device.
Posted by Martijn Grooten on Aug 31, 2016
 Full technical details of the first in-the-wild Android app 'collusion' attack, where multiple apps perform an attack in collaboration, will be shared with the public in
at VB2016 in Denver on 5 October.
Full technical details of the first in-the-wild Android app 'collusion' attack, where multiple apps perform an attack in collaboration, will be shared with the public in
at VB2016 in Denver on 5 October.
Posted by Martijn Grooten on Aug 26, 2016
 Following their success last year, this year a series of "Small Talks" return to the VB2016 conference programme. We are pleased to announce the details of six of these talks, covering subjects that range from the Chinese cybercriminal underground to Android security, the Tor Project, and exploit kits.
Following their success last year, this year a series of "Small Talks" return to the VB2016 conference programme. We are pleased to announce the details of six of these talks, covering subjects that range from the Chinese cybercriminal underground to Android security, the Tor Project, and exploit kits.
Posted by Martijn Grooten on Aug 24, 2016
 Research by Virus Bulletin, in which five web security products were served 54 live exploit kits, shows that the products blocked between 87 and 100 per cent of the kits.
Research by Virus Bulletin, in which five web security products were served 54 live exploit kits, shows that the products blocked between 87 and 100 per cent of the kits.