Posted by Virus Bulletin on Feb 11, 2020
 Attor is a newly discovered cyber-espionage platform, use of which dates back to at least 2014 and which focuses on diplomatic missions and governmental institutions. Details of Attor were presented at VB2019 in London by ESET researcher Zuzana Hromcová. Today we release the recording of Zuzana's presentation.
Attor is a newly discovered cyber-espionage platform, use of which dates back to at least 2014 and which focuses on diplomatic missions and governmental institutions. Details of Attor were presented at VB2019 in London by ESET researcher Zuzana Hromcová. Today we release the recording of Zuzana's presentation.
Posted by Virus Bulletin on Feb 6, 2020
 With the call for papers for VB2020 currently open, we explain why, whether you've never presented before or you're a conference circuit veteran, if you have some interesting research to share with the community we want to hear from you!
With the call for papers for VB2020 currently open, we explain why, whether you've never presented before or you're a conference circuit veteran, if you have some interesting research to share with the community we want to hear from you!
Posted by Helen Martin on Feb 5, 2020
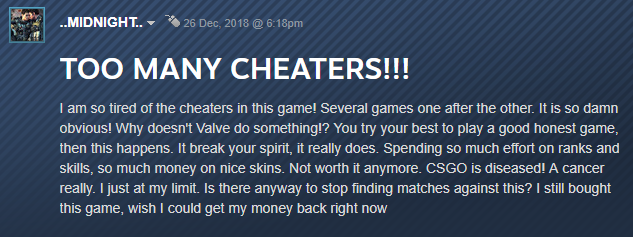 At VB2019 in London, Kaspersky researcher Santiago Pontiroli presented a paper on the growing illegal economy around video game cheats and its parallels with the malware industry. Today we publish both Santiago's paper and the recording of his presentation.
At VB2019 in London, Kaspersky researcher Santiago Pontiroli presented a paper on the growing illegal economy around video game cheats and its parallels with the malware industry. Today we publish both Santiago's paper and the recording of his presentation.
Posted by Virus Bulletin on Jan 31, 2020
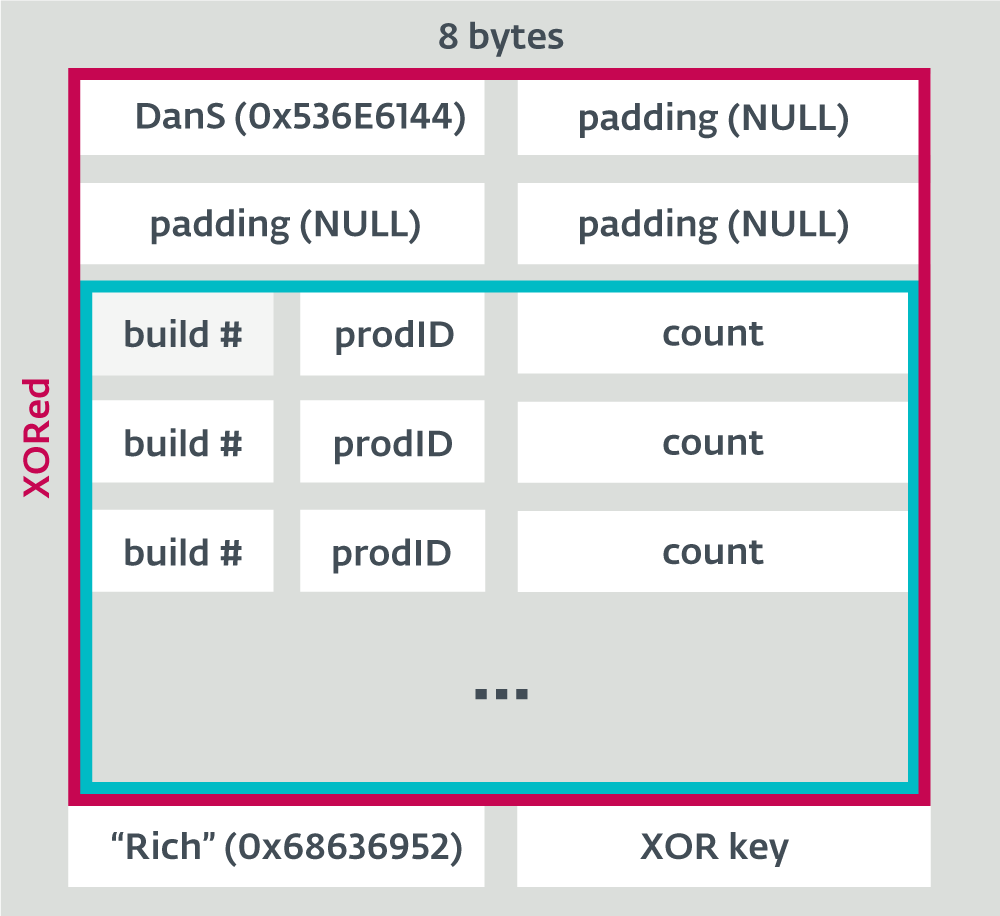 In a paper presented at VB2019 in London, ESET researchers Peter Kálnai and Michal Poslušný discussed the subject of rich headers and how it can be useful in malware research. Today we publish both their paper and the recording of their presentation.
In a paper presented at VB2019 in London, ESET researchers Peter Kálnai and Michal Poslušný discussed the subject of rich headers and how it can be useful in malware research. Today we publish both their paper and the recording of their presentation.
Posted by Helen Martin on Jan 28, 2020
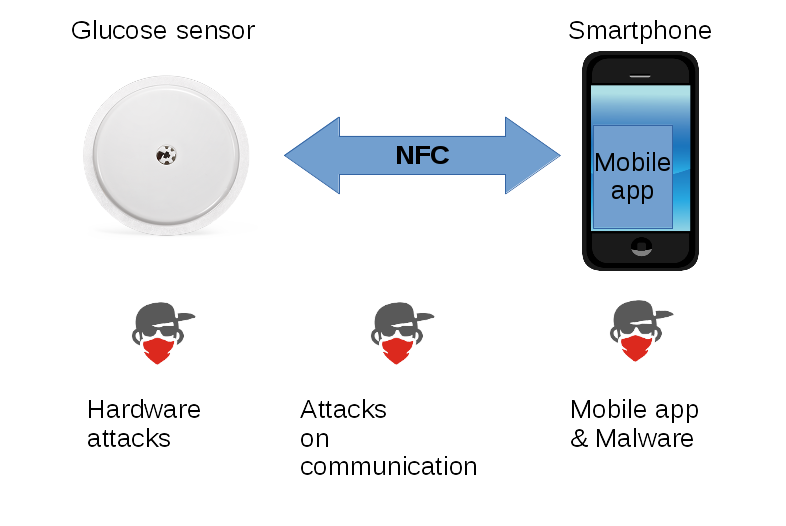 At VB2019 in London, Fortinet researcher Axelle Apvrille presented a paper co-written with Aamir Lakhani that looked at the threats faced by those who use medical IoT devices to help manage their diabetes. Today we publish the researchers' paper, as well as the recording of Axelle's presentation.
At VB2019 in London, Fortinet researcher Axelle Apvrille presented a paper co-written with Aamir Lakhani that looked at the threats faced by those who use medical IoT devices to help manage their diabetes. Today we publish the researchers' paper, as well as the recording of Axelle's presentation.
Posted by Virus Bulletin on Jan 24, 2020
 In a VB2019 paper Avast researchers Jan Sirmer, Luigino Camastra and Adolf Středa revealed full details of the Rietspoof malware. Today we publish their paper and the recording of the presentation given by Jan and Luigino in London.
In a VB2019 paper Avast researchers Jan Sirmer, Luigino Camastra and Adolf Středa revealed full details of the Rietspoof malware. Today we publish their paper and the recording of the presentation given by Jan and Luigino in London.
Posted by Helen Martin on Jan 20, 2020
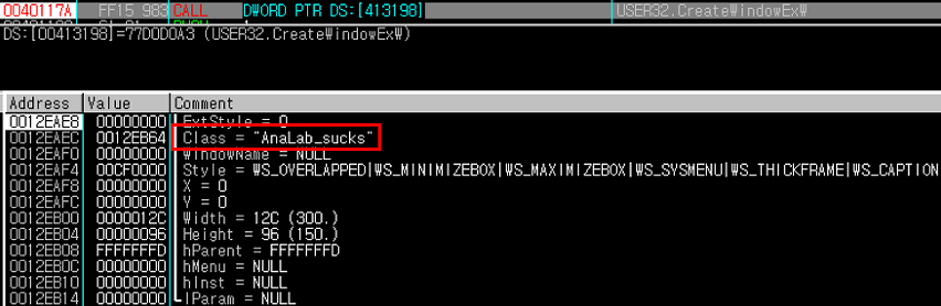 The GandCrab ransomware regularly updated itself to newer versions to stay ahead of decryptors released by security researchers, and regularly included taunts, jokes and references to security organizations in its code. In a new paper, the AhnLab Security Analysis Team reveal the full details of the battle that went on between GandCrab and AhnLab.
The GandCrab ransomware regularly updated itself to newer versions to stay ahead of decryptors released by security researchers, and regularly included taunts, jokes and references to security organizations in its code. In a new paper, the AhnLab Security Analysis Team reveal the full details of the battle that went on between GandCrab and AhnLab.
Posted by Virus Bulletin on Jan 16, 2020
 At VB2019 Juan Andres Guerrero-Saade looked at nation-state actors using threat intelligence for victim deconfliction. Today we publish both his paper and the recording of his presentation.
At VB2019 Juan Andres Guerrero-Saade looked at nation-state actors using threat intelligence for victim deconfliction. Today we publish both his paper and the recording of his presentation.
Posted by Virus Bulletin on Jan 14, 2020
 With the VB2020 Call for Papers now open, we explain how the selection procedure works, which may help you during your abstract submission.
With the VB2020 Call for Papers now open, we explain how the selection procedure works, which may help you during your abstract submission.
Posted by Virus Bulletin on Jan 13, 2020
 In 2019 we saw a rise in the number of targeted malware infections spread via ISPs and service providers. In a last-minute paper presented at VB2019 in London, Kaspersky researcher Denis Legezo discussed the details of a number of such cases. Today we release the recording of Denis' presentation.
In 2019 we saw a rise in the number of targeted malware infections spread via ISPs and service providers. In a last-minute paper presented at VB2019 in London, Kaspersky researcher Denis Legezo discussed the details of a number of such cases. Today we release the recording of Denis' presentation.