Posted by Martijn Grooten on Jul 16, 2018
 It is likely that, by now, everyone in computer science has at least heard of the Spectre attack, and many excellent explanations of the attack already exist. But what is the likelihood of finding Spectre being exploited on Android smartphones?
It is likely that, by now, everyone in computer science has at least heard of the Spectre attack, and many excellent explanations of the attack already exist. But what is the likelihood of finding Spectre being exploited on Android smartphones?
Posted by Martijn Grooten on Jul 11, 2018
 We are excited to announce several more companies that have partnered with VB2018.
We are excited to announce several more companies that have partnered with VB2018.
Posted by Martijn Grooten on Jul 10, 2018
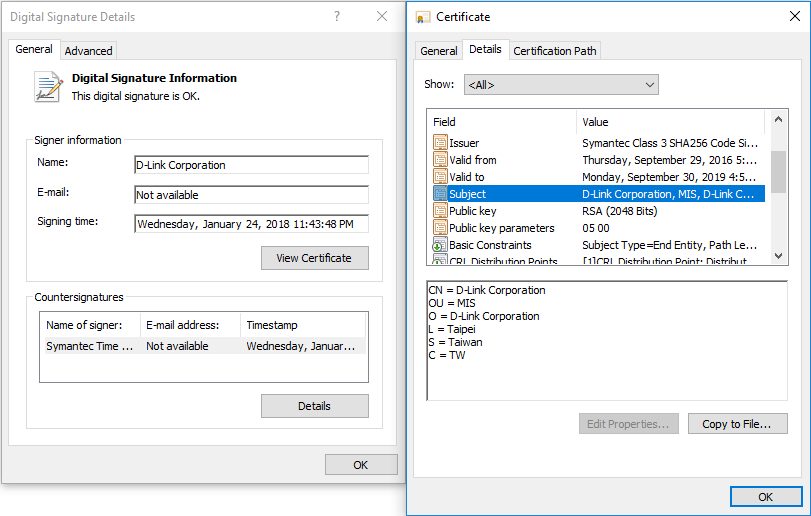 A new malware campaign that uses two stolen code-signing certificates shows that such certificates continue to be popular among malware authors. But there is a positive side to malware authors' use of stolen certificates.
A new malware campaign that uses two stolen code-signing certificates shows that such certificates continue to be popular among malware authors. But there is a positive side to malware authors' use of stolen certificates.
Posted by Martijn Grooten on Jul 6, 2018
 Though the location will remain under wraps for a few more months, we are pleased to announce the dates for VB2019, the 29th Virus Bulletin International Conference.
Though the location will remain under wraps for a few more months, we are pleased to announce the dates for VB2019, the 29th Virus Bulletin International Conference.
Posted by Martijn Grooten on Jul 6, 2018
The operators of the Necurs botnet, best known for being one of the most prolific spam botnets of the past few years, have pushed out updates to its client, which provide some important lessons about why malware infections matter.
Read morePosted by Martijn Grooten on Jul 3, 2018
 Virus Bulletin has opened nominations for the fifth annual Péter Szőr Award, for the best piece of technical security research published between 1 July 2017 and 30 June 2018.
Virus Bulletin has opened nominations for the fifth annual Péter Szőr Award, for the best piece of technical security research published between 1 July 2017 and 30 June 2018.
Posted by Martijn Grooten on Jul 3, 2018
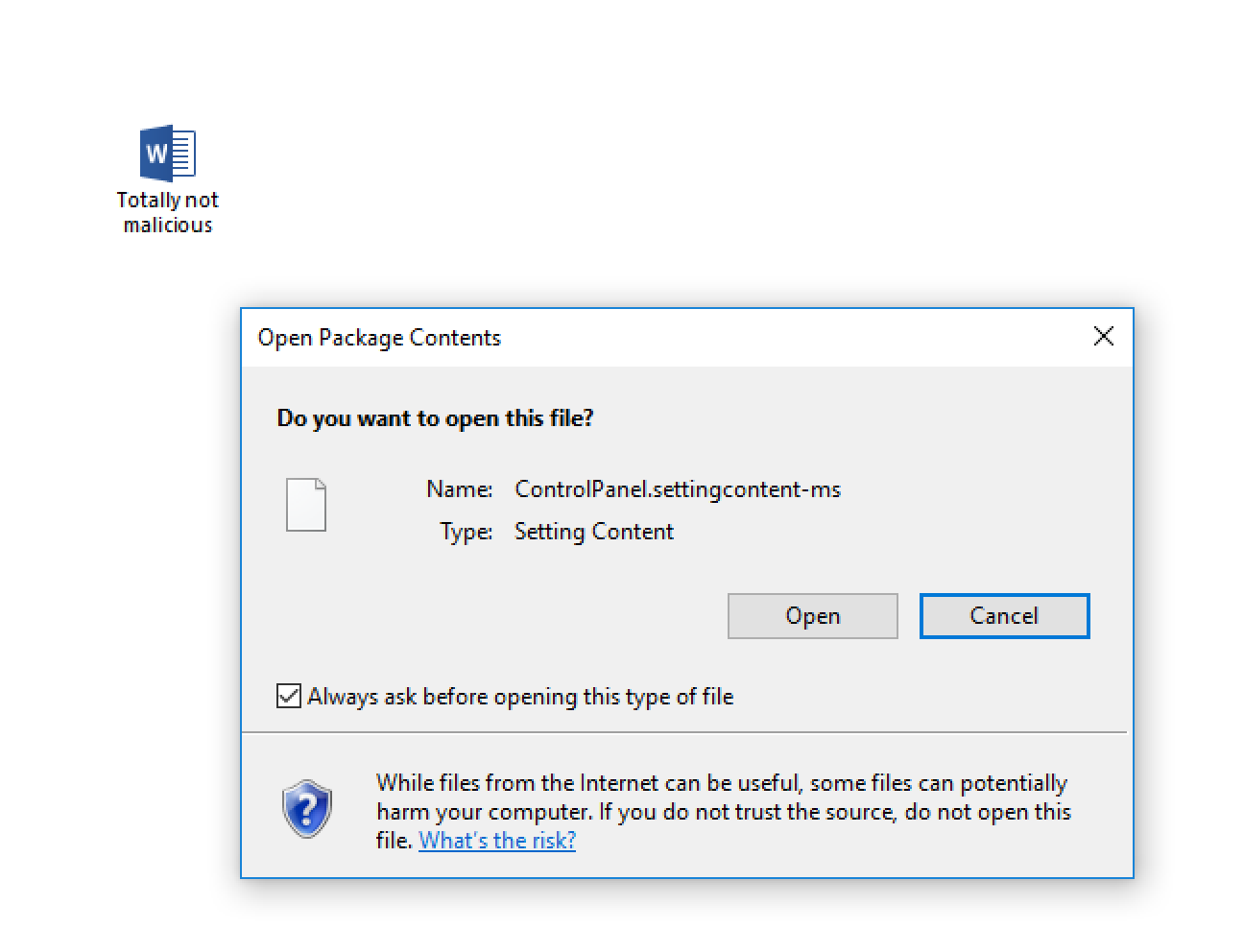 Security researcher Matt Nelson has discovered how .SettingContent-ms files can be embedded into Office files to deliver malware.
Security researcher Matt Nelson has discovered how .SettingContent-ms files can be embedded into Office files to deliver malware.
Posted by Martijn Grooten on Jun 26, 2018
 The New York Times reports that smart home devices are increasingly used in cases of domestic abuse.
The New York Times reports that smart home devices are increasingly used in cases of domestic abuse.
Posted by Martijn Grooten on Jun 25, 2018
 If you want to come to VB2018 in Montreal this year (and why wouldn't you?) and want to save a bit on the ticket price (and why wouldn't you?), remember that early bird discounts will be available until 30 June.
If you want to come to VB2018 in Montreal this year (and why wouldn't you?) and want to save a bit on the ticket price (and why wouldn't you?), remember that early bird discounts will be available until 30 June.
Posted by Martijn Grooten on Jun 21, 2018
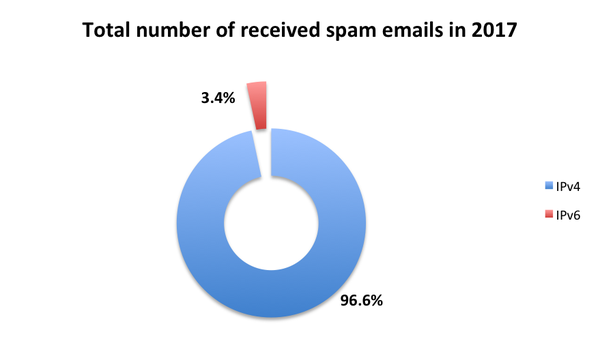 Though IPv6 is gradually replacing IPv4 on the Internet's network layer, email is lagging behind, the difficulty in blocking spam sent over IPv6 cited as a reason not to move. But would we really have such a hard time blocking spam sent over IPv6?
Though IPv6 is gradually replacing IPv4 on the Internet's network layer, email is lagging behind, the difficulty in blocking spam sent over IPv6 cited as a reason not to move. But would we really have such a hard time blocking spam sent over IPv6?