Posted by Martijn Grooten on Dec 18, 2019
 Today we publish the VB2019 paper by Anurag Shandilya (K7 Computing) who looked at recent malware attacks against routers, as well as the video of his presentation in London.
Today we publish the VB2019 paper by Anurag Shandilya (K7 Computing) who looked at recent malware attacks against routers, as well as the video of his presentation in London.
Posted by Martijn Grooten on Dec 17, 2019
 In the first of a five-part series of blog post, departing VB Editor Martijn Grooten explains why he believes cybersecurity isn't as much as technical field as we like to believe.
In the first of a five-part series of blog post, departing VB Editor Martijn Grooten explains why he believes cybersecurity isn't as much as technical field as we like to believe.
Posted by Martijn Grooten on Dec 16, 2019
 Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2020 is now open and we want to hear from you!
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2020 is now open and we want to hear from you!
Posted by Martijn Grooten on Dec 13, 2019
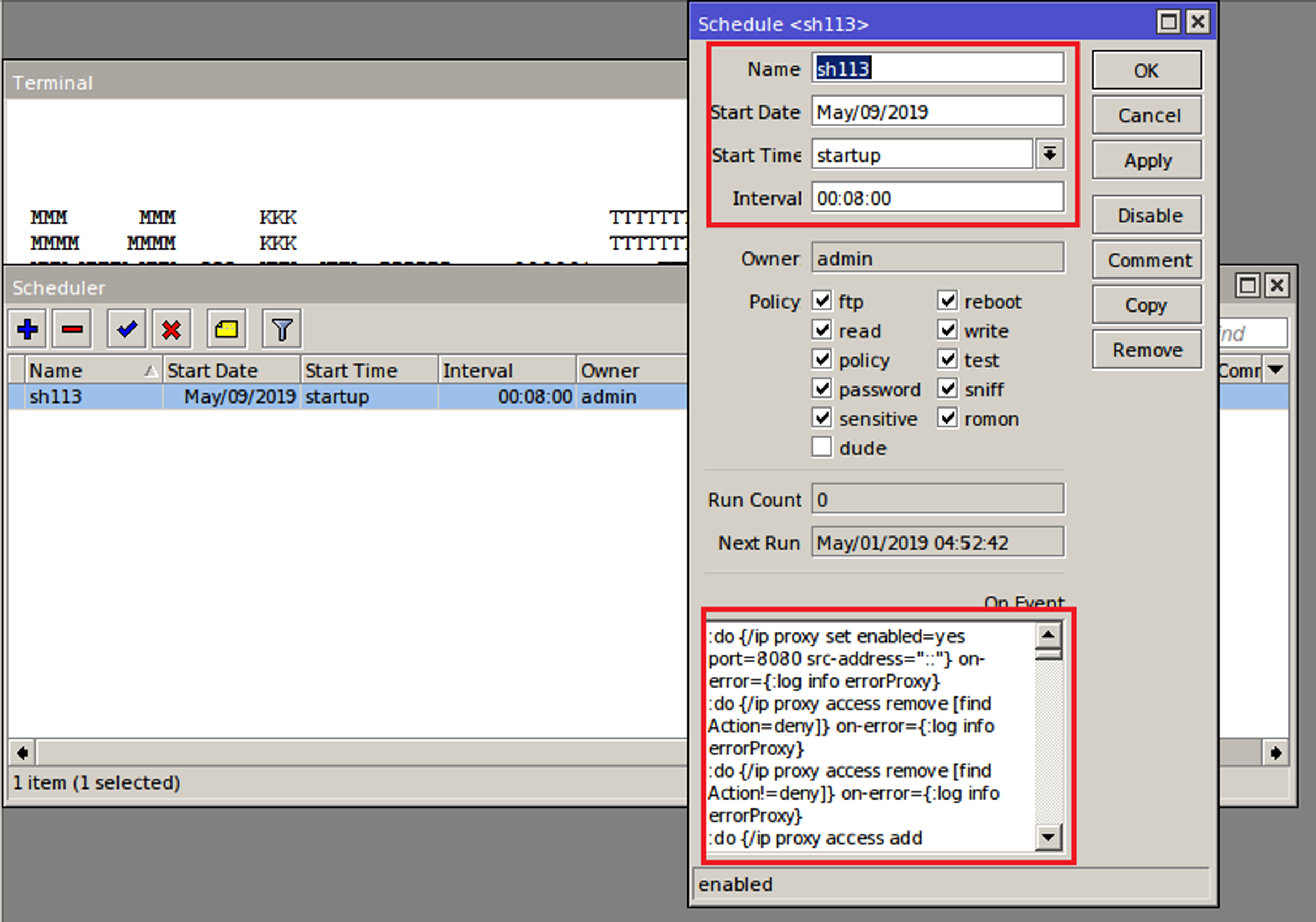
Today we publish the VB2019 paper by Cybereason researchers Mor Levi, Amit Serper and Assaf Dahan on Operation Soft Cell, a targeted attack against telecom providers around the world.
Read morePosted by Martijn Grooten on Dec 10, 2019
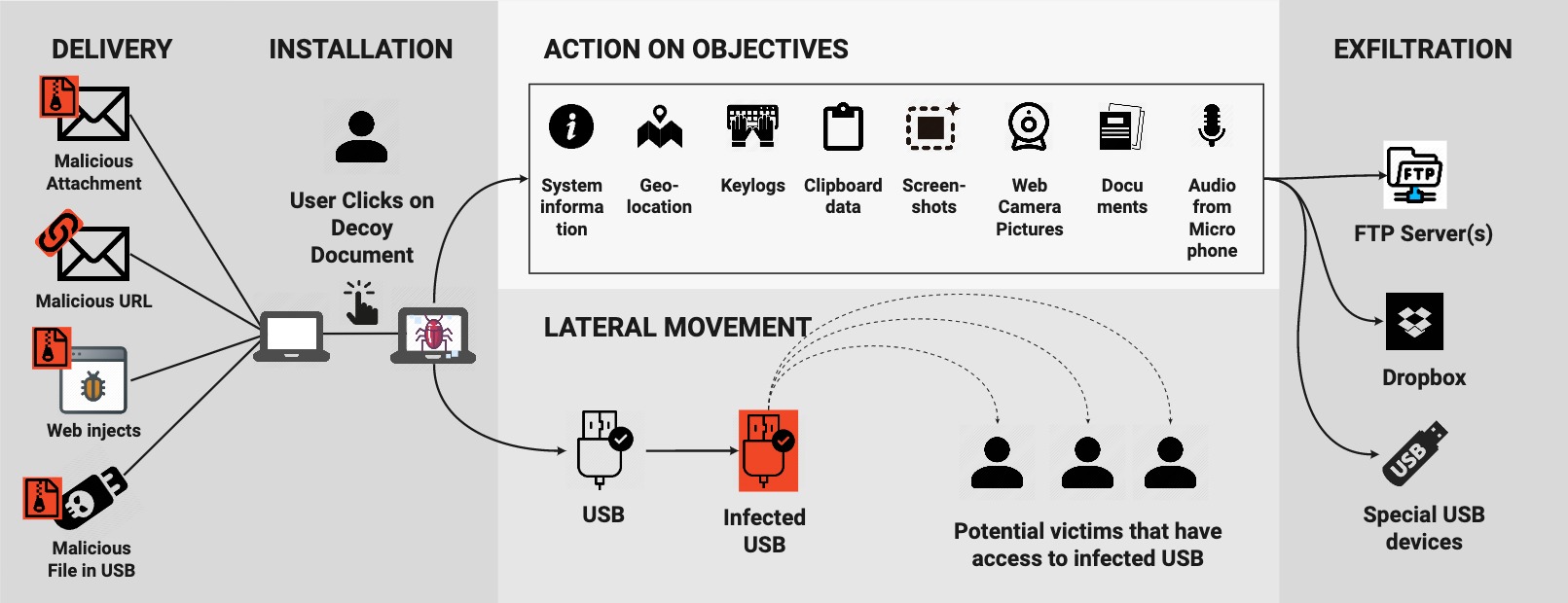 At VB2019 in London a group of researchers from the Stratosphere Lab at the Czech Technical University in Prague presented a paper in which they analysed and dissected the cyber espionage activities of an APT group in Latin America through the analysis of one of its tools, known as Machete. Today we publish their paper and the recording of their presentation.
At VB2019 in London a group of researchers from the Stratosphere Lab at the Czech Technical University in Prague presented a paper in which they analysed and dissected the cyber espionage activities of an APT group in Latin America through the analysis of one of its tools, known as Machete. Today we publish their paper and the recording of their presentation.
Posted by Helen Martin on Dec 5, 2019
 In a paper presented at VB2019 in London, researchers Miriam Cihodariu (Heimdal Security) and Andrei Bogdan Brad (Code4Romania) looked at how surveillance is represented in fiction and how these representations are shaping people's attitudes to surveillance in current legal debates. Today we publish both their paper and the recording of Miriam presenting the paper in London.
In a paper presented at VB2019 in London, researchers Miriam Cihodariu (Heimdal Security) and Andrei Bogdan Brad (Code4Romania) looked at how surveillance is represented in fiction and how these representations are shaping people's attitudes to surveillance in current legal debates. Today we publish both their paper and the recording of Miriam presenting the paper in London.
Posted by Helen Martin on Dec 3, 2019
 At VB2019 in London industry veterans Righard Zwienenberg and Eddy Willems took a detailed look at the relationship between past and current cyber threats. Today, we publish both their paper and the recording of their presentation.
At VB2019 in London industry veterans Righard Zwienenberg and Eddy Willems took a detailed look at the relationship between past and current cyber threats. Today, we publish both their paper and the recording of their presentation.
Posted by Martijn Grooten on Nov 29, 2019
 Virus Bulletin is recruiting for a person to be the public face of the company
Virus Bulletin is recruiting for a person to be the public face of the company
Posted by Martijn Grooten on Nov 29, 2019
 At VB2019 in London, ZEROSPAM researchers Pierre-Luc Vaudry and Olivier Coutu discussed how email clustering could be used to detect malicious Emotet emails that hijacked existing email threads. Today we publish the recording of their presentation.
At VB2019 in London, ZEROSPAM researchers Pierre-Luc Vaudry and Olivier Coutu discussed how email clustering could be used to detect malicious Emotet emails that hijacked existing email threads. Today we publish the recording of their presentation.
Posted by Martijn Grooten on Nov 28, 2019
 Today we publish a VB2019 paper from Lion Gu and Bowen Pan from the Qi An Xin Threat Intelligence Center in China in which they analysed an APT group dubbed 'Poison Vine', which targeted various government, military and research institutes in China.
Today we publish a VB2019 paper from Lion Gu and Bowen Pan from the Qi An Xin Threat Intelligence Center in China in which they analysed an APT group dubbed 'Poison Vine', which targeted various government, military and research institutes in China.