Posted by Martijn Grooten on Apr 26, 2016
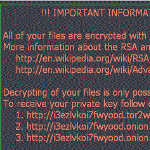 The current ransomware plague is one of the worst threats the Internet has seen and it is unlikely to go away any time soon. But telling people to never pay the ransom is unhelpful advice.
The current ransomware plague is one of the worst threats the Internet has seen and it is unlikely to go away any time soon. But telling people to never pay the ransom is unhelpful advice.
Posted by Martijn Grooten on Apr 22, 2016
In his VB2015 paper, Martin Korman presented his 'VolatilyBot' tool, which extracts malicious code from packed binaries, leveraging the functionality of the Volatility Framework.
Read morePosted by Martijn Grooten on Apr 21, 2016
 We have announced 37 papers (and four reserve papers) that will be presented at VB2016 in Denver, Colorado, USA in October. Registration for the conference has opened; make sure you register before 1 July to benefit from a 10% early bird discount.
We have announced 37 papers (and four reserve papers) that will be presented at VB2016 in Denver, Colorado, USA in October. Registration for the conference has opened; make sure you register before 1 July to benefit from a 10% early bird discount.
Posted by Martijn Grooten on Apr 15, 2016
 The people behind the MalwareHunterTeam have released a tool that helps victims of ransomware identify which of more than 50 families has infected their system, something which could help them find a tool to decrypt their files.
The people behind the MalwareHunterTeam have released a tool that helps victims of ransomware identify which of more than 50 families has infected their system, something which could help them find a tool to decrypt their files.
Posted by Martijn Grooten on Apr 13, 2016
 The PR campaign around the Badlock vulnerability backfired when it turned out that the vulnerability wasn't as serious as had been suggested. But naming vulnerabilities can actually be helpful and certainly shouldn't hurt.
The PR campaign around the Badlock vulnerability backfired when it turned out that the vulnerability wasn't as serious as had been suggested. But naming vulnerabilities can actually be helpful and certainly shouldn't hurt.
Posted by Helen Martin on Apr 7, 2016
 The Virus Bulletin Virus Prevalence Table, which ran from 1992 until 2013, gave users a regular snapshot of what was really going on in the virus (and later malware) world, recording the number of incidents of each virus reported to VB in the preceding month. In August 2000, Denis Zenkin, a self-confessed virus prevalence table junkie, shared his findings following a study of the virus prevalence tables over the preceding few years, allowing him to determine the top ten viruses of the period, the top viruses by type and the viruses of the year.
The Virus Bulletin Virus Prevalence Table, which ran from 1992 until 2013, gave users a regular snapshot of what was really going on in the virus (and later malware) world, recording the number of incidents of each virus reported to VB in the preceding month. In August 2000, Denis Zenkin, a self-confessed virus prevalence table junkie, shared his findings following a study of the virus prevalence tables over the preceding few years, allowing him to determine the top ten viruses of the period, the top viruses by type and the viruses of the year.
Posted by Martijn Grooten on Mar 30, 2016
 Security researcher Andreas Lindh recently found a vulnerability in Apache OpenMeetings that could allow remote code execution on a vulnerable server. Andreas reported the vulnerability to the OpenMeetings developers and, once it had been patched, he wrote up the details.
Security researcher Andreas Lindh recently found a vulnerability in Apache OpenMeetings that could allow remote code execution on a vulnerable server. Andreas reported the vulnerability to the OpenMeetings developers and, once it had been patched, he wrote up the details.
Posted by Helen Martin on Mar 24, 2016
 Word and Excel’s internal file formats used to be something in which few were interested – until macro viruses came along and changed all that. In 1996, Andrew Krukov provided an overview of the new breed of viruses.
Word and Excel’s internal file formats used to be something in which few were interested – until macro viruses came along and changed all that. In 1996, Andrew Krukov provided an overview of the new breed of viruses.
Posted by Martijn Grooten on Mar 18, 2016
 You have until the early hours (GMT) of Monday 21 March to submit an abstract for VB2016! The VB2016 programme will be announced in the first week of April.
You have until the early hours (GMT) of Monday 21 March to submit an abstract for VB2016! The VB2016 programme will be announced in the first week of April.
Posted by Martijn Grooten on Mar 15, 2016
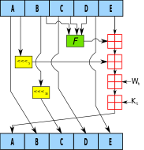 SHA-1 collisions may be found in the next few months, but that doesn't mean that fake SHA-1-based certificates will be created in the near future. Nevertheless, it is time for everyone, and those working in security in particular, to move away from outdated hash functions.
SHA-1 collisions may be found in the next few months, but that doesn't mean that fake SHA-1-based certificates will be created in the near future. Nevertheless, it is time for everyone, and those working in security in particular, to move away from outdated hash functions.