Posted by Virus Bulletin on Oct 14, 2015
Gabor Szappanos looks at how macro malware campaigns spread a commercial keylogger to harvest banking details.
Macro malware was a plague in the late 1990s, when Microsoft Office executed macros by default, making the writing of computer viruses literally child's play.
Macro execution has long been disabled by default, but in the last two years, we have seen a resurgence of macro malware, this time using social engineering to make the user enable macros manually, which then typically results in further malware being downloaded. In July 2014, we published a paper by Sophos researcher Gabor Szappanos, which was one of the first articles pointing to this new trend.
Today, we publish a new paper by Gabor, in which he looks at a series of campaigns that used Office macros to download the commercial HawkEye keylogger. The Office documents were generated using the Microsoft Word Intruder (MWI) kit, which has been used to spread more than 40 different malware families.
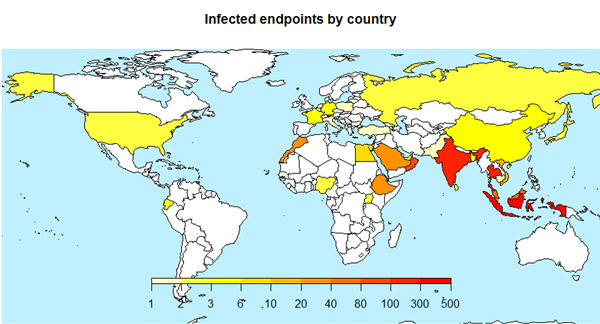
These particular campaigns primarily targeted users in Asia, who received spear-phishing emails allegedly containing payment receipts or shipping labels. A user who opened the attached document and then followed the instructions to enable macros would find themselves infected with the keylogger, which was then used to steal their banking credentials.
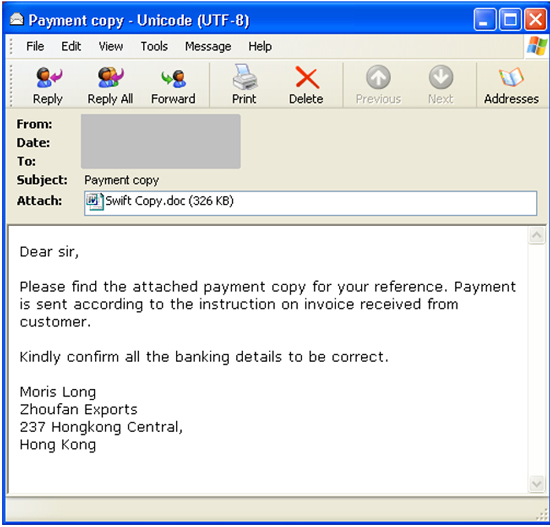
The terms and conditions of MWI don't permit large-scale campaigns, but with a few dozen to a few thousand victims, these campaigns will have been very successful for the perpetrators.
You can read the article here in HTML format or download it here as a PDF.