Deloitte, Argentina
Copyright © 2018 Virus Bulletin
Formbook [1] is an infostealer that has been advertised for sale in public hacking forums since February 2016 by a user with the handle 'ng-Coder'. It is more advanced than a keylogger as it can retrieve authorization and login credentials from a web data form before the information reaches a secure server, bypassing HTTPS encryption. Formbook is effective even if the victims use a virtual keyboard, auto-fill, or if they copy and paste information to fill the form. The author of Formbook affirms that it is 'browser-logger software', a.k.a. form-grabbing software. Formbook offers a PHP panel, where the buyers can track their victims' information, including screenshots, keylogged data, and stolen credentials. Hosting and domain services are provided for low prices with a bin only available in the Pro version.
Formbook was used in a spam campaign in late 2017, targeting the aerospace, defence contractor and manufacturing sectors in South Korea and the USA. It includes hiding, persistence, anti-analysis, deletion and termination mechanisms along with several commands that the C&C (command-and-control) server can receive. The 'ng-Coder' user indicated that Formbook should not be used for malicious purposes and blocked sales until further notice after the spam campaigns became known. According to 'ng-Coder', Formbook should only be used to spy on family members or employees if the user has the explicit right to do so. However, this claim is dubious given the barely legitimate nature of the use of such software.
Formgrabbers intercept HTTP(S) data and use inline hooking to redirect the function to one within the formgrabber before transferring the execution flow back to the HTTP function to complete the request. This technique allows formgrabbers to capture a user's information before the user submits it over the Internet to a secure server. While keyloggers focus mainly on capturing the user's input, formgrabbers collect pasted information and/or information selected via a drop-down option, which makes them more efficient than keyloggers.
A formgrabber injects a DLL (Dynamic Link Library) into a browser and monitors for calls to the HttpSendRequest API within WININET.DLL in order to intercept the data before encryption and send all requests to its own code, prior to sending the data onwards. Andromeda (aka Gamarue), Tinba and Weyland‑Yutani BOT are some malware families that use this technique.
Prior to advertising it for sale, a user with the handle 'ng-Coder' offered Formbook for free in public hacking forums so that other users could review it.
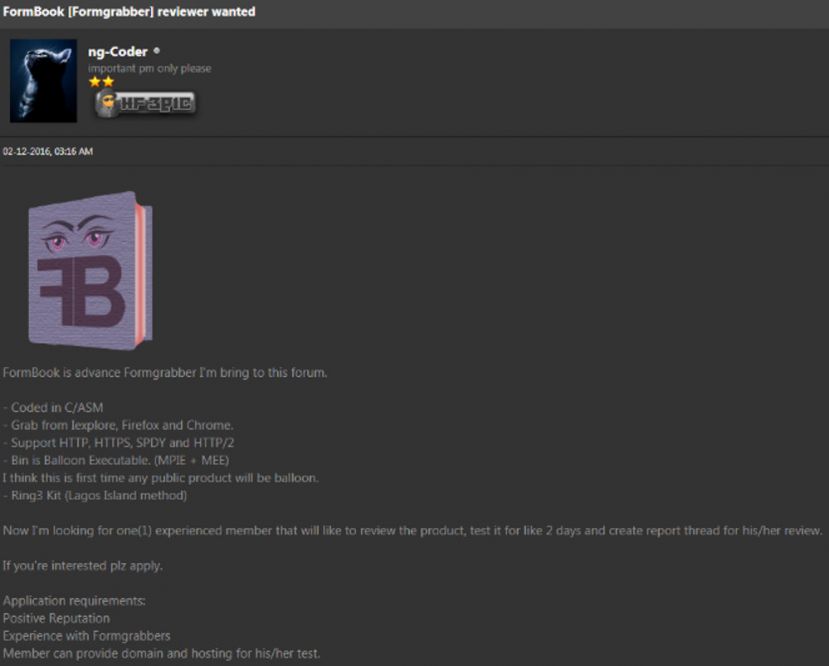 Figure 1: First mention of Formbook in a forum.
Figure 1: First mention of Formbook in a forum.
Soon after the free version was released, the user 'ng-Coder' advertised Formbook for sale at an initial price of 250 USD. However, the author reduced the price to 120 USD in early March 2016 after receiving several complaints about the price from forum members. The current pricing list and payment methods offered in the forum are displayed in Figure 2.
 Figure 2: Pricing list and payment methods for Formbook.
Figure 2: Pricing list and payment methods for Formbook.
According to the user 'ng-Coder', Formbook boasts the following features:
Formbook works as a botnet, infecting victims that are shown in a web panel in order to manage the information that is retrieved from them. Figure 3 shows the web panel.
Each bot can receive the following commands from the C&C server:
Formbook was used in spam campaigns targeting the aerospace, defence contractor and manufacturing sectors within the US and South Korea in 2017 [2]. It was distributed via PDFs with embedded links, DOC and XLS files with malicious macros, and compressed files containing the executable.
It was also observed in 2018, distributed via emails with DOCX files that contained a URL [3]. This URL downloaded an RTF file that exploits CVE-2017-8570 and drops an executable. This executable downloads the Formbook sample.
The analysed sample is a RAR self-extracting archive (SFX) that contains several files, as shown in Figure 4.
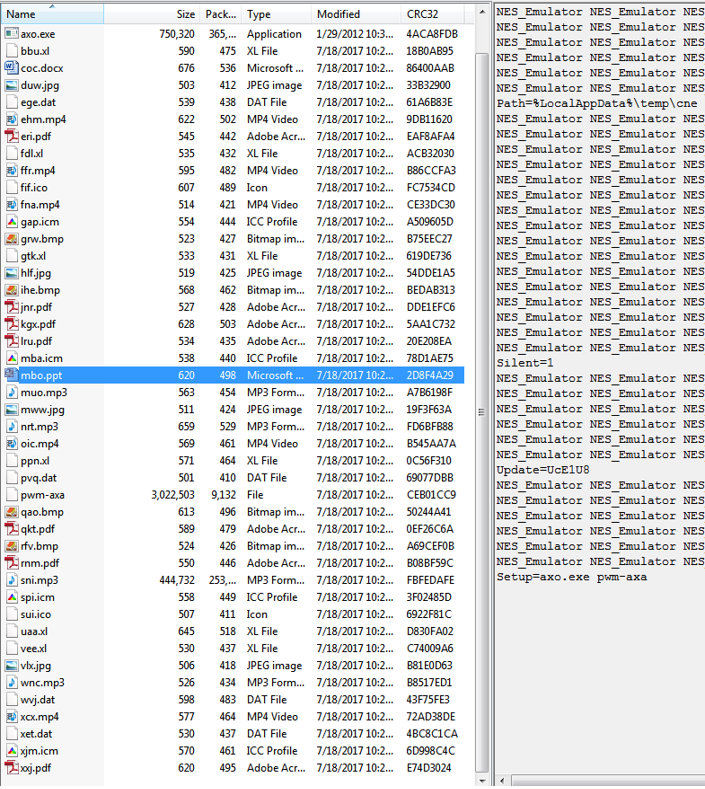 Figure 4: SFX file.
Figure 4: SFX file.
The description to the right of the files shows the following strings:
Files with a size below 1K contain a few strings that are probably used during decompression.
After executing the SFX file, Formbook extracts the files in %LocalAppData%\temp\cne using CreateDirectoryW. It then deletes the SFX file. Figure 5 shows the file extraction.
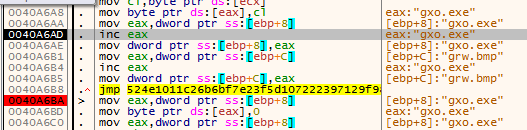 Figure 5: File extraction.
Figure 5: File extraction.
The axo.exe file is an AutoIt script that is executed with the pwm-axa file as a parameter. Figure 6 shows the properties of the axo.exe file.
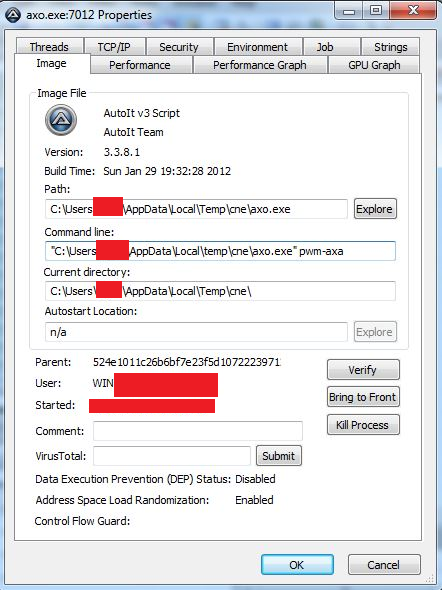 Figure 6: Properties of the axo.exe AutoIt executable.
Figure 6: Properties of the axo.exe AutoIt executable.
The script decrypts Formbook and loads it in memory. In order to do this, it creates a file with a random name that contains Formbook's functionality and deletes it soon after loading it in memory. This file contains 44 functions with obfuscated names. The sni.mp3 file includes interesting strings that were used during the execution, as shown in Figure 7.
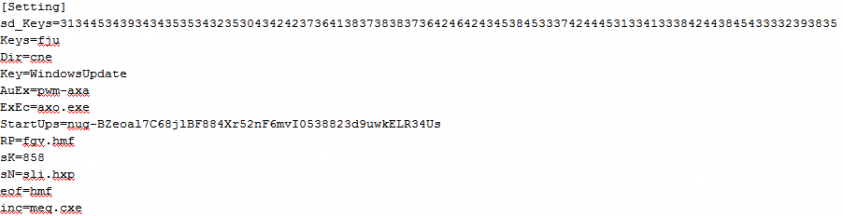 Figure 7: Interesting strings found in the sni.mp3 file.
Figure 7: Interesting strings found in the sni.mp3 file.
The script contains the following features:
The script changes the cne folder attributes to hide its content by executing the command FileSetAttrib($cne_Folder_Path, "+H").
In order to remain persistent, it modifies the Run registry key with a new key named WindowsUpdate that instructs the execution of axo.exe along with pwm-axa:
If IsAdmin() Then
RegWrite("HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Run", $WindowsUpdate, "REG_SZ", $cne_Folder_Path & "\" & $axo.exe & " " & FileGetShortName(FileGetShortName($cne_Folder_Path & "\" & $pwm-axa)))
Else
RegWrite("HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run", $WindowsUpdate, "REG_SZ", $cne_Folder_Path & "\" & $axo.exe & " " & FileGetShortName($cne_Folder_Path & "\" & $pwm-axa))
RegWrite("HKCU64\Software\Microsoft\Windows\CurrentVersion\Run", $WindowsUpdate, "REG_SZ", $cne_Folder_Path & "\" & $axo.exe & " " & FileGetShortName($cne_Folder_Path & "\" & $pwm-axa))
EndIf
Sleep(1000)
Sleep(1000)
EndFunc
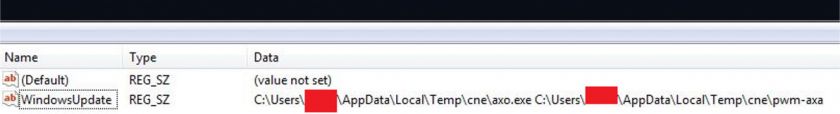 Figure 8: Persistence mechanism.
Figure 8: Persistence mechanism.
The script tries to modify the following registry keys:
And it:
Formbook will terminate if it finds VMware or VirtualBox processes running in the victim's system and if the 'D' drive has space of less than 1MB:
The script will check the HKCR\http\shell\open\command registry key to know which Internet browser the victim's machine uses by default.
Formbook will look for the svshost.exe process and terminate if it finds more than two svshost.exe processes running, as shown in Figure 9.
Despite Formbook infostealer having been around for a couple of years now, it only came to public attention after it was extensively used in spam campaigns in late 2017. The fact that Formbook wasn't noticed before is probably because its developers didn't release the builder to the public, so it was easy for them to track its activities and turn it off if they found that it was being used for purposes for which it was not intended or if it was gaining too much attention from the security community. Despite not being broadly used, Formbook represents a real threat, due to it being stealthier and more powerful than keyloggers.
Similar to the Agent Tesla remote access trojan (RAT), the author of Formbook initially offered a beta version of the product free of charge in order to receive feedback and make improvements.
The 'ng-Coder' user indicates that Formbook should not be used for malicious purposes, and after the spam campaigns were made public, he blocked Formbook's sales until further notice. According to 'ng-Coder', Formbook should only be used to spy on family members or employees if the user has the explicit right to do so. However, this claim itself is dubious given the barely legitimate nature of the use of such software.
The SHA256 hash of the SFX file that was analysed is: 2f74f8518bd14a882a870f3794a76dba381b59c1e40247a2483468959b572d82.
[1] Schwarz, D. The Formidable FormBook Form Grabber. Arbor Networks, 20 September 2017. https://www.arbornetworks.com/blog/asert/formidable-formbook-form-grabber/.
[2] Villeneuve, N.; Eitzman, R.; Nemes S.; Dean, T. Significant FormBook Distribution Campaigns Impacting the U.S. and South Korea. FireEye, 5 October 2017. https://www.fireeye.com/blog/threat-research/2017/10/formbook-malware-distribution-campaigns.html.
[3] Urgent server alert malspam delivers formbook trojan via CVE-2017-8570 word doc. My Online Security, 16 February 2018. https://myonlinesecurity.co.uk/urgent-server-alert-malspam-delivers-formbook-trojan-via-cve-2017-8570-word-doc.