2011-03-01
Abstract
Until recently, malware on mobile devices had not been used for organized crime involving large amounts of money. This changed when the infamous Zeus gang, known for targeting online banking, started to show a clear interest in infecting mobile phones and released a new version of their bot to propagate a trojan for mobile phones. Axelle Apvrille and Kyle Yang present an indepth analysis of the Zitmo trojan.
Copyright © 2011 Virus Bulletin
Malware on mobile phones has existed for several years, but until recently it had not been used for organized crime involving large amounts of money. This changed in September 2010 when the infamous Zeus gang, known for targeting online banking, started to show a clear interest in infecting mobile phones and released a new version of their bot to propagate a trojan for mobile phones.
In this two-part article (based on a paper presented at ShmooCon 2011) we will present an in-depth reverse engineering of the mobile phone trojan, show how to reroute stolen SMS messages to a test phone, and explain how to display hidden windows of the trojan.
For years, people have been predicting that malware for mobile phones will one day follow the same path as computer viruses and become both a significant problem and part of major cybercriminal activities [1], [2], [3], [4]. There are a number of reasons for this prediction: first, the number of mobile phones now outnumbers the number of desktop or laptop computers, and so a single mobile sample has the opportunity to spread widely. The recent Symbian Yxes worm, for instance, has been reported to have infected hundreds of thousands of Chinese subscribers [5]. Second, mobile phones make a perfect target for attackers, because, on the one hand, they are being used for sensitive operations (e.g. payments, storage of personal data) and on the other, they are quite easy to attack because they offer many communication interfaces, with little user education and weak protection. Third, as the gap between mobile phones and personal computers (laptops, netbooks etc.) narrows, mobile malware is expected to evolve quickly, inheriting skills from the past history and experience of computer viruses.
As an example, it took 20 years for the first polymorphic virus (V2PX) to appear on computers, whereas it took only eight years for one to appear on mobile phones (WinCE/Pmcryptic.A!tr).
Fortunately, the much feared mobile Death Star has not yet hit. Significant steps towards the dark side have nonetheless been noticed. In the old days, pre-2004, mobile viruses were mostly the product of enthusiast hackers curious to understand how their devices worked. But 2004 proved to be a turning point, with the appearance of several new proof-of-concepts including Duts, Brador and Cabir [6]. These opened the door for a new wave of mobile viruses, most of which were annoyware (viruses that disabled fonts, rebooted the phone etc.) for Symbian phones. By 2009, mobile malware authors had started to show more interest in making some quick money [7] – for example with diallers which called international numbers. This change of mood was confirmed in 2010, with Fortinet’s internal statistics showing an increase in monetized malware (approximately 30% in 2010) and malware targeting privacy (25%), while no new annoyware was detected (see Figure 1). This seemed to confirm that mobile malware is moving into the realms of larger-scale cybercriminality.
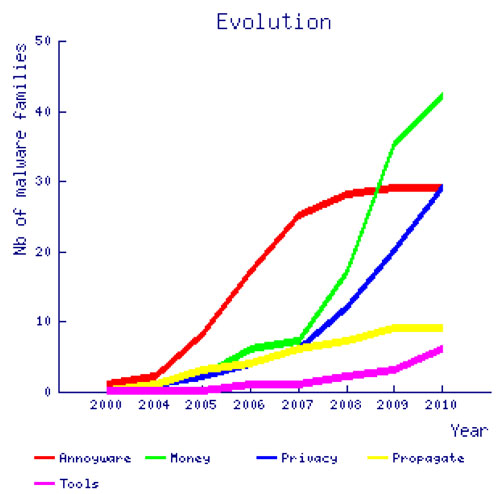
Figure 1. Number of new malware families identified for a given category and per estimated year of implementation.
However, in most cases, the rewards attackers reap remain rather low (although, due to the fact that victims and operators provide little information regarding the attacks they encounter, it is difficult to evaluate true financial losses): interesting for an individual attacker, but not significant enough to be interesting to organized crime. For example, the authors of the Windows Mobile Terdial dialler generated 135 euros in the first few days it spread. This may be worthwhile for a single attacker, but it is not enough to interest a large cybercriminal group. It is not easy for malicious diallers to generate more substantial revenue because premium phone numbers are rented for short periods and the revenue is divided between all resellers.
Zitmo is the first sign of organized criminals showing an interest in mobile malware. It is being propagated by newer versions of the infamous Zeus botnet which has a record of attacking online banking. Zitmo, short for ‘Zeus In The MObile’, infects mobile phones and intercepts SMS messages carrying a one-time password known as a mobile Transaction Authentication Number (mTAN). mTANs are commonly used by banks as an additional way to secure authentication of sensitive online transfers or transactions.
Zitmo was first discovered by s21sec [8] and shortly after by Fortinet [9], and a new variant was identified in February 2011. It has been written about in several blog posts and press releases, but as usual the full story has not been disclosed, or else is too fragmented in various places for readers to make the connections. This article is about making those connections so as to help understand how the attack works from start to end, but also revealing unknown aspects discovered during our research, such as similarities with other commercial spyware and a hidden debug window.
We will start by providing some background information on both Zeus and mobile malware. Then, we explain how the attack behind Zitmo works, from cybercriminal to bank account. We also cover the presumed making of Zitmo. In the second instalment of the article (next month) we will present our reverse engineering work of Zitmo, explaining each feature of Zitmo (startup, SMS interception, commands and corresponding actions). Finally, we will attempt to draw lessons from the attack, highlighting the roots of the attack and ideas to circumvent it.
In this section we provide some background information that will be useful to know before getting into the details of the specific Zeus/Zitmo attack.
Zeus (also known as Zbot) is a crimeware kit which allows a botnet herder to configure and create custom executables that precisely target their intended hosts [10]. The kit is primarily designed for stealing banking information, although it can easily be used for other types of data or identity theft. As it is sold in the underground market, there are several different botnets – each one targeting the specific hosts its bot herder configured – rather than there being a single Zeus botnet. For example, in the case of Zitmo, the configuration downloaded by the specific Zbot executables targeted several Spanish online banking and financial organizations.
The Zbot executable works as follows: first, it decrypts a hard-coded XOR-encrypted BLOB, which contains two pieces of information:
A URL, from which to download an encrypted configuration file.
A table, which corresponds to a scheduled key for the RC4 algorithm.
Next, it downloads a configuration file from the URL. The configuration file is both encrypted and compressed. The binary decrypts the file – as the RC4 key is already in its scheduled format, RC4 decryption boils down to processing it in RC4’s pseudo random generation algorithm (PRGA) [11]. Finally, the binary XORs the result with the initial encrypted configuration file to retrieve a compressed configuration file.
After decompression, the configuration file is parsed by the bot [12] in order to inject JavaScripts into bank pages. Then, the bot sends a report back to the server and waits for further commands. Figure 2 shows a few of the URLs targeted by the botnet and into which it injects JavaScript. Zitmo contained a form to get the victim’s phone number and model [8].

Figure 2. Part of the configuration file which matches the Zitmo attack. (Courtesy of David Barroso.)
From the point of view of mobile malware, it is important to note that although the iPhone, BlackBerry and Android are making an impression in the market, Symbian was still the most widespread mobile platform in 2010 (41% according to Gartner). In particular, Zitmo targets phones running Symbian OS version 9.1 or greater. The malware authors also planned to release a version for BlackBerry, but apparently never did so. Symbian OS 9.1 was released in 2005. It includes security features such as data caging and capabilities. In 2009, Yxes was one of the first pieces of malware to appear on this platform [13].
There are still relatively few tools and documents available to reverse engineer and experiment with Symbian OS 9 – security researchers are usually more attracted by research on the iPhone or Android phones. Among our favourite tools, we would cite IDA Pro (which supports ARM assembly code), SISWare for unpacking, and App TRK for remote debugging. The use of those tools is illustrated in [13], [14], [15], which contain valuable information regarding the reverse engineering of those phones.
This section is intended to provide an overview of how Zitmo works, and serve as a reference for the rest of the article. Mainly, it puts together and clarifies information found in [8], [16] and our prior work [17], [18], in addition to explaining facts which have not explicitly been highlighted before.
To secure online banking transactions, sensitive operations or logins, several banks (e.g. ING Direct, BB Bank, Deutsche Postbank – mostly European banks) use two-factor authentication. Two-factor authentication means that two different authentication methods must be combined from three possible choices: what the end-user knows (e.g. a password), what he has (e.g. a physical token) and what he is (e.g. biometric data). For example, to perform a sensitive operation on an account, banks typically ask the end-user to enter a valid identifier and password (something he knows) and a secret one-time PIN sent to him by SMS (something he has). This secret code sent by SMS is also known as an mTAN – a mobile Transaction Authentication Number. This solution is believed to be quite secure [19]. Unfortunately, Zitmo demonstrates a practical way to defeat it.
The attack works as follows: first, the victim’s computer is infected by a sample of Zeus (see Section 2). The compromised computer becomes part of a Zeus botnet, controlled by a botmaster (see Figure 3, step 1). The next time the end-user visits his favourite bank’s website (e.g. Santander Bank for Zitmo), the infected computer lets the HTTP request go, but modifies the content of the response on the fly and dynamically injects a malicious script into the bank’s HTML code (step 2). The victim’s browser displays the modified content – which is controlled by Zeus. Note that this is not the same as phishing: the URL displayed in the browser is real and corresponds to the legitimate bank, whereas, in phishing, the URL corresponds to a website controlled by the attackers. The modification of content does not consist of pointing to another website, but of code injection directly on the compromised computer of the victim.
In the case of Zitmo, the injected script builds an HTML form which requests the victim’s mobile phone number and model. These details are purported to be important information required ‘for security’. The end-user has no reason to be suspicious as he believes the page he is viewing is legitimate. Of course, the phone number and phone model are not sent to the bank, but transferred to the bot master. The bot master contacts another host with SMS sending capabilities, which sends an SMS to the victim’s phone. This SMS claims to be a digital security certificate, and provides a link to download the fake certificate (step 3). The download backend was hosted on krambamburr.com (fast flux).
Again, the victim has no reason to be suspicious because he believes the SMS has come from the bank. Note that SMSs are a handy way to propagate malware because, unlike MMS, all mobile devices are generally properly configured to receive them.
The end-user downloads the alleged security certificate (cert.sis) from a remote website. At this point, a knowledgeable end-user might become suspicious, because certificates are usually sent using the PKCS#12 format (extension .p12 or .pfx), rather than using a Symbian installation package (.sis or .sisx extension). In reality, cert.sis is not a certificate, but a modified version of a known Russian spyware program named SMS Monitor [16].
Finally, the end-user installs the trojan on the phone (believing it to be the security certificate). Now both authentication vectors – the victim’s computer and his phone – are infected.
The trojan consists of a malicious daemon, named NokiaUpdate.exe, which listens to incoming SMSs. Additionally, it has the capability to react to a few specific commands sent via SMS by an administrator (a member of the malicious gang).
As soon as the trojan is successfully installed on the phone, it sends an SMS message, ‘App installed ok’, to the default hard-coded administrator’s phone number. In Zitmo, this was a UK phone number (+44778148xxxx [phone number censored]), which is now blocked by most operators. This SMS is sent only once, at the first startup after installation, probably to notify the attackers that they have a new victim. The phone number acts as an administrator number for the mobile trojan and pilots the rest of the attack.
Next, the malicious administrator needs to configure the trojan to target a particular online bank. To do so, he must send SMS messages to the victim with a specific body as text. The specific bodies of those SMS messages are also called commands.
So, the first command the administrator would have to send would ask the trojan to silently forward any SMS coming from the bank’s phone number (add sender PHONENO). The second SMS would activate the spyware (ON).
When the victim logs into his bank account, or performs a sensitive online transaction, a malicious keylogger on the infected computer (Zbot binary on Windows) eavesdrops on the victim’s credentials (e.g. login, password, credit card number). The first authentication factor falls into the hands of the Zeus gang. Meanwhile, the online bank sends an mTAN by SMS to the victim’s phone. This SMS is intercepted by the mobile trojan, forwarded to the administrator’s phone number and discarded from the victim’s phone (step 4 of Figure 3). The second authentication factor falls into the hands of the Zeus gang.
Note that the mTAN is not displayed at all on the victim’s phone, so he cannot correctly end his own banking operation. While the victim is probably still waiting for the mTAN, trying to figure out what is happening (or reverting to a degraded authentication mode without mTANs), the cybercriminals have all the information they need to conduct their fraud.
In fact, the real novelty in Zitmo is not the fact that it defeats two-factor authentication, but that it is able to initiate a fraudulent two-factor authentication. Indeed, prior to Zbot, executables were already capable of defeating mTANs: as mTANs are entered on a compromised PC, they merely needed to log keys or mouse gestures corresponding to the mTAN. What Zitmo improves is the fact cybercriminals can now choose to initiate the next frauds when they wish (they need no further interaction with the victim). For example, they can log into the victim’s bank account (at any time), initiate a transfer, intercept the SMS from the victim’s phone (at any time) and finish the transaction as if they were the user.
Previously, we mentioned that Zitmo is very closely derived from a Russian spyware program named SMS Monitor. The code is very similar (several strings and assembly routines match exactly – see Table 1), with a few minor differences:
Zitmo does not eavesdrop on outgoing SMS messages
Zitmo sends an SMS the first time it is run
Zitmo does not implement any licence control mechanism
Zitmo’s packaging is different: different name, different UID, and all features are grouped into a single executable (no DLLs).
| Zitmo compared with | Exact match of assembly routines | Exact match of strings (case-sensitive match) |
| SMS Monitor Lite | 60% | 89% |
| SMS Monitor | 59% | 90% |
| SymbOS/Trapsms.A!tr.spy | 13% | 2% |
| SymbOS/Fwdsms.D!tr.spy | 16% | 30% |
Table 1. Comparison of Zitmo with other trojans.
The percentages in Table 1 clearly show that Zitmo is strongly related to SMS Monitor and SMS Monitor Lite. Note that there are also matches with other pieces of malware, such as SymbOS/Trapsms.A!tr.spy because, for instance, some object instantiation routines or string constants are very common among Symbian executables.
Like most software of this kind, it is advertised as a tool for ‘parental control or security audit’. Although this is quite possibly a cover – a ‘politically correct’ way of describing a borderline application – the developer of SMS Monitor did not seem, to us, like a high-profile cybercriminal and/or someone related to the Zeus gang. From the outset, he was very helpful at responding to our inquiries, providing technical information about his spyware – which is not the behaviour one would expect of a criminal. Furthermore, it would not be very shrewd of him to sell a piece of spyware on the one hand (he says he has about 100 registered users) and incriminate himself by using it for malicious activities on the other.
It seems more likely that a member of the Zeus gang sought such a piece of spyware and either cracked a registered version or reverse engineered the lite version to re-use it in Zitmo. The task was probably made easier by the fact that the developer of SMS Monitor published two technical articles detailing his software in a Russian hacker magazine named ‘xakep’ (pronunciation close to ‘hacker’) [20], [21].
The Zeus gang re-packaged the spyware, naming the executable NokiaUpdate.exe so as not to arouse suspicion, and had it signed by Symbian’s Express Signed program [17]. The Express Signed program has already been abused by several pieces of malware (e.g. Yxes, CommDN, Album, NMPlugin) because it allows malware authors to sign their programs with all the security capabilities they should ever need, at an affordable cost [22]. Occasionally, a few applications submitted to the Express Signed program are selected for random audit but this was not the case for Zitmo, so the trojan was signed without anybody reviewing it.
To sign an application with Express Signed, one must, however, purchase a Publisher ID from TrustCenter CA. In the case of Zitmo, the malware authors provided TrustCenter with an official Azerbaijani company registration document and a copy of the alleged registrant’s passport. Unfortunately, it seems that it is easy for members of the Zeus gang to get hold of fake or stolen identification – [21] even explains a possible procedure, scanning stolen documents.
In the second part of this article we will provide details of the reverse engineering of a Symbian Zitmo sample, as well as looking at security considerations and solutions.
We thank reviewers Guillaume Lovet (Fortinet) for his technical and in-depth review, and Ludovic Apvrille (Telecom ParisTech) for useful comments on the paper’s structure. We also thank David Barroso (s21sec) for kindly sharing information regarding Zeus and Zitmo.
[3] Lovet, G. Dirty money on the wires: the business models of cybercriminals. Proceedings of the 16th Virus Bulletin Conference, 2006.
[4] Coursen, S. Mobile Malware: A Clear and Present Danger. ISSA, pp.35–36, January 2006. https://www.issa.org/Library/Journals/2006/January/Coursen%20-%20Mobile%20Malware.pdf.
[5] Chickowski, E. Chinese Mobile Malware Signals Danger Opportunity for Channel, April 2010. http://www.channelinsider.com/c/a/Security/Chinese-Mobile-Malware-Signals-Danger-Opportunity-for-Channel-590400/.
[6] Chen, T.; Peikari, C. Handbook of Research on Wireless Security, chapter 1. Idea Group Publishing. Y. Zhang, J. Zheng, M. Ma (eds.), 2008.
[7] Apvrille, A.; Zhang, J. Four Malware and a Funeral. 5th Conf. on Network Architectures and Information Systems Security (SAR-SSI), 2010.
[8] Barroso, D. ZeuS Mitmo: Man-in-the-mobile, September 2010. http://securityblog.s21sec.com/2010/09/zeus-mitmo-man-in-mobile-i.html.
[9] SymbOS/Zitmo.A!tr.spy. Fortiguard Center, Virus Encyclopedia, September 2010. http://www.fortiguard.com/encyclopedia/virus/symbos_zitmo.a!tr.spy.html.
[10] McDonald, D. Zeus: God of DIY Botnets, October 2009. http://www.fortiguard.com/analysis/zeusanalysis.html.
[11] Yang, K. ZeuS: Bot to Master early communication protocol (Part one of two), October 2010. http://blog.fortinet.com/zeus-bot-to-master-early-communication-protocol-12.
[12] Yang, K. ZeuS: Bot to Master early communication protocol (Part two of two), October 2010. http://blog.fortinet.com/zeus-bot-to-master-early-communication-protocol-part-two-of-two/.
[15] Zhang, J. Find out the ’Bad guys’ on the Symbian. Association of Anti Virus Asia Researchers Conference, 2007.
[16] Tarasov, D. SMS Monitor User Manual. http://dtarasov.ru/smsmonitor_manual_en.html.
[17] Apvrille, A. ZeuS In The MObile (Zitmo): Online Banking’s Two Factor Authentication Defeated, September 2010. http://blog.fortinet.com/zeus-in-the-mobile-zitmo-online-bankings-two-factor-authentication-defeated/.
[18] Apvrille, A. Zitmo Follow Up: From Spyware to Malware, September 2010. http://blog.fortinet.com/zitmo-follow-up-from-spyware-to-malware/.
[20] Tarasov, D. SMS Spy. xakep magazine, 9, 2006. http://www.xakep.ru/magazine/xa/093/132/1.asp (in Russian).
[21] Tarasov, D. Evil-coding Symbian. xakep magazine, 3, 2009. http://www.xakep.ru/magazine/xa/123/096/1.asp (in Russian).
[22] Apvrille, A. Symbian Signed Mobile Malware: One Gang?, July 2010. http://blog.fortinet.com/symbian-signed-mobile-malware-one-gang/.