2011-01-01
Abstract
VB's lab team take a closer look at eScan Internet Security 11, commenting on its funky styling and the wealth of features it has to offer.
Copyright © 2011 Virus Bulletin
We have had a chance to check out the latest eScan product in the last couple of VB100 comparative reviews, and have been intrigued by both the snazzy look of the new interface and the promise of a wealth of additional features. In this review we’ll be taking a more thorough look at version 11 of MicroWorld’s eScan Internet Security to find out how well the funky styling works and what more it has to offer.
MicroWorld Technologies is a veteran player in the anti-malware world, having been founded in 1993. The company first submitted a product for VB100 testing in 2003, and since then it has become one of our most regular participants – providing support for every platform we test on and keen to face up to the challenge of our certification scheme month after month. The company’s test record has been exemplary, with a solid, if not quite unbroken run of VB100 passes – even weathering the trying switch from an OEM engine to all-in-house technology with only the slightest dip in performance.
According to MicroWorld’s website, escanav.com, the company is incorporated in the US, but is Indian in origin and has a large presence there, as well as offices in Germany, South Africa and Malaysia. From this base is produced a complete set of solutions, ranging from home-user to enterprise level and including a selection of dedicated server and gateway products – there is even a home-user Linux solution. The company website focuses heavily on the product range and its promotion, with the most prominent areas given over to information on the products, trial downloads, licensing and partner resellers. The bottom of the home page is adorned with a thorough selection of certification logos, including the VB100 award.
There is, of course, some more general content, including a blog, information on the latest major threats, and a news section, which seems to focus on company news rather than threat-related information.
Also grabbing interest on the home page were links marked ‘Wiki’, which lead to a sub-site featuring a surprisingly well stocked knowledgebase. This is presented in FAQ format and includes some interesting general tips and advice as well as solution-specific information. It is here, we later discovered, that the help system for the product range is hosted. This appeared to be very thorough and clearly laid out with plenty of illustrations, but it takes an almost entirely ‘describe-what-each-button-does’ approach, rather than the generally more useful task-oriented approach (however, that may have been available elsewhere in the large wiki area).
A ‘Forum’ section is similarly full of questions, most of which appear to have been answered rapidly, although users with more specific queries seem to be redirected in most cases to a live chat support system. On visiting this and posing a random question, we wondered at first if the system was automated, given the stock ‘welcome’ and ‘please provide licence info’ responses, but a friendly plea for quick help brought a more human-sounding reply, with at least some effort made to resolve the problem. Phone-based support is also available, but this is time-limited and regional, and customers are encouraged to use email or live chat where possible.
One other thing of note on the website are the links scattered around all over the place to the ‘eScan Anti-Virus Toolkit’ – something which also does well on a number of popular software download sites. This is a simple on-demand scanner tool with cleaning and command-line control as well as GUI, which can be used on systems that are not running the full product; its set-up and usage are pretty straightforward, and it’s a pretty handy, powerful little tool.
Of course, the part of the website we were most interested in was the download page for the latest full product, and from here we initiated a download via a proprietary download manager solution, which dealt well with losing connection repeatedly. When allowed to complete properly the download measured close to 150MB, but it took only a few minutes on a reasonably fast connection.
We tried the product on a selection of systems. The hardware requirements are fairly forgiving, with only 256MB of RAM required (although more is recommended). Support is still in place for Windows 2000 as well as the latest x64 versions of Windows 7, so all but the most ancient of systems ought to be able to run the product. To try this out, we ran it on netbooks and wheezy old systems as well as more standard hardware.
Given the range of features we knew to be included in the product, we found the installation process fairly straightforward. It offers to disable the Windows Firewall, if it is running, in order to replace it with its own, but other than that there seemed to be little in the way of initial configuration or options to deal with, and after a reboot it was apparently all set and ready to go.
As mentioned previously (and repeatedly in the company’s literature), the interface design is a bit of a departure from the norm – but not so extreme as to confuse anyone. There seem to be two standard approaches to anti-malware GUI layout, the ‘traditional’ style, with a menu down the left-hand side covering the various modules, and the currently modish style of having several large icons arrayed across the centre of the main window covering the main functions. There are a few radical departures from this pattern, some of which lean towards the opaque, but eScan manages to shake things up a bit without wandering too far from familiar patterns. The most notable thing here is the ‘dock’ at the bottom of the GUI, on which icons for all the main areas are presented. The colourful icons enlarge on rollover in the Mac style and it is reasonably easy to decipher what each is intended to denote. The rest of the GUI is much simpler, with a plain tab for each module providing start/stop buttons, information on status, reporting of events and so on, in plain, unadorned text.
In each of these areas there is a ‘Settings’ button, which leads to configuration controls for each module. These are fairly plain and unfussy, text-based and generally provided in exhaustive detail; just about everywhere we looked, there were more opportunities for fine-tuning to achieve just about any combination of settings. The wording of most was clear and lucid, and although in more sophisticated areas it becomes increasingly difficult to explain concepts concisely in non-technical language, we felt that the fine-tuning options would be fairly accessible to the interested, but non-expert user. Something that was lacking was context-based help rather than the generic link to the online wiki system at the top of the main interface. Being able to click straight through to a full description and guidance relating to the particular area in which one has hit a problem can be invaluable – and particularly good for encouraging those who do not have a complete understanding of what they are dealing with to take an interest, learn the ropes and take some responsibility for their own security. For many, browsing and searching through a complete help system is likely to be too much like hard work, and the opportunity to turn a moment’s interest into an educational experience for the user is easily lost.
With such a wide range of ground to cover, we’ll leave a closer look at the configuration system for later, after first taking a quick look at our main area of interest.
In its earlier years eScan was powered by the Kaspersky engine, with some in-house-developed extras on top. In our tests the product’s results routinely followed those achieved by Kaspersky Lab’s own solutions fairly closely. When MicroWorld first announced it was planning to drop the OEM engine to fly solo, our first reaction was one of surprise and trepidation – having seen several other products try to go it alone in this way, with generally disastrous results, we were highly sceptical that eScan would be able to retain its VB100 certified status, let alone maintain its previous solid record and regular high scores. After a brief wobble and a slight drop in detection rates over the following months, however, eScan mounted a steady and apparently unstoppable attack on our test sets, with coverage growing more and more thorough each month. False positives have been an occasional problem, but rarely a major one, and its superb detection rates routinely place it in the high-achiever cluster on our RAP quadrants.
With plenty of testing history behind us, we ran a few additional detection tests using some newer and older sample sets that are not routinely used in VB100 testing, as well as some extra clean software. We saw a pretty similar pattern of excellent coverage and minimal false alarms. Indeed, this latest version of the product boasts a whitelisting system which, the company claims, should entirely eliminate any risk of false alarms on important operating system files (the type which generally cause the most havoc and distress). This system certainly appeared to have been working well in the last few VB100 tests, with no problems encountered despite some major expansion of our clean sets, and even when run over expanded sets containing large quantities of unchecked material we saw no evidence of false alarms.
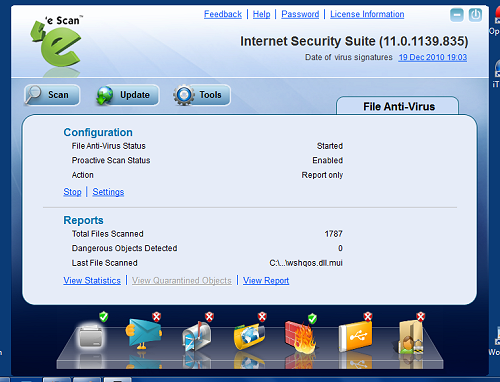
The product’s scanning speed is not super-fast and, as we observed in the most recent comparative (see VB, December 2010, p.27), can be a little unpredictable – with some scans taking notably more or less time than the same job run just moments earlier. Running a standard basic scan – covering only memory, registry and so on – took a few minutes at most, but a thorough check of a large, well-stocked system can take several hours and is usually best left for an overnight run when the machine is not in use (of course, a comprehensive and well-designed scheduler system is available to simplify and automate this). That said, where speed really counts is in on-access mode, as this is what will affect the running of the machine. Here, all seems pretty good, with measures taken in the last test proving very low indeed, both in terms of lag times imposed on accessing files and in the amount of RAM and CPU used. Some further tests in this area showed consistently light system impact when running a variety of common tasks.
In addition to the standard protection offered by this static file scanning and monitoring, and the additional features we’ll look at in the next section, there are a couple more elements covered in the main ‘File Anti-Virus’ section of the interface which merit a mention here. Buried on the second tab of the settings dialog for this section is a checkbox marked ‘Enable Proactive Scan’, which, according to the description in the help pages, applies an extra layer of heuristics for picking up on suspicious activities at run-time, including monitoring registry changes and so on. This option appears to be disabled by default, but when trying some of the few malware samples we found which were not picked up by the standard scanner, some additional protection was seen here – almost all samples performed some activities which caused them to be spotted and warned about. This additional protection was counterbalanced by a slightly increased tendency to warn about legitimate items performing unusual actions though – so this option is perhaps best reserved for experts and the extremely paranoid.
The final item is labelled ‘Folder Protection’, and locks down specified folders, preventing any changes to the files stored in them. This seems like a nifty idea, allowing one to corral one’s most important items and keep them safe from damage. A brief test showed this feature to work nicely against a range of attempts to subvert it.
As if this solid level of protection at the file level was not enough, the suite includes a comprehensive range of additional layers of protection. The second and third tabs on the GUI dock are mail anti-virus and anti-spam, their icons differentiated by the presence of a mailbox as well as an envelope in the anti-spam one. The mail scanning is pretty straightforward, defaulting to blocking a wide range of executable file formats as well as some specific filenames commonly used by malware. Additional options include checking inside compressed files, looking out for attachments with multiple file extensions and watching out for attempts to exploit vulnerabilities in mail clients – there is an option to block all HTML emails containing scripts. There is also a surprise extra in the form of a mail backup system, which can be set to archive all mails and attachments to a selected location. All of this is clearly laid out and generally pretty self-explanatory.
The anti-spam settings are, of course, a little more complex: at the most basic level they can be set to add warnings to various parts of mails detected as spam, to check for certain character sets or tell-tale spammy characteristics, to check outgoing messages, forwards and replies (all disabled by default), and even to block or whitelist messages containing phrases specified on a user-configurable list. Somewhat oddly, the main tab is labelled ‘Advanced’, but also has a button marked ‘Advanced’ which leads to the truly advanced settings. Here, spam-filtering geeks can really let themselves go, tweaking which parts of mails to include in checks, which RBL servers to use and whether or not to check SPF compliance and SURBLs. There is also the mention here of eScan’s ‘Non-Intrusive Learning Pattern’, a Bayesian filtering system which the help system describes as ‘revolutionary’, without giving away a great deal of information about what it does or how it works. Our anti-spam testing system is currently not geared up to test desktop solutions, but we hope to introduce this facility soon, and will add eScan’s offering to the list of solutions to look at, to find out how this system fares.
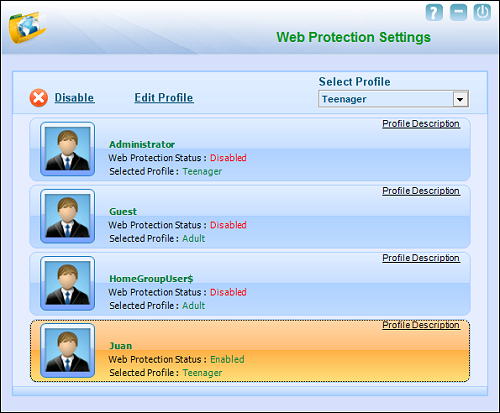
The middle icon on the dock is tagged ‘Web Protection’, and consists mainly of parental controls. These are nicely laid out and fairly simple to use, with a set of levels which can be applied on a per-user basis, including ‘adult’, ‘teen’, ‘adolescent’ and ‘walled garden’. Each is infinitely configurable, with enormously long lists of both whitelisted sites and keywords associated with half a dozen categories of potentially unwanted content. The keywords list includes the names of a bewildering range of beverages in the ‘alcohol’ section, and such a wide selection of military terms and weaponry listed under ‘violence’ that it may well hamper any kind of historical research if applied injudiciously. The process of adding keywords and adjusting settings is clear and simple, and it all seems to work very nicely. Attempting to access a site featuring one of the blacklisted words triggers a warning pop-up and a replacement web page. Users should note that when switching on this system they also need to set a master password via the link at the top of the interface. A helpful tool tip on the alert pop-up lets on that if this step is forgotten, the password ‘admin’ will grant access to any and all content.
One other section in this area is labelled ‘Phishing Filter’ – in most other areas configuration is all-encompassing, but here, other than a simple start/stop button, no further control or information is given, even in the help system.
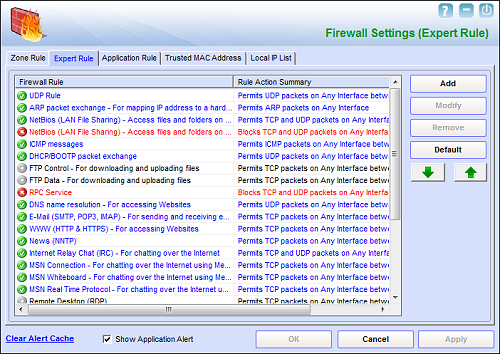
Moving swiftly onto the firewall, this is a fairly standard implementation, with a scale of protection ranging from allow all to block all, via ‘Limited filter’ (only applying a basic set of rules) and ‘Interactive filter’ (prompting for user decisions when something is not defined). The basic settings seem fairly well defined and work reasonably well, while the interactive mode is much more thorough but presents a lot of pop-ups if not configured carefully. Fortunately, a good depth of configuration is provided once again, and quite some effort has been made to assist less skilled users. Rather than just providing stark and unhelpful acronyms, descriptions of what each protocol is needed for are given, and proper sentences are used in the rule descriptions, which should make things a little easier for technophobes (although some understanding of networking basics will be required to operate it properly). The tweaking and adding of rules is a nicely presented and smooth process.
The ‘Endpoint Security’ section covers application and USB device control. The USB section scans flash drives for malware and disables autoplay; it can also be set to block or insist on a password for all USB devices, and to whitelist known devices. Application control is considerably more complex, with a monster list of known applications grouped into categories and blockable on a per-application basis. The categories cover gaming, messenger, media player and P2P software, extending the already thorough parental controls settings to a business-ready level.
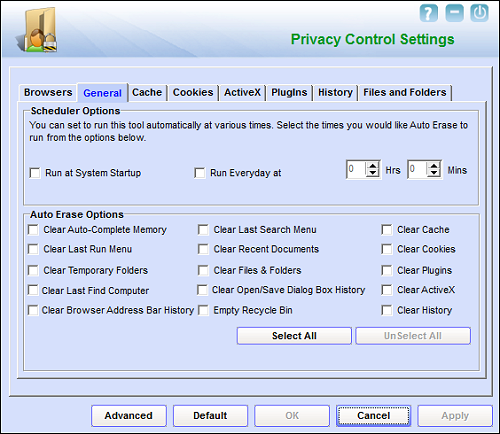
The final major sub-section is ‘Privacy Control’, which focuses on browsers and can clear history, caches, cookies etc. on demand or on a schedule. It can also be used to browse history and caches and delete individual items, and to clear Windows recycle bins and recently accessed lists. However, it seems to cover only Internet Explorer and Firefox, with no mention of any of the other browsers – including Chrome, Opera and Safari – installed on our test system. Once again, the controls are clear, simple and comprehensive, and most of the bases seem to be covered to ensure that whatever you’ve been up to can’t be tracked – ideal for international secret agents and the paranoid.
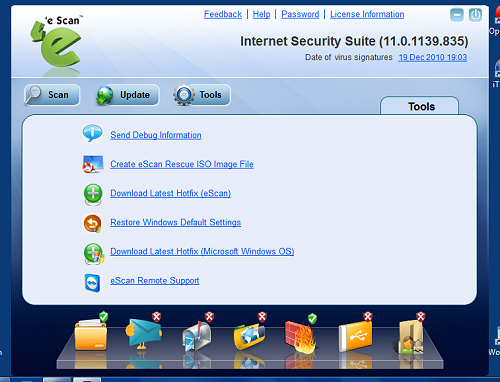
That’s all for the main set of modules (note that each has a button to create a report of all activity noted or performed, for total traceability), but of course, not all the suite has to offer. A button at the top of the interface, next to the ‘Help’ button, is labelled ‘Tools’ and provides a screenful of further items. Several of these are related to product maintenance, including generating debug information to help support issues, downloading patches, and allowing a support engineer remote access. There is also the option to create a boot CD to provide a clean environment for disinfection; this is an increasingly common offering, and something we’ve been planning to introduce into our comparative testing. In this case, it is apparently Windows-based, and is provided as part of the installation media for those purchasing boxed copies of the product.
A couple of items in the ‘Tools’ tab are a little different however – one downloads and applies the latest Windows updates, using the company’s own download manager tool. This seems to be provided as an alternative to the standard Windows Update process, but appears to be lacking in configurability or scheduling tools. A similarly basic item is labelled ‘Restore Windows default settings’, and really does just that – we clicked on the link expecting to be presented with some options and so on, but were surprised to see it start running the normal malware scan dialog, apparently trolling through the system looking for changes which could have been made by malware, and reverting them to their default values.
Leaving the interface, the final few items are found on the context menu from the system tray icon. Included here, as well as the option to open the main ‘console’ and other standard items such as the ‘about’ information, is a network activity monitor – a little application that lists everything connected to the network and provides some basic details on each. Right-clicking any process gives the option to kill it or look up more information on the eScan website, where most common items are explained in some detail. A similar application is labelled ‘System Information’. This provides detailed data on the host machine – much of which can be found in the Windows Computer Management console on most platforms, but here it is presented in a nice, orderly fashion with plenty of helpful, colourful icons. The final item is a virtual keyboard, designed to defeat any keyloggers which may have sneaked past the battery of protective layers. This is a fairly simple, but by no means unappealing little gadget.
After a rather exhausting trawl through the vast wealth of add-ons, our final impressions of eScan 11 are generally pretty favourable. It maintains, and even improves upon the excellent levels of detection and proactive protection provided by previous versions, and adds a little extra sparkle in the form of the funky dock gizmo (and there’s an extra bit of show business when closing windows, as they twirl away in a rather unnecessary spiral form). Beyond the shiny front page, things are much more businesslike and functional, with some of the best configuration and controls we have seen in any product lately, both in terms of the depth of fine-tuning available and in their clarity and simplicity. The range of extras is truly impressive, with the parental controls particularly complete and thorough, especially when supplemented by the application control module – combined, they add up to a system suitable for both worried parents and corporate policy enforcers.
It’s not all perfect of course. The help system does let the product down a little; a proper contextual system providing instant and targeted advice would be much better, and some kind of task-based guidance in addition to the current list of options is a must. There were also places where the product seemed to lack internal consistency, with some of the extras appearing tacked on and not properly integrated into the main suite. Some features also seemed short on description or controls, particularly compared to the thoroughness displayed elsewhere, and occasionally we were taken by surprise when the click of a button kicked off an activity rather than taking us to the expected set-up stages. When really treating the product badly, thrashing at the buttons and overloading systems, we managed to make it ‘hang’ a couple of times (at least, by the Windows 7 definition – in reality, it just had to calm itself down for a few seconds).
These are fairly minor gripes though, mainly to do with usability, and in general it does an excellent job in this area, making some serious tools accessible to all. On top of the superb protection built in, this makes it a solid and impressive suite all round.
MicroWorld Technology’s eScan Internet Security Suite 11 was tested on:
Intel Pentium 4 1.6 GHz, 512MB RAM, running Microsoft Windows XP Professional SP2.
AMD Athlon64 3800+ dual core, 4GB RAM, running Microsoft Windows XP Professional SP3 and Windows 7 Professional.
Intel Atom 1.6GHz netbook, 2GB RAM, running Microsoft Windows XP Professional SP3.