2010-12-01
Abstract
August 2010 saw the appearance of the first piece of malware for the Android mobile platform. Denis Maslennikov examines three variants of the FakePlayer SMS trojan.
Copyright © 2010 Virus Bulletin
The vast majority of today’s mobile malware is designed to make illicit profits. This type of malware (particularly SMS trojans) is most widespread in Russia and certain CIS countries for one very simple reason: weak legislation in these countries makes it possible to rent short premium pay numbers anonymously. Essentially, it is this weak legislation that has led to the appearance of a large number of trojans which send SMS messages to short premium pay numbers in order to make a profit for their creators.
From Symbian to Android and Windows Mobile, there is a wide selection of mobile operating systems on the market. In other words, unlike the PC segment, there isn’t a single dominant platform for malware writers to target. After all, not everyone has a smartphone – many people use standard mobile phones. As a result, the vast majority of known SMS trojans are written for Java 2 Micro Edition (J2ME). Most standard mobile phones support this platform, as do smartphones running Symbian and Windows Mobile. In doing this, malware writers have covered all their bases and thus solved the problem of picking a platform to target.
Of course, this doesn’t mean that smartphones aren’t targeted specifically by malware writers. We’ve seen a lot of SMS trojans both for Symbian (Trojan-SMS.SymbOS.Enoriv, Trojan-SMS.SymbOS.Lopsoy) and for Windows Mobile (Trojan-SMS.WinCE.Sejweek, Trojan-SMS.WinCE.Abcmag). The first trojan for Symbian appeared in 2007; the first for Windows Mobile in 2008. Until the beginning of August 2010, the Android platform – which has managed to win a certain share of the market in a relatively short space of time – had escaped the attention of malware writers. However, that changed with the appearance of Trojan-SMS.AndroidOS.FakePlayer, the first SMS trojan for the Android platform. This article examines the FakePlayer trojan and its evolution.
One important point should be stressed from the start: the FakePlayer trojan is relatively straightforward in terms of its code. However, there are two other important aspects which make it interesting: it’s the first piece of malware for Android seen in the wild, and it’s only Russian users who are at risk of financial loss due to infection by this trojan.
In the following sections we take a look at three variants of this trojan, looking at where they came from, and the way in which they spread.
The first variant of FakePlayer was identified at the beginning of August 2010. The trojan file, called ‘RU.apk’, spreads disguised as a media player. The file is 12,927 bytes in size, and the installation package contains the following files:
res/drawable/icon.png
res/layout/main.xml
res/values/strings.xml
res/values/public.xml
META-INF/MANIFEST.MF
META-INF/CERT.RSA
META-INF/CERT.SF
classes.dex
resources.arsc
AndroidManifest.xml
During installation of the trojan, the operating system displays the following warning:

The key warning here is the last on the list: ‘Services that cost you money. Send SMS messages’. Why would an application allegedly designed to play video and audio need to send SMS messages? Clearly the authors of the program had something in mind – but what?
The APK archive contains a file called AndroidManifest.xml, which contains information about the application, including the following important string:
android.permission.SEND_SMS
If the user grants the application these privileges, once the program is installed and run, it can send SMS messages without any restrictions – exactly what the malware writers wanted.
Once installed, a ‘Movie Player’ icon (i.e. FakePlayer.a) appears in the smartphone menu:

The MoviePlayer.class file contains the main payload. Analysis shows that once the trojan is run, it creates a database called ‘movieplayer.db’, which contains a single table called ‘table1’. This table, in turn, contains a single column called ‘was’. The ‘was’ column can contain one of two values: ‘yes’ or ‘no’. The first value indicates that the trojan has already sent an SMS; the second indicates that no SMS has been sent yet. Why did the malware writers include this function? Primarily so that the trojan’s payload would be slightly less obvious.
The vast majority of mobile users in Russia have pre-paid, or pay-as-you-go, numbers – i.e. they have a certain amount of credit on their mobile account. Once the credit has been used, it’s impossible to connect to the network until the account is topped up. If the trojan were to send an unlimited number of SMS messages, credit on an account would be exhausted almost immediately, which would quickly cause the owner of the device to become suspicious.
Once the trojan has checked to see if SMS messages have been sent or not, it displays the following message:

[Translation: Wait, requesting access to the video library...]
After this, FakePlayer sends three SMS messages reading ‘798657’ to two short numbers: the first is sent to 3353, the second to 3354, and the third to 3353 again. The following screenshot shows the relevant code:
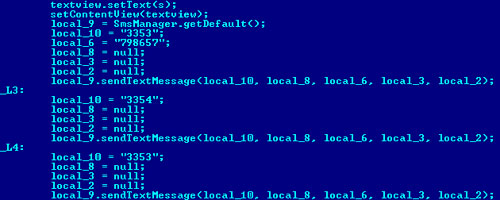
One SMS costs approximately $6, meaning that a user running the application will immediately lose $18.
Once the trojan has sent the three SMS messages, it stops running.
Luckily, the trojan can be removed using standard smartphone tools:
The second variant of FakePlayer appeared at the beginning of September 2010, approximately one month after the identification of FakePlayer.a. FakePlayer.b is almost identical to FakePlayer.a.
This time, the malicious file is called ‘pornoplayer.apk’ and is 16,833 bytes in size. The AndroidManifest.xml file contains the same string requesting permission to send SMS messages as the first version:
android.permission.SEND_SMS
Once installed, an icon called ‘Porno Player’ (i.e. FakePlayer.b) appears in the smartphone menu:
This variant of the trojan uses a different icon from FakePlayer.a (in this case, it’s a pornographic image) and a different name. In terms of code, though, almost nothing has changed: FakePlayer.b also creates a database called ‘movieplayer.db’ containing information about whether or not SMS messages have been sent. However, FakePlayer.b displays a different message on screen:

[Translation: Getting personal key...]
Almost immediately after the message has been displayed, the trojan sends four SMS messages with varied content to 7132:
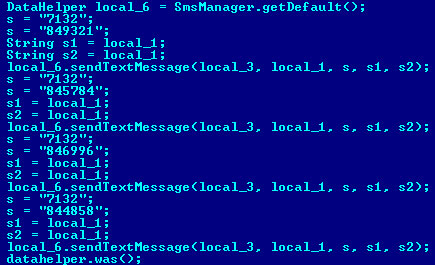
With a single SMS costing approximately $6, the user loses $24 with this variant of the trojan.
Once again, FakePlayer.b can be removed using standard Android tools:

The third variant of the trojan appeared recently, in early October, and this leads us to believe that the malware writers might be providing their victims with monthly ‘updates’. As FakePlayer.c isn’t significantly different from the other variants (just as FakePlayer.b didn’t differ significantly from FakePlayer.a), I won’t cover it in detail. FakePlayer.c uses the same icon as variant .a, the message displayed on screen has changed to

‘Podozhdite’, i.e. ‘Wait’, and the trojan sends messages both to 7132 and to a new number, 4161. The cost of each SMS message is $6.
Let’s draw some preliminary conclusions. Firstly, in terms of code, the trojan is relatively primitive. Secondly, the way in which it disguises itself (presenting itself as a legitimate application) is nothing new. However, FakePlayer is of interest not just because it was the first SMS trojan to target smartphones running Android, but also because of the way in which it spreads. This is addressed below.
When the first variant of FakePlayer appeared, it was not entirely clear how the trojan was being spread. However, the appearance of the second variant provided some answers.
As anyone in IT security knows, Internet pornography is extremely popular, and malware writers often exploit this fact to spread their malicious programs. Perhaps unsurprisingly, pornography plays an important role in the case of FakePlayer.
Today, the owners of Russian paid pornography sites offer their users very quick access to content – via an SMS message. A user who wants to gain access to the site sends an SMS message (or messages) containing a specified text to a short premium number. The user is then sent an access code to enter the site.
How do users arrive at porn sites? Clearly, a large number of them arrive via search engines. Consequently, the owners of pornographic sites have an interest in making sure that their sites are ranked near the top of the results returned by search engines for popular ‘pornographic’ searches. Search engine optimization (both ‘white’ and ‘black’) is used to do this.
The way in which a user arrives at a porn site can be summarized as follows:
User->search engine->‘pornographic’ search->porn site->send SMS->get access code->get access to site
This is what happens when a PC is used to browse the Internet. But what happens if a mobile device – for instance, a smartphone running Android – is used?
The first three links in the chain remain unchanged. But then an interesting thing happens – when clicking on a link displayed in the search results, the remote server is sent an HTTP request which contains, among other information, the User-Agent string (this contains information about the application, the operating system, and the device language).
The User-Agent string is checked on the remote server. If the site is being accessed via a PC, the porn site will be displayed. However, if the site is being accessed using a mobile device running Android, a message will be displayed telling the user to download pornoplayer.apk (i.e. FakePlayer).
The chain of events for a user accessing a porn site via a smartphone running Android looks like this:
User->search engine->‘pornographic’ search ->porn site->message saying pornoplayer.apk should be downloaded
In this way, the owner of the porn site can generate additional income – the only catch being that this income is illegal.
One interesting point came up during analysis of the sites which spread FakePlayer: the cybercriminals are using geotargetting in order to filter access requests made to the site and only present the pornoplayer.apk file if the user is coming from a Russian IP address.
However, this is not the end of the story. What if the site is accessed using, for instance, Opera Mini? Or using a standard mobile phone (i.e. non-smartphone), or a smartphone running Symbian? In this case, the user will be asked to download a file called play_ru2.jar, which is actually an SMS trojan called Trojan-SMS.J2ME.Small.aa. This trojan attempts to send SMS messages reading ‘840***’ to a familiar short number: 3354.

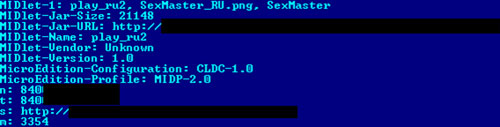
SMS messages sent to this number cost $6.
To sum up, analysis has shown that the trojan uses a relatively interesting attack method. Anyone using a mobile device to access a porn site spreading FakePlayer will be asked to download the application which corresponds to his/her smartphone or mobile phone. If the site is accessed using a device running Android, the user is asked to download pornoplayer.apk (Trojan-SMS.AndroidOS.FakePlayer.a). If the site is accessed using a standard mobile phone, or a smartphone running Symbian, the user is asked to download play_ru2.jar (Trojan.SMS.J2ME.Small.aa). By doing this, the cybercriminals are ensuring they cover the majority of mobile devices.
The evolution of FakePlayer demonstrates that Russian malware writers now see Android as a platform to target using attacks designed to make money. Although the trojan itself is primitive, and the ways in which it disguises itself and spreads are not fundamentally new, the fact that the first malware to target Android was designed to make money, and used some interesting twists in terms of propagation, was somewhat unexpected. It’s also interesting to think a bit about its authors. The trojan is supported by a familiar Russian partnerka, and the Android infection seems to be just a tiny component of a much more complex framework. (More information about this will be given in a future article.)
When malware appears using new attack methods, or which targets a previously untouched platform, one has to be prepared for the fact that, sooner or later, the number of attacks will increase (if such attacks are profitable). In the case of FakePlayer, we can see that malware writers are regularly updating the trojan and the supporting sites used to spread the malware. I would hazard a guess that this is far from the end of the story – FakePlayer is not likely to disappear any time soon.