2008-09-01
Abstract
Christoph Alme and his colleagues walk through the complete attack process of the Win32.ASF-Hijacker.A trojan, which has two different sets of victims: those affected by the trojan itself and those affected by media files altered by the trojan.
Copyright © 2008 Virus Bulletin
Shortly following the appearance of the crafted malicious ASF (Advanced Systems Format) media files that hit the road earlier this year [1], a new class of malicious ASF media file appeared with growing prevalence. The malicious files seemed to have originated from legitimate (benign) media files which were all tampered with in the same way. It took another month and some more close collaboration with fellow malware researchers to finally get hold of the nasty newbie and find the missing part of the puzzle. In this article, we walk through the complete attack process of the Win32.ASF-Hijacker.A trojan, which has two different sets of victims: those affected by the trojan itself and those affected by media files altered by the trojan.
The root of all evil lies on a ‘warez’ website in this instance. People searching for serial numbers, cracks or key generators may find themselves with a trojan downloader instead of ‘just’ the illegal content they were looking to download. In this case, the search for an activation key for the popular Nero Burning ROM program does the undesired trick. A simple hidden IFrame pointing to a page that embeds the executable as an OBJECT element triggers a drive-by download.
The downloader retrieves an XOR-obfuscated list of malware download URLs from ‘smart-security.biz’, then downloads the various malware files – one of which is the ASF-infector component. Paying respect to desktop firewalls in its very own way, the downloader first creates remote threads in either the Internet Explorer or Firefox browser and then lets this trusted process perform the download. To add to our headache, the downloader retrieves what appears to be a legitimate GIF image. The image can be displayed as normal, but the file’s header denotes the image size as 52 x 34 pixels – GIF images of this size are normally about 2 KB in size, but this one is 36 KB, so there seems to be some ‘added value’ in it. A comparison of the supposed GIF image to a set of benign GIF images of the same file size reveals only slight deviations in their data’s overall information entropy gradient (see Figure 2). The benign GIFs’ data is just as random (e.g. compressed at similar quality), but the insidious GIF shows two anomalous downward spikes that bear some resemblance to an executable’s section padding areas.
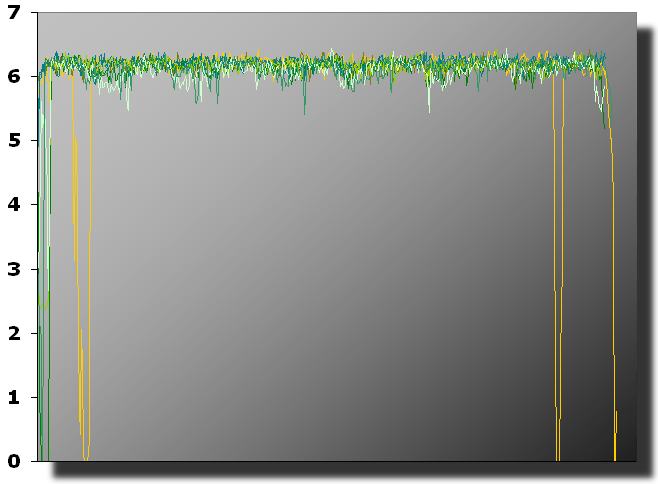
Figure 2. Information entropy gradients of insidious GIF (yellow) compared to several benign GIFs (all green).
Indeed the infector component is compressed with the PECompact runtime packer, XOR-obfuscated and appended to the GIF image. While the downloader retrieves the key to deobfuscate the infector component from the file at eight bytes from its end, an x-ray scan for a valid PE header easily reveals the embedded executable as well.
Probably as a countermeasure against desktop behaviour blockers and on-disk scanning, the infector component does not touch down on the hard disk at any time – except for infecting all your precious MP3s and videos, that is. Having deobfuscated the infector component, the trojan downloader does not drop and execute it; instead it executes the legitimate ‘winver.exe’ from the Windows installation as a suspended process. Then it replaces the complete executable image in memory by unloading winver.exe’s image via ntdll’s ZwUnmapViewOfSection() API (from user mode), mapping the infector component into the process space through WriteProcessMemory(), and finally resuming the main thread of the process.
The trojan searches for MP2, MP3 (MPEG-1 Layer 3) and ASF media files on the local hard disk and on mapped shares (all drives with a Win32 API drive type of either DRIVE_FIXED or DRIVE_REMOTE). The Windows Media Format SDK’s WMCreateReader() and WMCreateWriter() APIs are used to convert MP2 and MP3 files to ASF format first, before using the WMCreateEditor() API to create an ‘IWMMetadataEditor’ COM object and injecting a script command via a call to the AddScript() method of the ‘IWMHeaderInfo’ interface of the same COM object (see Figure 3).
The Advanced Systems Format (ASF) is a general-purpose container format for media files, used for Windows Media Video (WMV) and Windows Media Audio (WMA) files, for example. The ASF format basically consists of data chunks, each starting with a 16-byte GUID identifier followed by an unsigned 64-bit field containing the length of this chunk in bytes (including the chunk’s header). The interesting chunk, which can contain script commands [2], has the GUID ‘30 1A FB 1E 62 0B D0 11 A3 9B 00 A0 C9 03 48 F6’ (in raw byte order). Similar to the ‘HREF track’ in QuickTime movies [3], script commands are executed based on elapsed playback time. Skipping the chunk’s header and a first array with type information, a second array follows with all the script commands encoded in UTF16 Little-Endian. It is not zero-terminated, but the number of characters is stored in an unsigned 16-bit field in front of each string.
The script command that the trojan injects is named ‘URLANDEXIT’, followed by a URL that will be opened with the default browser when playing the media file. The trojan infects all ASF media files, including the converted MP3s, with ‘URLANDEXIT’ commands to point collectively to ‘isvbr.net’, a domain hosted in Hong Kong. At the time of writing, the site returns a 302 status code to then redirect to the real malicious site, currently ‘flashcodec.com’.
When done with its raid, the trojan changes a registry setting (‘URLAndExitCommandsEnabled’) and an INI file that alter the default behaviour of Windows Media Player and WinAmp, respectively. These changes will cause the compromised computer’s media player to ignore any ‘URLANDEXIT’ script commands, so the user can play their videos and audio streams without noticing any change.
So what’s the point in infecting media files on the compromised computer, but then disabling the feature that would allow the injected script commands to run? The victim of this first stage of attack acts as a proxy to spread the second stage, and they won’t notice. The user may be exchanging music files or videos on file-sharing portals or peer-to-peer networks, such as Gnutella (the network behind the popular Limewire client). As the infection remains unnoticed by the user, sooner or later they will upload files to share with others (in exchange for new files). The road to hell is paved with good intentions – sometimes illegal ones, too.
Those unlucky users who download these files and try to play them will receive a notification stating that a codec is missing and needs to be installed in order to play the video or audio stream. A well-known social-engineering trick, it is not surprising to find that this codec is actually malware. The only slight surprise is that in this case, it is not a Zlob trojan but an LDPinch password-stealer.
Probably in order to enforce compatibility with the Windows Firewall (apologies for the sarcasm), the LDPinch password-stealer adds itself to the following registry key in order to pass through it without any alerts: HKEY_LOCAL_MACHINE\SYSTEM\...\FirewallPolicy\...\AuthorizedApplications\List
Once that has been done, it can harvest all kinds of credentials – such as from the victim’s ICQ, Miranda or Trillian installations, credentials stored in FTP clients and in the Firefox and Opera web browsers, Outlook mail account credentials, and last but not least Windows Dial-Up network credentials. All the goods are delivered back through HTTP POST requests to ‘keygenguru.com’, a domain hosted in Russia.
Simply staying away from shady or illegal websites won’t necessarily keep you safe these days – with SQL injection and ‘malvertizing’ hitting many legitimate websites – but in the case of the Win32.ASF-Hijacker.A trojan, it would. Users downloading from peer-to-peer networks need to exercise caution anyway (without going into a discussion of the legal implications), but they also need to be wary of any pop-ups that appear while playing a downloaded video or audio stream: a strong indication that they should bail out quickly.
Surprisingly, the ‘missing codec’ trick remains one of the most widespread and obviously successful social-engineering tricks. As is so often the case, running one’s PC with a limited user account rather than as Administrator with full privileges would also help protect against the undesired installation of the fake codec. Doing so raises the bar for the attackers, and does not even require Windows Vista.
[1] McAfee Avert Labs Blog: Fake MP3s Running Rampant. http://www.avertlabs.com/research/blog/index.php/2008/05/06/fake-mp3s-running-rampant/.
[2] Microsoft Corp.: Using Script Commands Supported by Windows Media Player. http://msdn.microsoft.com/en-us/library/aa391231(VS.85).aspx.
[3] Alme, C.; Elser, D. Blow up your video. Virus Bulletin, December 2007, p.13. http://www.virusbtn.com/virusbulletin/archive/2007/12/vb200712-blow-up-video.