Posted by Martijn Grooten on Nov 27, 2018
 The latest Virus Bulletin web security report sees Kaspersky, Trustwave and Fortinet all achieve VBWeb certification, but also see some products struggle with the new Fallout exploit kit.
The latest Virus Bulletin web security report sees Kaspersky, Trustwave and Fortinet all achieve VBWeb certification, but also see some products struggle with the new Fallout exploit kit.
Posted by Martijn Grooten on Nov 26, 2018
 Subscribe to the re-launched Virus Bulletin eNews Newsletter to receive regular updates on the latest threat intelligence sources directly in your inbox.
Subscribe to the re-launched Virus Bulletin eNews Newsletter to receive regular updates on the latest threat intelligence sources directly in your inbox.
Posted by Martijn Grooten on Nov 22, 2018
 The Lazarus Group, which became (in)famous through the Sony Pictures breach and the WannaCry attack, is still very much active and targeting financial institutions around the world. Today we publish the VB2018 paper by AhnLab researcher Minseok (Jacky) Cha on the group's activities.
The Lazarus Group, which became (in)famous through the Sony Pictures breach and the WannaCry attack, is still very much active and targeting financial institutions around the world. Today we publish the VB2018 paper by AhnLab researcher Minseok (Jacky) Cha on the group's activities.
Posted by Martijn Grooten on Nov 16, 2018
 Today, we have published the video of a VB2018 presentation by Kaspersky Lab researchers Kurt Baumgartner and Mike Scott, who looked at the latest activity of the Turla group.
Today, we have published the video of a VB2018 presentation by Kaspersky Lab researchers Kurt Baumgartner and Mike Scott, who looked at the latest activity of the Turla group.
Posted by Martijn Grooten on Nov 13, 2018
 Today we publish the video of the VB2018 presentation by Google researcher Lukasz Siewierski on the Triada Android malware and Google's work with OEMs to remove it from infected devices.
Today we publish the video of the VB2018 presentation by Google researcher Lukasz Siewierski on the Triada Android malware and Google's work with OEMs to remove it from infected devices.
Posted by Martijn Grooten on Nov 6, 2018
Today, we publish the VB2018 paper by Masarah Paquet-Clouston (GoSecure) who looked at the supply chain behind social media fraud.
Posted by Virus Bulletin on Nov 1, 2018
 Today, we publish the VB2018 paper from Saher Naumaan (BAE Systems) who looks at malware variants that contain a wiper functionality. We also publish the recording of her presentation.
Today, we publish the VB2018 paper from Saher Naumaan (BAE Systems) who looks at malware variants that contain a wiper functionality. We also publish the recording of her presentation.
Posted by Martijn Grooten on Oct 31, 2018
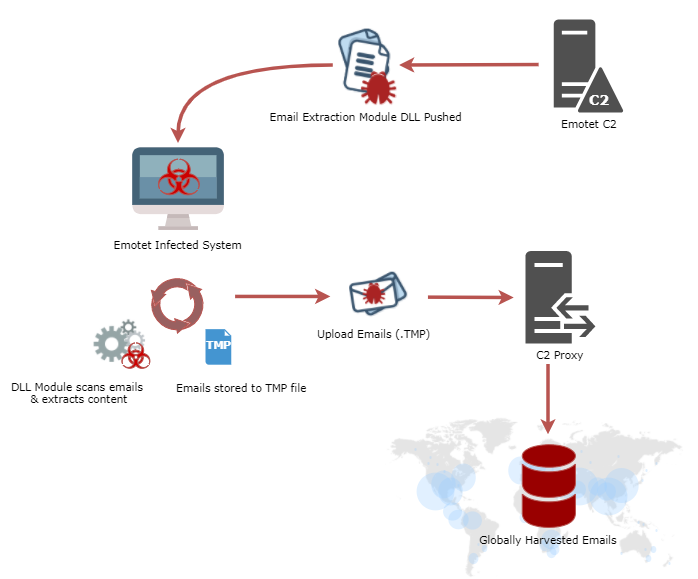 The infamous Emotet trojan has added the capability to steal full email bodies from infected machines, opening the possibilities for more targeted spam and phishing campaigns.
The infamous Emotet trojan has added the capability to steal full email bodies from infected machines, opening the possibilities for more targeted spam and phishing campaigns.
Posted by Martijn Grooten on Oct 30, 2018
 Cisco Talos researchers Paul Rascagnères and Warren Mercer were among the first to write about the Olympic Destroyer, the malware that targeted the 2018 PyeongChang Winter Olympic Games. Today, we publish the paper they presented at VB2018 about the malware; we also publish the video of their VB2018 presentation.
Cisco Talos researchers Paul Rascagnères and Warren Mercer were among the first to write about the Olympic Destroyer, the malware that targeted the 2018 PyeongChang Winter Olympic Games. Today, we publish the paper they presented at VB2018 about the malware; we also publish the video of their VB2018 presentation.
Posted by Martijn Grooten on Oct 26, 2018
 Today, we publish the VB2018 paper by Malwarebytes researcher Jérôme Segura, in which he details the shift from exploit kits to drive-by mining. We also publish the video of his VB2018 presentation.
Today, we publish the VB2018 paper by Malwarebytes researcher Jérôme Segura, in which he details the shift from exploit kits to drive-by mining. We also publish the video of his VB2018 presentation.