Posted by Martijn Grooten on Oct 2, 2017
 The recently discovered malicious CCleaner version has become one of the biggest security stories of 2017. Two researchers from Avast, the company that had recently acquired CCleaner developer Piriform, will share the results of their investigations at VB2017 in Madrid this week.
The recently discovered malicious CCleaner version has become one of the biggest security stories of 2017. Two researchers from Avast, the company that had recently acquired CCleaner developer Piriform, will share the results of their investigations at VB2017 in Madrid this week.
Posted by Martijn Grooten on Oct 2, 2017
 We preview the VB2017 paper by Kaspersky Lab researchers Juan Andrés Guerrero-Saade and Costin Raiu on fourth-party collection and its implications for attack attribution.
We preview the VB2017 paper by Kaspersky Lab researchers Juan Andrés Guerrero-Saade and Costin Raiu on fourth-party collection and its implications for attack attribution.
Posted by Martijn Grooten on Sep 29, 2017
 We preview Patrick Wardle's VB2017 paper, in which the Synack researcher analyses the mysterious OSX/FruitFly malware by setting up a custom C&C server.
We preview Patrick Wardle's VB2017 paper, in which the Synack researcher analyses the mysterious OSX/FruitFly malware by setting up a custom C&C server.
Posted by Martijn Grooten on Sep 28, 2017
More than 50 security industry experts will present conference papers to their peers at VB2017 next week, and there are several papers on the programme with a certain newsworthiness. There is still time for cybersecurity journalists to apply for a press pass.
Read morePosted by Martijn Grooten on Sep 25, 2017
 We preview the VB2017 paper by Dhia Mahjoub (OpenDNS) and Jason Passwaters (Intel471) who combine an actor-centric and a network-centric approach to analysing bulletproof hosting operations.
We preview the VB2017 paper by Dhia Mahjoub (OpenDNS) and Jason Passwaters (Intel471) who combine an actor-centric and a network-centric approach to analysing bulletproof hosting operations.
Posted by Martijn Grooten on Sep 22, 2017
 As has become tradition, VB2017 will once again see a security industry table football tournament. Register your team now for some great fun and adrenaline-filled matches in between sessions in Madrid!
As has become tradition, VB2017 will once again see a security industry table football tournament. Register your team now for some great fun and adrenaline-filled matches in between sessions in Madrid!
Posted by Martijn Grooten on Sep 21, 2017
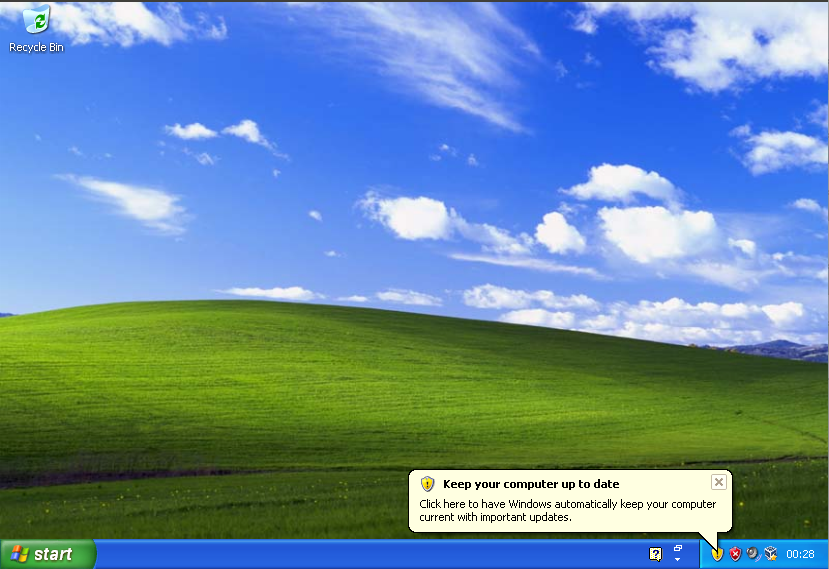 Greater Manchester Police is one of many organizations still running Windows XP on some of its systems. This is bad practice, but the case against running XP is far more subtle than we often pretend it is.
Greater Manchester Police is one of many organizations still running Windows XP on some of its systems. This is bad practice, but the case against running XP is far more subtle than we often pretend it is.
Posted by Martijn Grooten on Sep 21, 2017
 Researchers from ESET have found a new way in which the FinSpy/FinFisher 'government spyware' can infect users, details of which they will present at VB2017 in Madrid.
Researchers from ESET have found a new way in which the FinSpy/FinFisher 'government spyware' can infect users, details of which they will present at VB2017 in Madrid.
Posted by Virus Bulletin on Sep 20, 2017
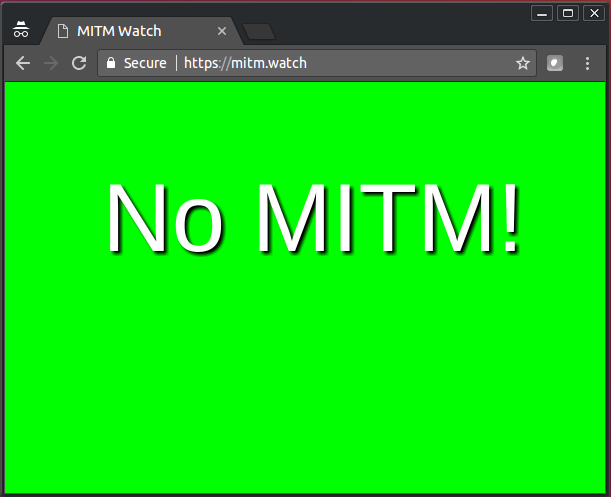 Activity monitoring by security products in general, and HTTPS traffic inspection in particular, are sensitive issues in the security community. There is a time and a place for them, VB's Martijn Grooten argues, but only when they are done right.
Activity monitoring by security products in general, and HTTPS traffic inspection in particular, are sensitive issues in the security community. There is a time and a place for them, VB's Martijn Grooten argues, but only when they are done right.
Posted by Martijn Grooten on Sep 19, 2017
 We preview the VB2017 paper by Fortinet researcher Axelle Apvrille, in which she looks at some less obvious tools for reverse engineering Android malware.
We preview the VB2017 paper by Fortinet researcher Axelle Apvrille, in which she looks at some less obvious tools for reverse engineering Android malware.