Posted by Martijn Grooten on Mar 8, 2018
 Partnering with the VB conference links your company to a successful and well-established event, demonstrates your commitment to moving the industry forward, allows you to meet potential clients, be visible to industry peers and build lasting connections.
Partnering with the VB conference links your company to a successful and well-established event, demonstrates your commitment to moving the industry forward, allows you to meet potential clients, be visible to industry peers and build lasting connections.
Posted by Martijn Grooten on Mar 7, 2018
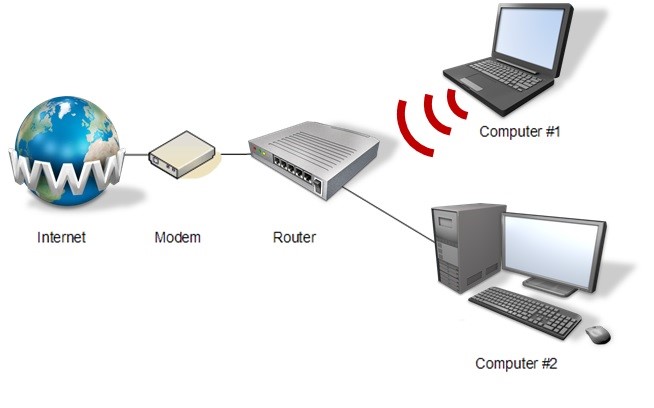 At VB2017 in Madrid, security researcher Himanshu Anand presented a paper on malware that targets routers, looking both at the topic in general and at some individual case studies. Today we publish both the paper (co-written with Chastine Menrige) and the recording of Himanshu's presentation.
At VB2017 in Madrid, security researcher Himanshu Anand presented a paper on malware that targets routers, looking both at the topic in general and at some individual case studies. Today we publish both the paper (co-written with Chastine Menrige) and the recording of Himanshu's presentation.
Posted by Martijn Grooten on Mar 6, 2018
 In recent months, some malicious spam campaigns have been spreading via the systems of Mailchimp, a well-known email service provider - a tactic which may give the campaigns a slightly higher success rate.
In recent months, some malicious spam campaigns have been spreading via the systems of Mailchimp, a well-known email service provider - a tactic which may give the campaigns a slightly higher success rate.
Posted by Martijn Grooten on Mar 1, 2018
 Though many of the IT security issues we face are global, there is a noticeable difference in the threats faced in various countries and regions, as well as in the ways they are dealt with. At VB2017, we heard from Tyrus Kamau about the state of cybersecurity in Kenya. Today, we publish the video of Tyrus's talk.
Though many of the IT security issues we face are global, there is a noticeable difference in the threats faced in various countries and regions, as well as in the ways they are dealt with. At VB2017, we heard from Tyrus Kamau about the state of cybersecurity in Kenya. Today, we publish the video of Tyrus's talk.
Posted by Martijn Grooten on Feb 21, 2018
 A report on the number of cyber attacks faced by UK local authorities is a good example of how the large numbers seen in many reports on security are rather meaningless.
A report on the number of cyber attacks faced by UK local authorities is a good example of how the large numbers seen in many reports on security are rather meaningless.
Posted by Martijn Grooten on Feb 20, 2018
 The UK's National Cyber Security Centre (NCSC) has provided helpful and practical advice on preventing and detecting lateral movement by an attacker within a network.
The UK's National Cyber Security Centre (NCSC) has provided helpful and practical advice on preventing and detecting lateral movement by an attacker within a network.
Posted by Martijn Grooten on Feb 17, 2018
 If you are considering submitting a proposal for a talk to VB2018 and you're not familiar with the event, you may find it useful to know what kind of people attend the conference.
If you are considering submitting a proposal for a talk to VB2018 and you're not familiar with the event, you may find it useful to know what kind of people attend the conference.
Posted by Martijn Grooten on Feb 15, 2018
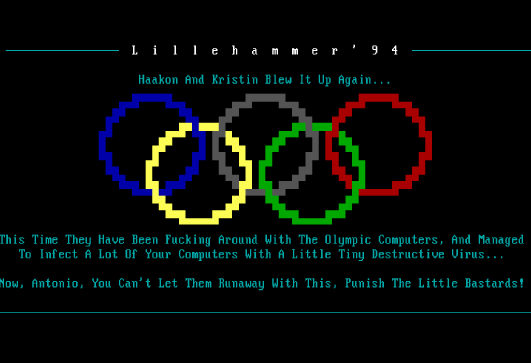 An unattributed malware attack has disrupted some computer systems of the 2018 Winter Olympics. In 1994, a computer virus also targeted the Winter Olympics.
An unattributed malware attack has disrupted some computer systems of the 2018 Winter Olympics. In 1994, a computer virus also targeted the Winter Olympics.
Posted by Martijn Grooten on Feb 12, 2018
 Thousands of websites, including many sites of government organisations in the UK, the US and Sweden, were recently found to have been serving a cryptocurrency miner. More interesting than the incident itself, though, are the lessons that can be learned from it.
Thousands of websites, including many sites of government organisations in the UK, the US and Sweden, were recently found to have been serving a cryptocurrency miner. More interesting than the incident itself, though, are the lessons that can be learned from it.
Posted by Martijn Grooten on Feb 9, 2018
 An article by security researcher Collin Anderson reopens the debate on whether publishing threat analyses is always in the public interest.
An article by security researcher Collin Anderson reopens the debate on whether publishing threat analyses is always in the public interest.