Often unbeknownst to network administrators, many company networks are used to download child sexual abuse material. In a paper presented at VB2019 in London, NetClean’s Richard Matti and Anna Creutz looked at this problem and what companies can do, ultim…
Why companies need to focus on a problem they do not know they have
Read the paper (HTML)
Download the paper (PDF)
It is one of the worst things on the Internet: child… https://www.virusbulletin.com/blog/2020/03/vb2019-paper-why-companies-need-focus/
Here at VB we are keeping a close eye on the global situation regarding the COVID-19 outbreak and the various travel restrictions and health advice, but in the meantime planning and arrangements for VB2020 are going ahead as usual, including the selection…
Like everyone around the world, we at Virus Bulletin have been closely following the news about the COVID-19 outbreak. Our team is spread throughout Europe (UK, Italy, Hungary and… https://www.virusbulletin.com/blog/2020/03/vb2020-current-situation/
Operational technology, the mission critical IT in ICS, shares many similarities with traditional IT systems, but also some crucial differences. During the Threat Intelligence Practitioners’ Summit at VB2019, Dragos cyber threat intelligence analyst Selen…
Cyber attacks on industrial control systems (ICS) include the well-known stories of Stuxnet and BlackEnergy and such attacks appear to be getting more prevalent. Late last year, a… https://www.virusbulletin.com/blog/2020/03/vb2019-presentation-nexus-between-ot-and-it-threat-intelligence/
In a paper presented at VB2019 in London, researchers fron the Financial Security Institute detailed the tools and activities used by the APT group 'Kimsuky', some of which they were able to analyse through OpSec failures by the group. Today, we publish t…
Are you tracking an APT group? Have you fought their targeting of your organisation? Why not submit a paper for VB2020 in Dublin, Ireland, the deadline for which is Sunday 15… https://www.virusbulletin.com/blog/2020/03/vb2019-paper-kimsuky-group-tracking-king-spear-phishing/
First advertised as an information stealer and keylogger when it appeared in underground forums in 2015, LokiBot has added various capabilities over the years and has affected many users worldwide. In a new paper researcher Aditya Sood analyses the URL st…
If you have some research you'd like to share with the security community, we'd love to hear from you: the call for papers for VB2020 (Dublin, 30 Sept to 2 Oct 2020) remains open… https://www.virusbulletin.com/blog/2020/02/new-paper-lokibot-dissecting-cc-panel-deployments/
Attor is a newly discovered cyber-espionage platform, use of which dates back to at least 2014 and which focuses on diplomatic missions and governmental institutions. Details of Attor were presented at VB2019 in London by ESET researcher Zuzana Hromcová. …
Attor is a newly discovered cyber-espionage platform, use of which dates back to at least 2014 and which focuses on diplomatic missions and governmental institutions. The modular… https://www.virusbulletin.com/blog/2020/02/vb2019-presentation-attor-spy-platform-curious-gsm-fingerprinting/
At VB2019 in London, Fortinet researcher Axelle Apvrille presented a paper co-written with Aamir Lakhani that looked at the threats faced by those who use medical IoT devices to help manage their diabetes. Today we publish the researchers' paper, as well …
Medical IoT for diabetes and cybercrime
Read the paper (HTML)
Download the paper (PDF)
It is estimated that between 8% and 9% of the population worldwide suffers with some… https://www.virusbulletin.com/blog/2020/01/vb2019-paper-medical-iot-diabetes-and-cybercrime/
With the call for papers for VB2020 currently open, we explain why, whether you've never presented before or you're a conference circuit veteran, if you have some interesting research to share with the community we want to hear from you!
Over almost three decades, the Virus Bulletin Conference has built a reputation as a conference that produces solid content. While you might be forgiven for thinking this comes… https://www.virusbulletin.com/blog/2020/02/why-we-encourage-you-submit-paper-vb2020/
In a VB2019 paper Avast researchers Jan Sirmer, Luigino Camastra and Adolf Středa revealed full details of the Rietspoof malware. Today we publish their paper and the recording of the presentation given by Jan and Luigino in London.
Spoofing in the reeds with Rietspoof
Read the paper (HTML)
Download the paper (PDF)
The Call for Papers for VB2020 in Dublin is open! Submit your abstract before… https://www.virusbulletin.com/blog/2020/01/vb2019-paper-spoofing-reeds-rietspoof/
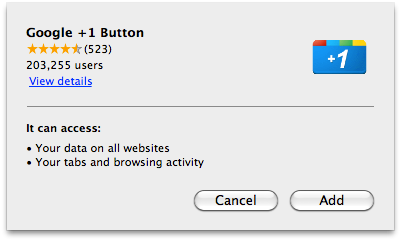 Google has made a subtle change to its Chrome browser, banning the inline installation of new extensions, thus making it harder for malware authors to trick users into unwittingly installing malicious extensions.
Google has made a subtle change to its Chrome browser, banning the inline installation of new extensions, thus making it harder for malware authors to trick users into unwittingly installing malicious extensions.
 We publish a paper by researchers from Quick Heal Security Labs in India, who study the EternalBlue and DoublePulsar exploits in full detail.
We publish a paper by researchers from Quick Heal Security Labs in India, who study the EternalBlue and DoublePulsar exploits in full detail.
 Several VB2018 papers deal explicitly or implicitly with threats that have been attributed to North Korean actors.
Several VB2018 papers deal explicitly or implicitly with threats that have been attributed to North Korean actors.
 The domain of the little-used SpamCannibal DNS blacklist had expired, resulting in it effectively listing every single IP address.
The domain of the little-used SpamCannibal DNS blacklist had expired, resulting in it effectively listing every single IP address.
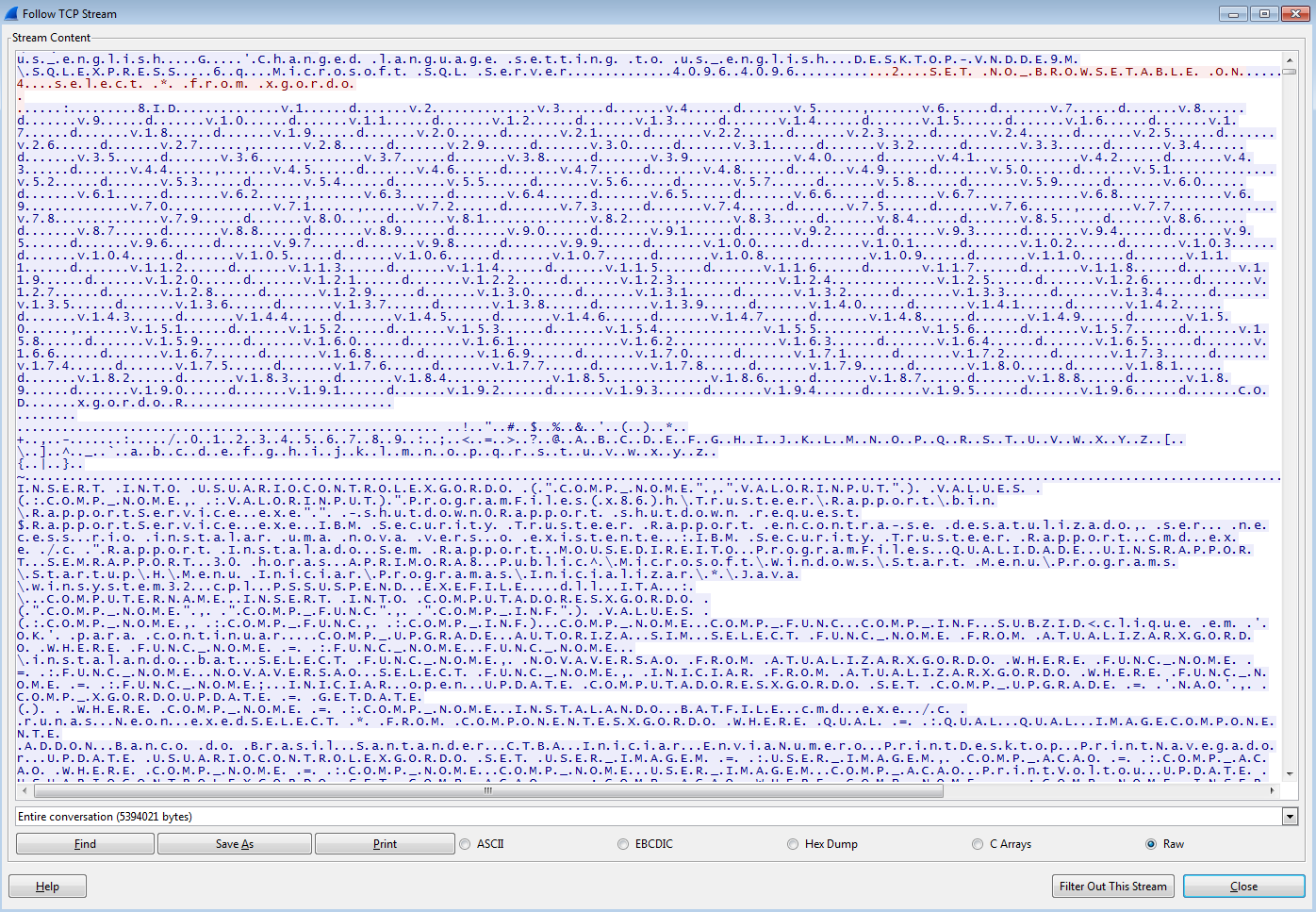 Researchers at IBM X-Force have discovered MnuBot, a banking trojan targeting users in Brazil, which is noteworthy for using SQL Server for command and control communication.
Researchers at IBM X-Force have discovered MnuBot, a banking trojan targeting users in Brazil, which is noteworthy for using SQL Server for command and control communication.
 The 68-byte EICAR test file plays as important a role today as it did 19 years ago. In this week's Throwback Thursday we look back at a VB99 conference paper in which Randy Abrams described how this 'miracle tool' worked and how it could be used.
The 68-byte EICAR test file plays as important a role today as it did 19 years ago. In this week's Throwback Thursday we look back at a VB99 conference paper in which Randy Abrams described how this 'miracle tool' worked and how it could be used.
 A new piece of cryptocurrency-mining malware on macOS has been found to use the popular XMRig miner.
A new piece of cryptocurrency-mining malware on macOS has been found to use the popular XMRig miner.
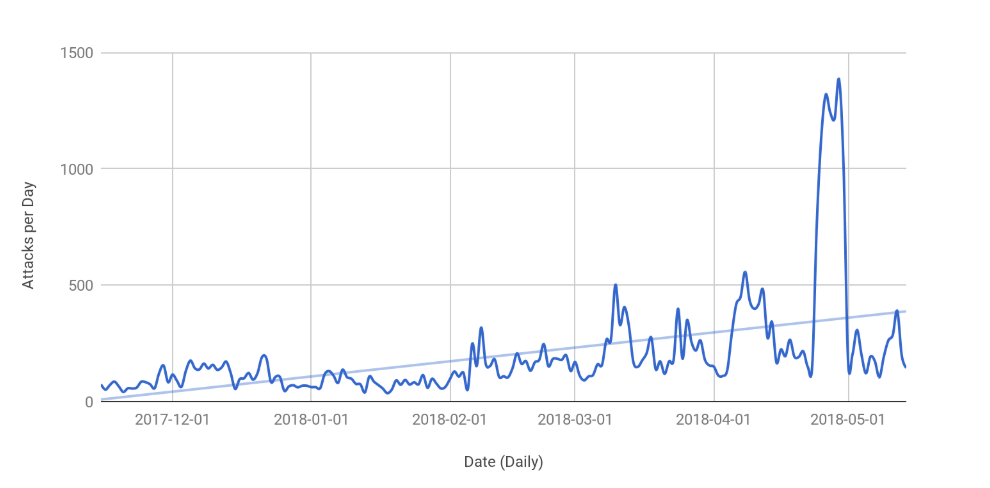 CDN provider Cloudflare reports an increase in DDoS attacks targeting layer 7 and focusing on exhausting server resources rather than sending large volumes of data. This fits in a wider trend.
CDN provider Cloudflare reports an increase in DDoS attacks targeting layer 7 and focusing on exhausting server resources rather than sending large volumes of data. This fits in a wider trend.
 Through fake social media accounts, users were tricked into installing an Android application that was actually a mobile version of the FinFisher spyware.
Through fake social media accounts, users were tricked into installing an Android application that was actually a mobile version of the FinFisher spyware.
 The Hide'n'Seek IoT botnet has received an update to make its infection persist on infected devices beyond a restart.
The Hide'n'Seek IoT botnet has received an update to make its infection persist on infected devices beyond a restart.