Posted by Martijn Grooten on Sep 21, 2018
 In recent years, car hacking has evolved from a mostly theoretical research field involving giggling researchers and scared journalists, to one that actually concerns car owners and manufacturers. On today's blog we preview two VB2018 papers, by Inbar Raz and Spencer Hsieh, that look at the subject of hacking cars.
In recent years, car hacking has evolved from a mostly theoretical research field involving giggling researchers and scared journalists, to one that actually concerns car owners and manufacturers. On today's blog we preview two VB2018 papers, by Inbar Raz and Spencer Hsieh, that look at the subject of hacking cars.
Posted by Virus Bulletin on Sep 20, 2018
 In a guest blog post by VB2018 gold partner Kaspersky Lab, Costin Raiu, Director of the company's Global Research and Analysis Team, looks critically at the 'A' in APT.
In a guest blog post by VB2018 gold partner Kaspersky Lab, Costin Raiu, Director of the company's Global Research and Analysis Team, looks critically at the 'A' in APT.
Posted by Martijn Grooten on Sep 19, 2018
 Today, we preview three VB2018 presentations that look at threats against civil society in general and the use of commercial spyware by governments for this purpose in particular.
Today, we preview three VB2018 presentations that look at threats against civil society in general and the use of commercial spyware by governments for this purpose in particular.
Posted by Martijn Grooten on Sep 18, 2018
 Today we preview the VB2018 paper by Saher Naumaan (BAE Systems Applied Intelligence) on the use of wipers in APT attacks.
Today we preview the VB2018 paper by Saher Naumaan (BAE Systems Applied Intelligence) on the use of wipers in APT attacks.
Posted by Martijn Grooten on Sep 17, 2018
 The VB2018 programme is packed with a wide range of security topics featuring speakers from all around the world. Today we preview two of them: one by Qihoo 360 researchers on tracking variants of Mirai and one by researchers from Bitdefender on the peer-to-peer Hide'n'Seek botnet.
The VB2018 programme is packed with a wide range of security topics featuring speakers from all around the world. Today we preview two of them: one by Qihoo 360 researchers on tracking variants of Mirai and one by researchers from Bitdefender on the peer-to-peer Hide'n'Seek botnet.
Posted by Martijn Grooten on Sep 10, 2018
 We are excited to announce the final additions to the VB2018 programme in the form of 10 'last-minute' papers covering up-to-the-minute research and hot topics and two more invited talks.
We are excited to announce the final additions to the VB2018 programme in the form of 10 'last-minute' papers covering up-to-the-minute research and hot topics and two more invited talks.
Posted by Martijn Grooten on Sep 7, 2018
 At VB2018, AhnLab researcher Minseok Cha will look at activities of the Lazarus Group on the Korean peninsula going back as early as April 2011.
At VB2018, AhnLab researcher Minseok Cha will look at activities of the Lazarus Group on the Korean peninsula going back as early as April 2011.
Posted by Virus Bulletin on Sep 6, 2018
 Paul Baccas reviews Bruce Schneier's latest thought-provoking book, 'Click Here to Kill Everybody'.
Paul Baccas reviews Bruce Schneier's latest thought-provoking book, 'Click Here to Kill Everybody'.
Posted by Martijn Grooten on Sep 3, 2018
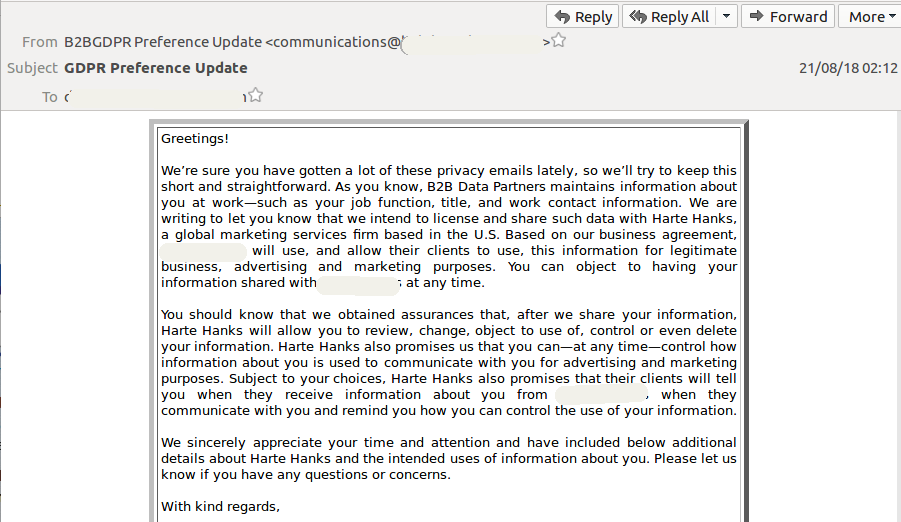 A brief analysis by Recorded Future suggests that the volume of spam and new domain registrations hasn't increased since the GDPR came into effect.
A brief analysis by Recorded Future suggests that the volume of spam and new domain registrations hasn't increased since the GDPR came into effect.
Posted by Martijn Grooten on Aug 29, 2018
 VB is thrilled to announce the programme of the first International Threat Intelligence Summit that will form an integral part of the VB2018 conference programme.
VB is thrilled to announce the programme of the first International Threat Intelligence Summit that will form an integral part of the VB2018 conference programme.