Posted by Martijn Grooten on Jun 29, 2017
Whether you call it Petya, NotPetya, Nyetya or Petna, there are still many mysteries surrounding the malware that has been causing havoc around the world.
Read morePosted by Martijn Grooten on Jun 28, 2017
 This week, the Early Bird discount for VB2017 comes to an end - so, for a 10% saving on the cost of full price registration, make sure you register now!
This week, the Early Bird discount for VB2017 comes to an end - so, for a 10% saving on the cost of full price registration, make sure you register now!
Posted by Martijn Grooten on Jun 23, 2017
Last year, Kaspersky Lab researcher Santiago Pontiroli and PwC's Bart Parys presented a VB2016 paper analysing the malicious threats faced by users of the Steam online gaming platform, and highlighting how organized criminals are making money with these profitable schemes. Today, we publish the paper.
Read morePosted by Martijn Grooten on Jun 22, 2017
 Researchers at Cisco have published a paper describing how it may be possible to use machine learning to distinguish malware command-and-control traffic using TLS from regular enterprise traffic, and to classify malware families based on their encrypted C&C traffic.
Researchers at Cisco have published a paper describing how it may be possible to use machine learning to distinguish malware command-and-control traffic using TLS from regular enterprise traffic, and to classify malware families based on their encrypted C&C traffic.
Posted by Martijn Grooten on Jun 20, 2017
After five years of exploitation in a wide variety of attacks, CVE-2012-0158 may have found a successor in CVE-2017-0199, which is taking the Office exploit scene by storm.
Read morePosted by Martijn Grooten on Jun 19, 2017
 Virus Bulletin was a proud sponsor of BSides London 2017 - Martijn Grooten reports on a great event.
Virus Bulletin was a proud sponsor of BSides London 2017 - Martijn Grooten reports on a great event.
Posted by Martijn Grooten on Jun 15, 2017
It is well known that the problem of cybersecurity is a global one that affects users worldwide - but it's also one that has some unique local flavours. With speakers representing at least 24 countries, VB2017 is one of the most international security conferences on the circuit, allowing attendees to hear the viewpoints of experts from around the world. Register before 1 July and receive a 10% Early Bird discount.
Read morePosted by Martijn Grooten on Jun 12, 2017
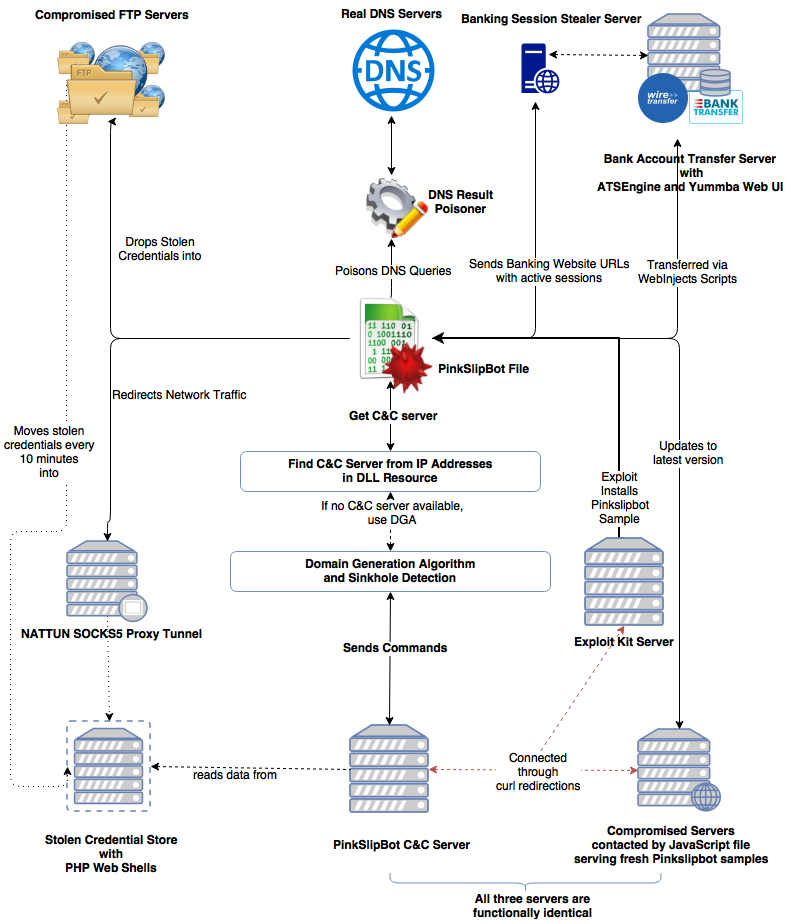 Qakbot or Qbot, is a banking trojan that makes the news every once in a while and was the subject of a VB2016 paper by Intel Security researchers Sanchit Karve, Guilherme Venere and Mark Olea. In it, they provided a detailed analysis of the Pinkslipbot/Qakbot trojan and its then latest campaign. Their full paper is now available to download or read online.
Qakbot or Qbot, is a banking trojan that makes the news every once in a while and was the subject of a VB2016 paper by Intel Security researchers Sanchit Karve, Guilherme Venere and Mark Olea. In it, they provided a detailed analysis of the Pinkslipbot/Qakbot trojan and its then latest campaign. Their full paper is now available to download or read online.
Posted by Martijn Grooten on Jun 2, 2017
 VB Editor Martijn Grooten reviews Finn Brunton's book 'Spam: A Shadow History of the Internet'.
VB Editor Martijn Grooten reviews Finn Brunton's book 'Spam: A Shadow History of the Internet'.
Posted by Martijn Grooten on Jun 1, 2017
 Virus Bulletin is proud to be a Silver sponsor of BSides London next week; we look forward to the event and to meeting many security professionals.
Virus Bulletin is proud to be a Silver sponsor of BSides London next week; we look forward to the event and to meeting many security professionals.