Posted by Martijn Grooten on Nov 22, 2019
 A VB2019 paper by FireEye researcher Daniel Kapellmann Zafra explained how open source intelligence (OSINT) can be used to learn crucial details of the inner workings of many a system. Today we publish Daniel's paper and the recording of his presentation.
A VB2019 paper by FireEye researcher Daniel Kapellmann Zafra explained how open source intelligence (OSINT) can be used to learn crucial details of the inner workings of many a system. Today we publish Daniel's paper and the recording of his presentation.
Posted by Martijn Grooten on Nov 21, 2019
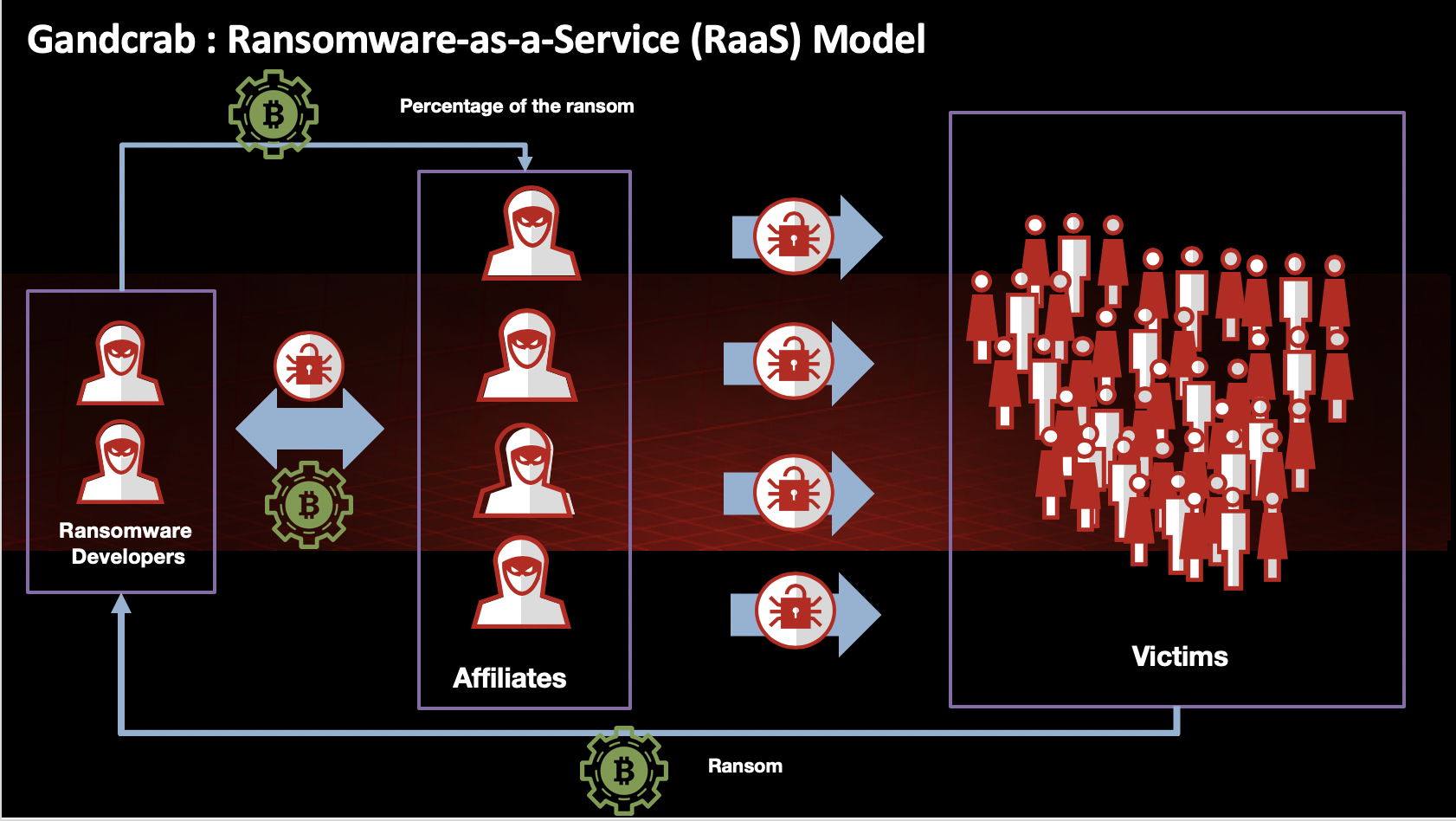 Though active for not much longer than a year, GandCrab had been one of the most successful ransomware operations. In a paper presented at VB2019 in London, McAfee researchers John Fokker and Alexandre Mundo looked at the malware code, its evolution and the affiliate scheme behind it. Today we publish both their paper and the recording of their presentation.
Though active for not much longer than a year, GandCrab had been one of the most successful ransomware operations. In a paper presented at VB2019 in London, McAfee researchers John Fokker and Alexandre Mundo looked at the malware code, its evolution and the affiliate scheme behind it. Today we publish both their paper and the recording of their presentation.
Posted by Martijn Grooten on Nov 18, 2019
At VB2019 in London, Check Point researchers Aseel Kayal and Lotem Finkelstein presented a paper detailing an Iranian operation they named 'Domestic Kitten' that used Android apps for targeted surveillance. Today we publish their paper and the video of their presentation.
Posted by Martijn Grooten on Nov 18, 2019
 At VB2019 in London, LINE's HeungSoo Kang explained how cryptocurrency exchanges had been attacked using Firefox zero-days. Today, we publish the video of his presentation.
At VB2019 in London, LINE's HeungSoo Kang explained how cryptocurrency exchanges had been attacked using Firefox zero-days. Today, we publish the video of his presentation.
Posted by Martijn Grooten on Nov 7, 2019
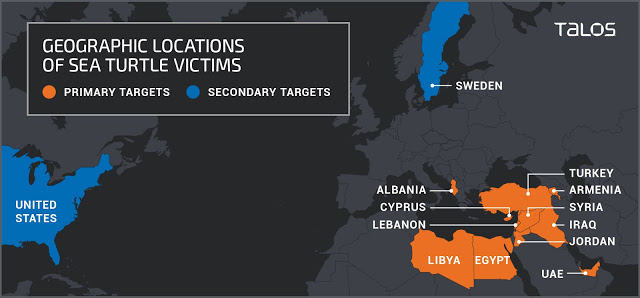 In a paper presented at VB2019, Cisco Talos researchers Warren Mercer and Paul Rascagneres looked at two recent attacks against DNS infrastructure: DNSpionage and Sea Turtle. Today we publish their paper and the recording of their presentation.
In a paper presented at VB2019, Cisco Talos researchers Warren Mercer and Paul Rascagneres looked at two recent attacks against DNS infrastructure: DNSpionage and Sea Turtle. Today we publish their paper and the recording of their presentation.
Posted by Martijn Grooten on Nov 6, 2019
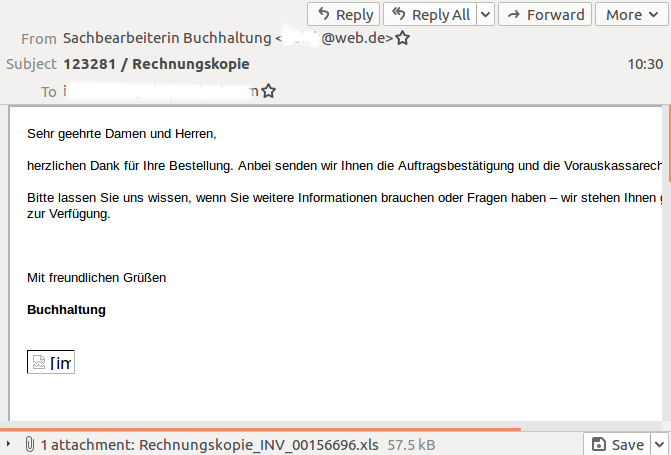 VB has analysed a malicious spam campaign targeting German-speaking users with obfuscated Excel malware that would likely download Dridex but that mostly stood out through its size.
VB has analysed a malicious spam campaign targeting German-speaking users with obfuscated Excel malware that would likely download Dridex but that mostly stood out through its size.
Posted by Martijn Grooten on Nov 5, 2019
 We publish a paper by researchers from ESTsecurity in South Korea, who describe a fuzzy hashing algorithm for clustering Android malware datasets.
We publish a paper by researchers from ESTsecurity in South Korea, who describe a fuzzy hashing algorithm for clustering Android malware datasets.
Posted by Martijn Grooten on Nov 4, 2019
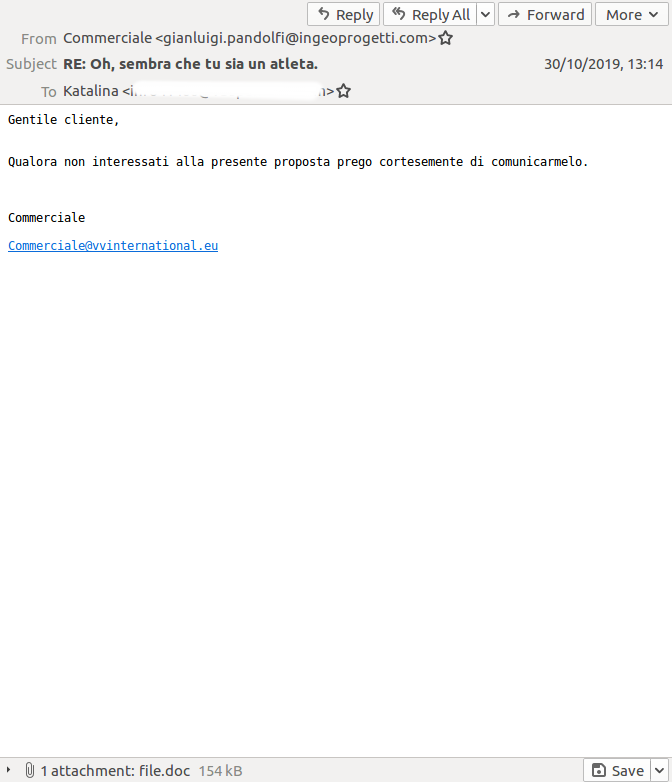 Having returned from a summer hiatus, Emotet is back targeting inboxes and, as seen in the VBSpam test lab, doing a better job than most other malicious campaigns at bypassing email security products.
Having returned from a summer hiatus, Emotet is back targeting inboxes and, as seen in the VBSpam test lab, doing a better job than most other malicious campaigns at bypassing email security products.
Posted by Martijn Grooten on Nov 1, 2019
 Those working in the field of infosec are often faced with ethical dilemmas that are impossible to avoid. Today, we publish a VB2019 paper by Kaspersky researcher Ivan Kwiatkowski looking at ethics in infosec as well as the recording of Ivan's presentation.
Those working in the field of infosec are often faced with ethical dilemmas that are impossible to avoid. Today, we publish a VB2019 paper by Kaspersky researcher Ivan Kwiatkowski looking at ethics in infosec as well as the recording of Ivan's presentation.
Posted by Martijn Grooten on Oct 31, 2019
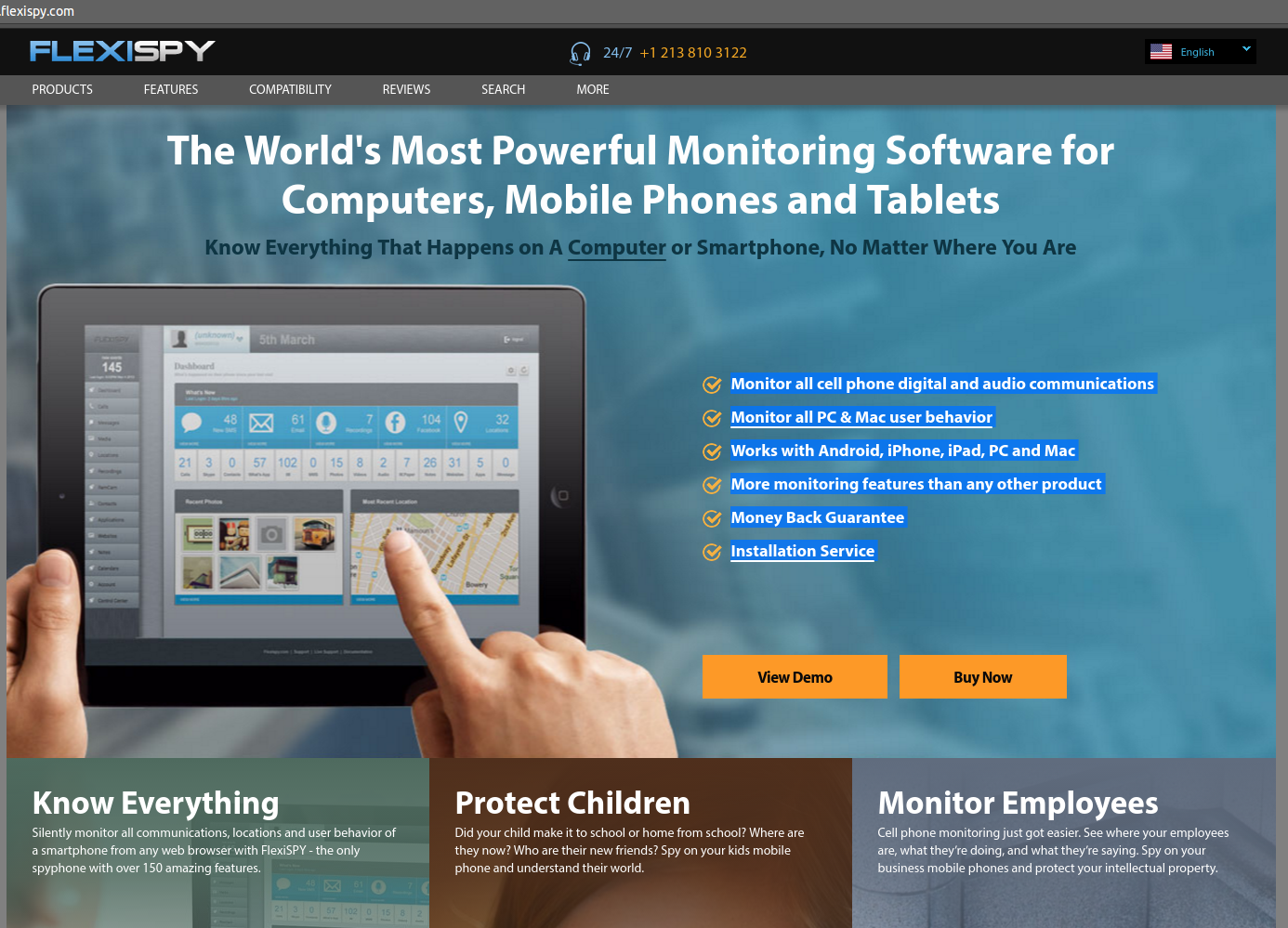 Malware used in domestic abuse situations is a growing threat, and the standard way for anti-virus products to handle such malware may not be good enough. But that doesn't mean there isn't an important role for anti-virus to play.
Malware used in domestic abuse situations is a growing threat, and the standard way for anti-virus products to handle such malware may not be good enough. But that doesn't mean there isn't an important role for anti-virus to play.