Posted by Martijn Grooten on Jul 5, 2016
 In a new paper published by Virus Bulletin, Sophos researcher Gabor Szappanos takes a look at the KeyBase keylogger, sold as a commercial product and popular among cybercriminals who use it in Office exploit kits.
In a new paper published by Virus Bulletin, Sophos researcher Gabor Szappanos takes a look at the KeyBase keylogger, sold as a commercial product and popular among cybercriminals who use it in Office exploit kits.
Posted by Martijn Grooten on Jun 28, 2016
 VB2016, the 26th International Virus Bulletin conference, is an excellent reason to go to Denver, Colorado in the first week of October. But there is another reason to come to Denver: BSides Denver, which will take place the day after VB2016, on Saturday 8 October 2016.
VB2016, the 26th International Virus Bulletin conference, is an excellent reason to go to Denver, Colorado in the first week of October. But there is another reason to come to Denver: BSides Denver, which will take place the day after VB2016, on Saturday 8 October 2016.
Posted by Virus Bulletin on Jun 13, 2016
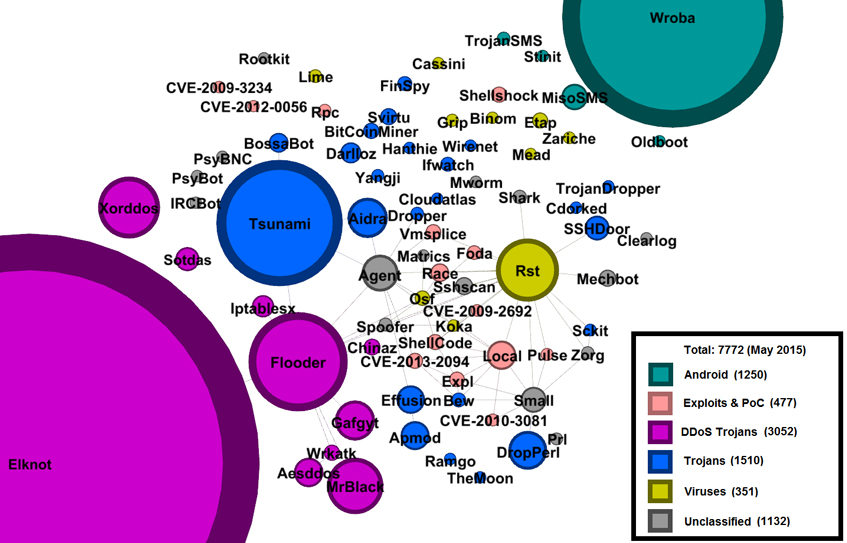 In their VB2015 paper, Peter Kálnai and Jaromír Hořejší look at the current state of DDoS trojans forming covert botnets on unsuspecting systems. The paper provides a technical analysis of the most important malware families, focusing on infection methods, dynamic behaviour, C&C communication, obfuscation techniques, advanced methods of persistence and stealth, and elimination of rivals.
In their VB2015 paper, Peter Kálnai and Jaromír Hořejší look at the current state of DDoS trojans forming covert botnets on unsuspecting systems. The paper provides a technical analysis of the most important malware families, focusing on infection methods, dynamic behaviour, C&C communication, obfuscation techniques, advanced methods of persistence and stealth, and elimination of rivals.
Posted by Helen Martin on Jun 2, 2016
 This week, well known and universally respected industry guru Mikko Hyppönen celebrates his 25th anniversary of working at F-Secure (formerly known as Data Fellows). VB takes a look back in the archives at two articles published in 1994: an "insight" into the life and work of the then rising star of the anti-virus world, and a virus analysis penned by the man himself.
This week, well known and universally respected industry guru Mikko Hyppönen celebrates his 25th anniversary of working at F-Secure (formerly known as Data Fellows). VB takes a look back in the archives at two articles published in 1994: an "insight" into the life and work of the then rising star of the anti-virus world, and a virus analysis penned by the man himself.
Posted by Helen Martin on Jun 1, 2016
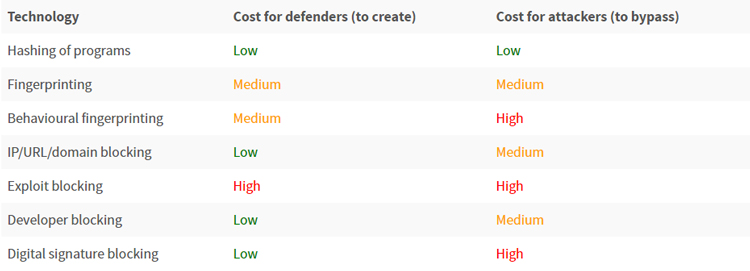 Financial pressure can be a proactive and potentially very effective tool in making our computer ecosystems safer. By cleverly employing various trust metrics and technologies such as digital signing, watermarking, and public-key infrastructure in strategically selected places, we can encourage good behaviours and punish bad ones. In his VB2015 paper, Igor Muttik analyses and gives examples of technologies (certificates, credentials, etc.) to de-incentivize bad behaviours in several ecosystems (Windows, Android, iOS).
Financial pressure can be a proactive and potentially very effective tool in making our computer ecosystems safer. By cleverly employing various trust metrics and technologies such as digital signing, watermarking, and public-key infrastructure in strategically selected places, we can encourage good behaviours and punish bad ones. In his VB2015 paper, Igor Muttik analyses and gives examples of technologies (certificates, credentials, etc.) to de-incentivize bad behaviours in several ecosystems (Windows, Android, iOS).
Posted by Martijn Grooten on May 26, 2016
Virus Bulletin has relaunched its security job vacancy service and added a new section, in which job seekers can advertise their skills and experience.
Read morePosted by Helen Martin on May 26, 2016
 In October 1994, a new multi-partite virus appeared, using some of the techniques developed by the Dark Avenger in Commander_Bomber. As if this were not enough, the One_Half virus could also encrypt vital parts of the fixed disk. Eugene Kaspersky provided a detailed analysis.
In October 1994, a new multi-partite virus appeared, using some of the techniques developed by the Dark Avenger in Commander_Bomber. As if this were not enough, the One_Half virus could also encrypt vital parts of the fixed disk. Eugene Kaspersky provided a detailed analysis.
Posted by Martijn Grooten on May 9, 2016
 Support scam pop-ups presented through malicious advertisements show that, next to vulnerable end points, gullible users remain an easy source of money for online criminals.
Support scam pop-ups presented through malicious advertisements show that, next to vulnerable end points, gullible users remain an easy source of money for online criminals.
Posted by Martijn Grooten on May 6, 2016
 Many websites put barriers in front of visitors who use the Tor network. If we want to make the web more accessible through Tor, we need to be honest about why this is done, rather than cry wolf about a dislike for privacy, Martijn Grooten says.
Many websites put barriers in front of visitors who use the Tor network. If we want to make the web more accessible through Tor, we need to be honest about why this is done, rather than cry wolf about a dislike for privacy, Martijn Grooten says.
Posted by Martijn Grooten on Apr 28, 2016
 A new paper by CYREN researcher Lordian Mosuela takes a close look at Gatak, or Stegoloader, a piece of malware that was discovered last year and that is controlled via malicious code embedded in a PNG image, a technique known as steganography.
A new paper by CYREN researcher Lordian Mosuela takes a close look at Gatak, or Stegoloader, a piece of malware that was discovered last year and that is controlled via malicious code embedded in a PNG image, a technique known as steganography.