Posted by Martijn Grooten on Aug 28, 2018
 Designing smart contracts is hard: we preview a VB2018 paper on the blockchain-based platform Ethereum, that describes both how the technology works and how a number of security issues inherent to the platform have led to various high-profile and often very costly hacks.
Designing smart contracts is hard: we preview a VB2018 paper on the blockchain-based platform Ethereum, that describes both how the technology works and how a number of security issues inherent to the platform have led to various high-profile and often very costly hacks.
Posted by Martijn Grooten on Aug 27, 2018
At VB2017, IBM Trusteer researcher Omer Agmon, presented a 'last-minute' paper in which he analysed the Client Maximum trojan, which targets Brazilian users of online banking. Today, we release the recording of his presentation.
Read morePosted by Martijn Grooten on Aug 21, 2018
 For those organizations working for the public good, security vendors are often willing to offer their services for free, or for very low cost.
For those organizations working for the public good, security vendors are often willing to offer their services for free, or for very low cost.
Posted by Martijn Grooten on Aug 17, 2018
 At VB2018, Google researcher Maddie Stone will present an analysis of the multi-layered 'WeddingCake' anti-analysis library used by many Android malware families.
At VB2018, Google researcher Maddie Stone will present an analysis of the multi-layered 'WeddingCake' anti-analysis library used by many Android malware families.
Posted by Martijn Grooten on Aug 15, 2018
 At VB2018, Malwarebytes researcher Jérôme Segura will discuss the rise of drive-by cryptocurrency mining, explaining how it works and putting it in the broader context of changes in the cybercrime landscape.
At VB2018, Malwarebytes researcher Jérôme Segura will discuss the rise of drive-by cryptocurrency mining, explaining how it works and putting it in the broader context of changes in the cybercrime landscape.
Posted by Martijn Grooten on Aug 14, 2018
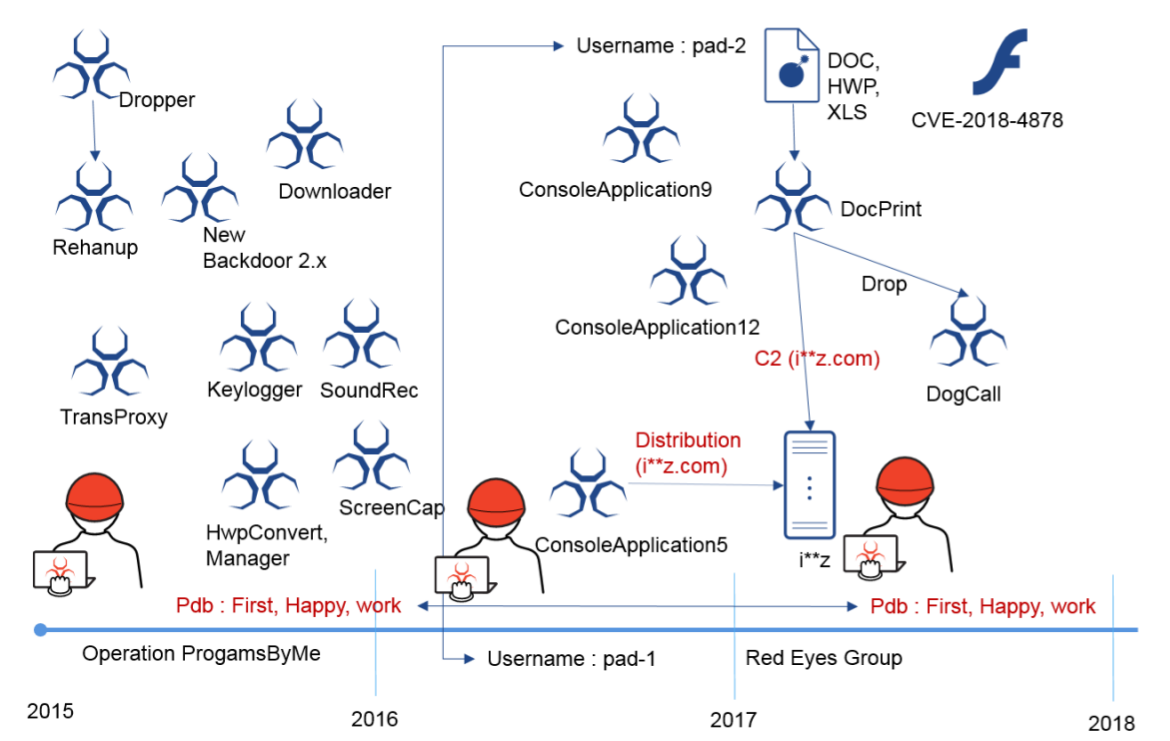 A research paper by AhnLab researcher Minseok Cha looks at the activities of the Red Eyes threat group (also known as Group 123 and APT 37), whose targets include North Korean defectors, as well as journalists and human rights defenders focused on North Korea.
A research paper by AhnLab researcher Minseok Cha looks at the activities of the Red Eyes threat group (also known as Group 123 and APT 37), whose targets include North Korean defectors, as well as journalists and human rights defenders focused on North Korea.
Posted by Martijn Grooten on Aug 9, 2018
 We are very excited to announce a special summit, as part of VB2018, that will be dedicated to all aspects of threat intelligence.
We are very excited to announce a special summit, as part of VB2018, that will be dedicated to all aspects of threat intelligence.
Posted by Martijn Grooten on Aug 7, 2018
 An industry approach for defining and detecting unwanted software to be presented and discussed at the Virus Bulletin conference.
An industry approach for defining and detecting unwanted software to be presented and discussed at the Virus Bulletin conference.
Posted by Martijn Grooten on Jul 27, 2018
 The call for last-minute papers for VB2018 is now open. Submit before 2 September to have your abstract considered for one of the nine slots reserved for 'hot' research.
The call for last-minute papers for VB2018 is now open. Submit before 2 September to have your abstract considered for one of the nine slots reserved for 'hot' research.
Posted by Martijn Grooten on Jul 25, 2018
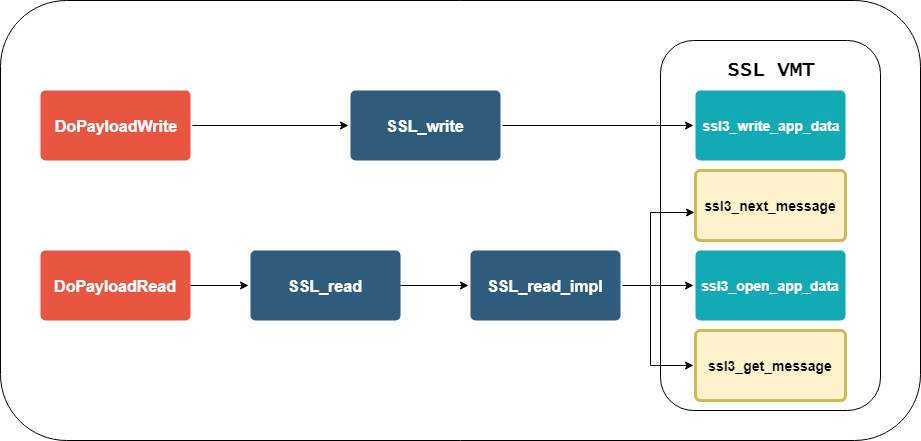 At VB2017, ESET researchers Peter Kálnai and Michal Poslušný looked at how banking malware interacts with browsers. Today we publish their paper, share the video of their presentation, and also publish a guest blog post from Peter, in which he summarises the recent developments in this space.
At VB2017, ESET researchers Peter Kálnai and Michal Poslušný looked at how banking malware interacts with browsers. Today we publish their paper, share the video of their presentation, and also publish a guest blog post from Peter, in which he summarises the recent developments in this space.