The Formbook information-stealing trojan may not be APT-grade malware, but its continuing spread means it can still be effective. At VB2018 in Montreal, Gabriela Nicolao, a researcher from Deloitte in Argentina, presented a short paper in which she looked…
The Formbook information-stealing trojan has been spread by a number of recent spam campaigns. The malware was advertised in hacking forums as long ago as January 2016, but wasn't… https://www.virusbulletin.com/blog/2019/01/vb2018-paper-inside-formbook-infostealer/
Today we publish the VB2018 paper and video by ESET researcher Filip Kafka, who looked at the new malware by Hacking Team, after the company had recovered from the 2015 breach.
It is good practice not to mock or laugh at hacking victims. But when the victim is a company that itself is in the business of hacking and has a habit of selling its products and… https://www.virusbulletin.com/blog/2019/01/vb2018-paper-hacking-team-hacked-team/
Mydoom turns 15 this month, and is still being seen in email attachments. This Throwback Thursday we look back to March 2004, when Gabor Szappanos tracked the rise of W32/Mydoom.
When a daily sports paper compares a national soccer crisis with the spread of an Internet worm, you know that the worm has had an enormous impact on everyday life. This was the… https://www.virusbulletin.com/blog/2019/01/throwback-thursday-were-all-doomed1/
We see a lot of spam in the VBSpam test lab, and we also see how well such emails are being blocked by email security products. Worryingly, it is often the emails with a malicious attachment or a phishing link that are most likely to be missed.
This blog post was put together in collaboration with VB test engineers Adrian Luca and Ionuţ Răileanu.
In a talk I gave at IRISSCON last year (the video of which you will find… https://www.virusbulletin.com/blog/2019/01/spam-hardest-block-often-most-damaging/
Have you analysed a new online threat? Do you know a new way to defend against such threats? Are you tasked with securing systems and fending off attacks? The call for papers for VB2019 is now open and we want to hear from you!
The call for papers for VB2019, the 29th Virus Bulletin International Conference, which will take place in London, UK, 2-4 October 2019, is now open!
We welcome submissions on… https://www.virusbulletin.com/blog/2019/01/vb2019-call-papers-now-open/
VB Editor Martijn Grooten reviews Charles Arthur's Cyber Wars, which looks at seven prominent hacks and attacks, and the lessons we can learn from them.
At a recent security conference, one speaker asked how many of the audience remembered the 2007 Storm Worm. Only about half the members of the audience of malware researchers… https://www.virusbulletin.com/blog/2018/12/book-review-cyber-wars/
At VB2018 Sophos researcher Gábor Szappanos provided a detailed overview of Office exploit builders, and looked in particular at the widely exploited CVE-2017-0199. Today we publish his paper and release the video of his presentation.
A large portion of today's malware infections use malicious Office documents as a first-stage payload. Typically, the user is tricked into enabling macros or disabling some… https://www.virusbulletin.com/blog/2018/12/vb2018-paper-office-bugs-rise/
Today, we release the video of the VB2018 presentation by Check Point researcher Aseel Kayal, who connected the various dots relating to campaigns by the APT-C-23 threat group.
The APT-C-23 group, which targets users in the Middle East and in particular in the State of Palestine, was named and first reported on by 360 in a Chinese language blog post in… https://www.virusbulletin.com/blog/2018/12/vb2018-video-big-bang-theory-apt-c-23/
Today, we publish the VB2018 paper by Qihoo 360 researchers Ya Liu and Hui Wang, on extracting data from variants of the Mirai botnet to classify and track variants.
The leaking or publishing of malware source code often leads to multiple spin-off families based on the code. Never has this been more clear than in the case of the Mirai Internet… https://www.virusbulletin.com/blog/2018/12/vb2018-paper-tracking-mirai-variants/
2018 has seen an increase in the variety of botnets living on the Internet of Things - such as Hide'N'Seek, which is notable for its use of peer-to-peer for command-and-control communication. Today, we publish the VB2018 paper by Bitdefender researchers A…
Until recently IoT botnets mostly consisted of Mirai and its many descendants. However, during 2018 we have seen an increase in the variety of botnets living on the Internet of… https://www.virusbulletin.com/blog/2018/12/vb2018-paper-hidenseek-adaptive-peer-peer-iot-botnet/
In a new paper, Avast researchers Jan Sirmer and Adolf Streda look at how a spam campaign sent via the Necurs botnet was delivering the Flawed Ammyy RAT. As well as publishing the paper, we have also released the video of the reseachers' VB2018 presentati…
The Necurs botnet has been active for some time. In 2014, Virus Bulletin published a 3-part article by Peter Ferrie (1, 2, 3) who had studied the botnet in great detail. And… https://www.virusbulletin.com/blog/2018/12/new-paper-botception-botnet-distributes-script-bot-capabilities/
Today we have published the video of the VB2018 presentation by Andrew Brandt (Sophos) on the SamSam ransomware, which became hot news following the indictment of its two suspected authors yesterday.
Yesterday, a federal grand jury in the US unsealed an indictment charging two Iranians with being behind the SamSam ransomware.
SamSam has been one of the most successful… https://www.virusbulletin.com/blog/2018/11/vb2018-video-behind-scenes-samsam-investigation/
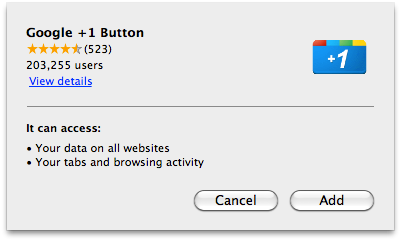 Google has made a subtle change to its Chrome browser, banning the inline installation of new extensions, thus making it harder for malware authors to trick users into unwittingly installing malicious extensions.
Google has made a subtle change to its Chrome browser, banning the inline installation of new extensions, thus making it harder for malware authors to trick users into unwittingly installing malicious extensions.
 We publish a paper by researchers from Quick Heal Security Labs in India, who study the EternalBlue and DoublePulsar exploits in full detail.
We publish a paper by researchers from Quick Heal Security Labs in India, who study the EternalBlue and DoublePulsar exploits in full detail.
 Several VB2018 papers deal explicitly or implicitly with threats that have been attributed to North Korean actors.
Several VB2018 papers deal explicitly or implicitly with threats that have been attributed to North Korean actors.
 The domain of the little-used SpamCannibal DNS blacklist had expired, resulting in it effectively listing every single IP address.
The domain of the little-used SpamCannibal DNS blacklist had expired, resulting in it effectively listing every single IP address.
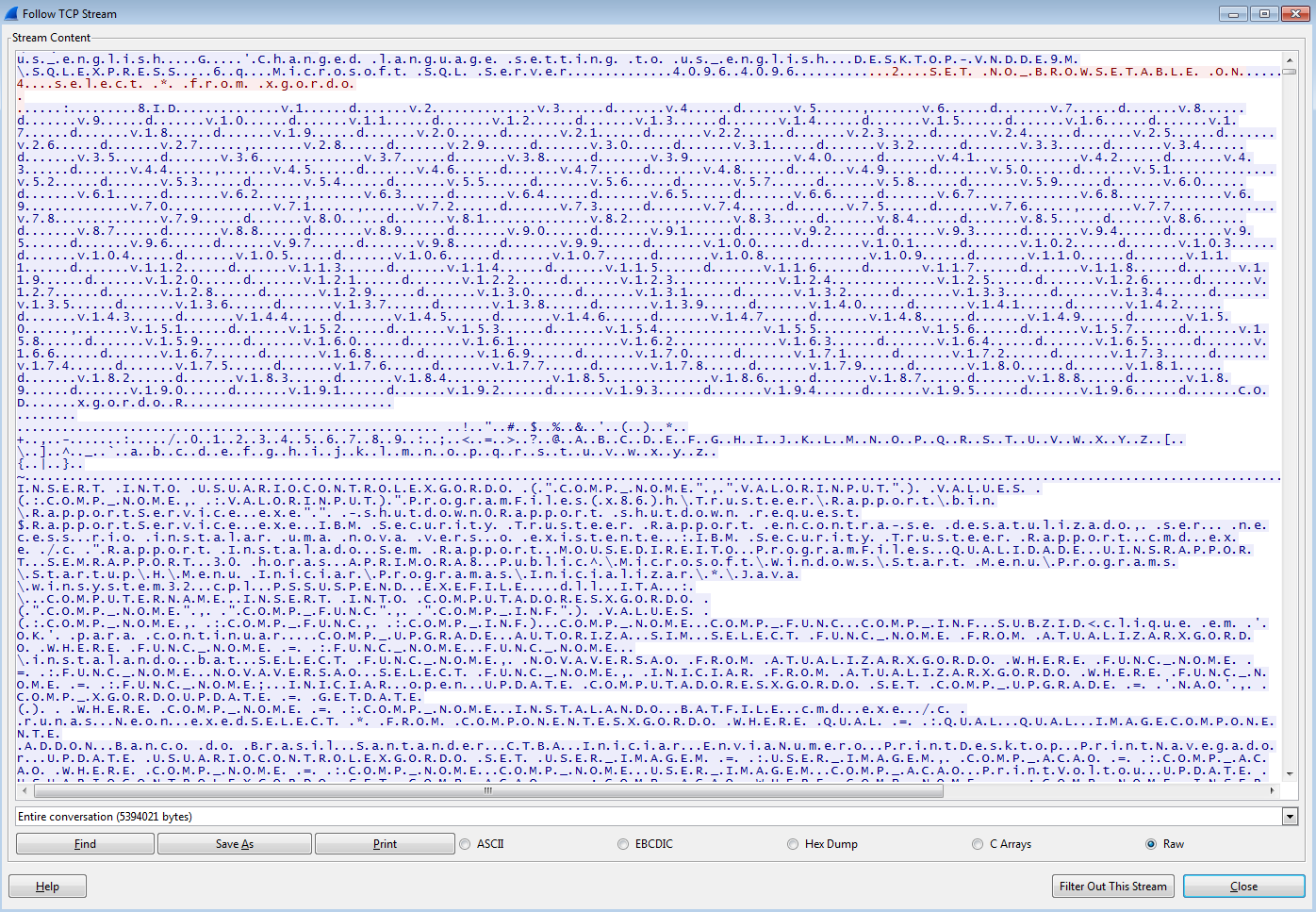 Researchers at IBM X-Force have discovered MnuBot, a banking trojan targeting users in Brazil, which is noteworthy for using SQL Server for command and control communication.
Researchers at IBM X-Force have discovered MnuBot, a banking trojan targeting users in Brazil, which is noteworthy for using SQL Server for command and control communication.
 The 68-byte EICAR test file plays as important a role today as it did 19 years ago. In this week's Throwback Thursday we look back at a VB99 conference paper in which Randy Abrams described how this 'miracle tool' worked and how it could be used.
The 68-byte EICAR test file plays as important a role today as it did 19 years ago. In this week's Throwback Thursday we look back at a VB99 conference paper in which Randy Abrams described how this 'miracle tool' worked and how it could be used.
 A new piece of cryptocurrency-mining malware on macOS has been found to use the popular XMRig miner.
A new piece of cryptocurrency-mining malware on macOS has been found to use the popular XMRig miner.
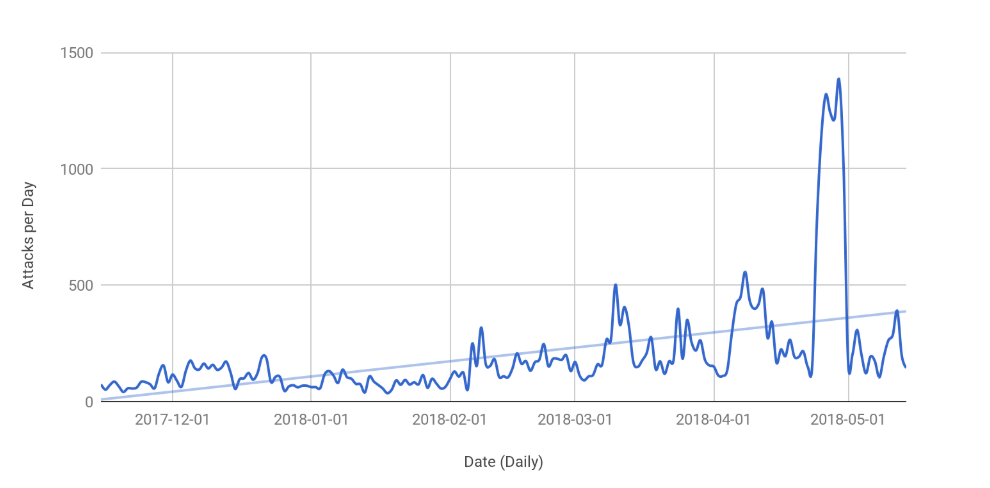 CDN provider Cloudflare reports an increase in DDoS attacks targeting layer 7 and focusing on exhausting server resources rather than sending large volumes of data. This fits in a wider trend.
CDN provider Cloudflare reports an increase in DDoS attacks targeting layer 7 and focusing on exhausting server resources rather than sending large volumes of data. This fits in a wider trend.
 Through fake social media accounts, users were tricked into installing an Android application that was actually a mobile version of the FinFisher spyware.
Through fake social media accounts, users were tricked into installing an Android application that was actually a mobile version of the FinFisher spyware.
 The Hide'n'Seek IoT botnet has received an update to make its infection persist on infected devices beyond a restart.
The Hide'n'Seek IoT botnet has received an update to make its infection persist on infected devices beyond a restart.