Posted by on Jan 31, 2020
When analysing malware, especially if it's new and rare, researchers look for every possible clue that could give them details on the context and perhaps help them find similar samples. One such clue could be what has been called ‘rich headers’, an undocumented chunk of data inside PE files.
In a paper presented at VB2019 in London, ESET researchers Peter Kálnai and Michal Poslušný discussed the subject of rich headers and how it can be useful in malware research.
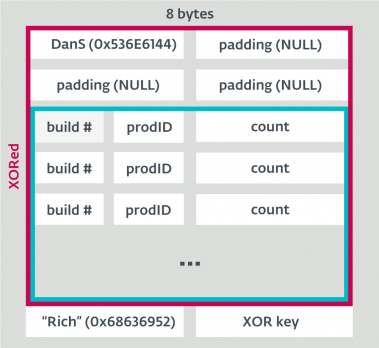 The unencrypted Rich Headers structure.
The unencrypted Rich Headers structure.
Today we publish the researchers' paper in both HTML and PDF format, as well as the recording of their presentation in London.
 Rich headers: leveraging the mysterious artifact of the PE format
Rich headers: leveraging the mysterious artifact of the PE format
Have you carried out research that furthers our understanding of the threat landscape? Have you discovered a technique that helps in the analysis of malware? The Call for Papers for VB2020 in Dublin is open! Submit your abstract before 15 March for a chance to make it onto the programme of one of the most international threat intelligence conferences.