Posted by on Sep 25, 2019
In a guest blog post VB2019 Silver partner Intezer outlines the importance of paying more attention to Linux threats.
In a previous blog post written for the Retail and Hospitality Information Sharing and Analysis Center (RH-ISAC), we discussed the emergence of Linux-based threats.
This threat ecosystem is heavily concentrated with financially driven cryptominers and DDoS botnet tools which primarily target vulnerable Linux servers. In addition, more sophisticated threats utilizing rare evasion techniques exist within the Linux platform, evidenced by the recent discoveries of HiddenWasp, and the QNAPCrypt ransomware campaigns targeting Linux-based file storage systems (NAS servers).
In the anti-virus industry, a large emphasis is placed on protecting Windows endpoints, and rightfully so — Windows desktop users comprise approximately 87% of the total desktop market share, in comparison to the 2% market share held by Linux desktop users. Because of this disparity, and the fact that we rarely see malware targeting Linux end-users, some security professionals argue that Linux is the safest and most secure operating system.
However, when discussing threats to the Linux platform, we must understand that Linux desktop usage is a very small piece of the puzzle. Linux makes up about 70% of the web server market share, and according to CBT Nuggets, 90% of all cloud servers. In a 2018 article, ZDNet reported that Linux is the most popular operating system on Microsoft's Azure Cloud.
In recent years, there has been a rapid growth in modern, cloud-based infrastructure. Linux has emerged as the predominant choice for cloud computing for two reasons:
The quick migration to the cloud, coupled with a lack of awareness into Linux instances and the threats that target these systems, have contributed to the low detection rates seen in the vast majority of security vendors.
Focus on Windows endpoints. In general, there are not many Linux protection systems, and as a result the evasion techniques are rudimentary in nature. The majority of security solutions are focused on protecting Windows environments—1) because Windows holds the majority of the desktop market share, and 2) since the cloud is a relatively new development. In addition, security vendors try to adapt their Windows tools to fit the Linux platform, but Linux is very different. As a result, these solutions are not as effective at detecting threats as they are in the Windows domain. Organizations require a tailored solution for Linux, not an adapted Windows technology.
Big picture. For enterprises that host their data on the cloud, there is a strong possibility that they are using a Linux server. Without proper detection and response mechanisms in place, organizations' cloud infrastructures can be exposed, making them more vulnerable to data breaches.
In an open-source ecosystem like Linux, there are large amounts of publicly available code that can quickly be copied and reused by adversaries in order to produce their own malware. In the case of HiddenWasp, the authors behind the malware reused large portions of code from open-source Mirai and the Azazel rootkit. While Mirai is not a highly complex malware, its code was previously leaked in 2016, and we often see the code being reused by attackers to deploy their own instances of Mirai, especially within the Linux platform.
In the world of software development, developers are incentivized to reuse code. Reusing code brings tools to market faster. The same principle applies to malware authors. Especially on the Linux platform, where detection rates have been consistently low, attackers have become less concerned about implementing excessive evasion techniques. Even when the attackers reuse extensive amounts of code, threats have managed to stay relatively undetected.
The majority of cyber attacks, whether they are targeting Linux or Windows systems, contain code from previous threats. As defenders of these environments, it's critical to analyse the binary code that is being used in these attacks. By identifying and then indexing an attacker's code, defenders can detect any future variant of the threat that uses even the smallest amounts of the same code.
This code reuse detection approach, which we call 'genetic malware analysis', is particularly relevant for detecting and classifying Linux threats, because, as we have seen in the cases of HiddenWasp and Mirai, Linux malware authors will reuse code.
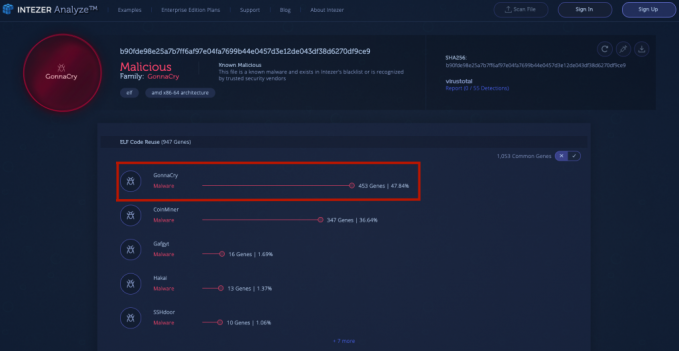
In another example, an Intezer Analyze community user recently detected a GonnaCry ransomware sample. GonnaCry is an open-source ransomware designed for the Linux platform. GonnaCry's source code is downloaded from GitHub and utilized by attackers to infect vulnerable Linux endpoints by encrypting their file systems. At the time of detection, this sample had 0/55 detections in VirusTotal. However, the sample was immediately flagged in our system because it shared 453 genes, or over 47% of its code, with previous instances of the GonnaCry ransomware.
In addition to adopting a genetic malware analysis approach, organizations can implement the following security best practices in order to mitigate the cyber threats targeting Linux-based systems:
The world of IT is changing quickly as more organizations host their data and files on the cloud. Linux, in particular, has emerged as the popular choice for cloud servers, even among Microsoft cloud computing services. Since Linux comprises nearly 90% of the cloud server market share, the majority of enterprises that host their data on the cloud are likely operating from a Linux server.
While the majority of security solutions are focused on detecting threats residing in Windows, particularly on Windows desktops, a greater emphasis needs to be placed on spreading awareness of Linux machines and threats. As defenders, we lack research and critical IOCs that can help us to better comprehend, detect and respond to Linux threats, more consistently, and on a greater scale.
As evidenced by the recent discoveries of HiddenWasp and QNAPCrypt, with improved visibility and detection rates we can expect to see new and advanced malware being created to target the Linux platform. However, we must also remember that Linux is an open-source ecosystem, where attackers will continue to reuse publicly available code to deploy new instances of malware. This is what makes indexing code seen in previous attacks so important for detecting future Linux threats.
By applying a genetic malware analysis approach, and adhering to the mitigation recommendations outlined in this blog, users of Linux-based systems — particularly organizations hosting their data on Linux cloud servers — can better protect themselves from the threats posed by this emerging landscape.