Posted by Martijn Grooten on Aug 26, 2019
Active since 2014, initially as a banking trojan, Emotet has been a plague on the Internet in recent years. Emotet's core strength is its ability to download other malware, thus giving those in control of it remote code execution on infected systems and networks. Emotet has been the initial infection in many high-profile attacks, in particular with ransomware such as Ryuk and MegaCortex.
Early in June, Emotet mysteriously ceased its activities and researchers were left guessing what happened. However, late last week the malware's command-and-control servers became active again, though for now no new binaries have been served.
At VB2019 in London, Sophos researcher Luca Nagy will present a thoroughly researched paper on Emotet, in which she studies its binary and the various modules in great detail.
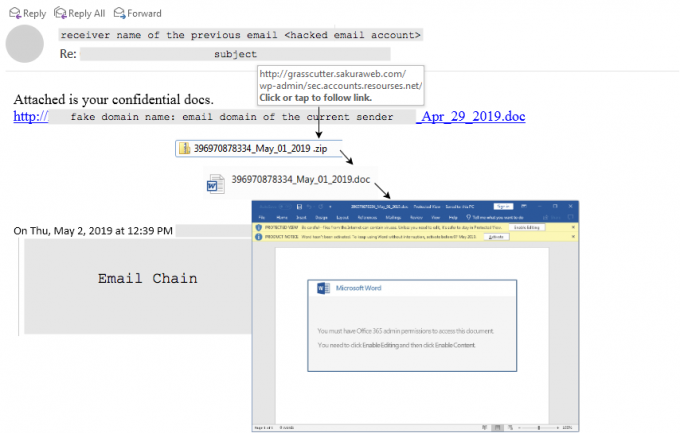
Understanding a threat like Emotet would have been important even with the threat itself gone, given how many attackers use a similar playbook, but with the return of Emotet, Luca's paper will be even more important.
To see this important presentation - and more than 50 others - don't forget to secure your place for VB2019! And if you have some hot research to present, don't forget the call for last minute papers is open until 1 September.