Posted by on Nov 1, 2018
Early computer viruses were often destructive in nature, but once criminals learned about the money they could make from malware, they realised that destructiveness hurt their goals. Destructive malware, however, has made a comeback in recent years, most importantly in nation-sponsored attacks.
Some of these malware variants literally wipe all data off disks (hence the name 'wiper'), while others merely encrypt the data in a way that doesn't allow for recovery, often masquerading as ransomware: the notorious 2017 attacks of WannaCry and NotPetya are examples of the latter.
In a paper presented at VB2018 in Montreal last month, BAE Systems researcher Saher Naumaan looked at the various kinds of malware that contain a wiper variant, including their goals, propagation methods, and how the wiper functionality worked.
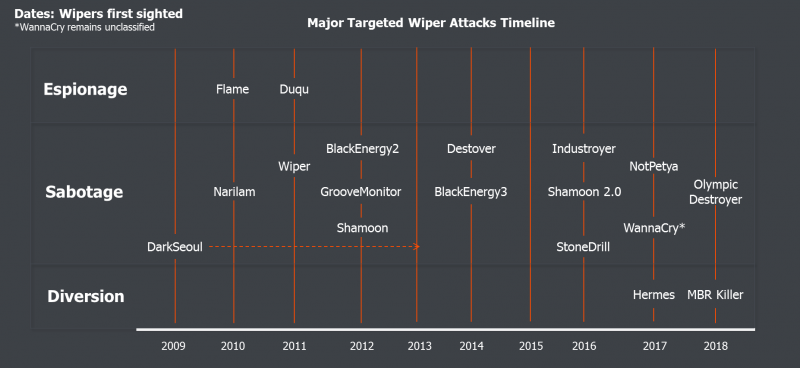 Major targeted attacks employing wipers and classifications.
Major targeted attacks employing wipers and classifications.
We have now published Saher's paper in both HTML and PDF format. We have also uploaded the video of her presentation to our YouTube channel.