Posted by Martijn Grooten on Apr 16, 2018
Patching is important, but not everything that presents itself as a security patch is safe to install.
Malwarebytes researcher Jérôme Segura has written a detailed analysis of the 'FakeUpdates' campaign, where thousands of websites with an out-of-date content management system have been compromised to spread malware. Rather than exploiting vulnerabilities in browsers or browser plug-ins, as is common in exploit kits, this campaign uses social engineering to trick a user into installing malware.
A visitor to such a site would be presented with a dialog urging them to update their browser or their Flash Player plug-in, but the update is, in fact, a script, hosted on Dropbox, that downloads the final payload. Jérôme mentions having seen both the Chthonic banking trojan and the NetSupport RAT being delivered; both have been used in exploit kits in the past.
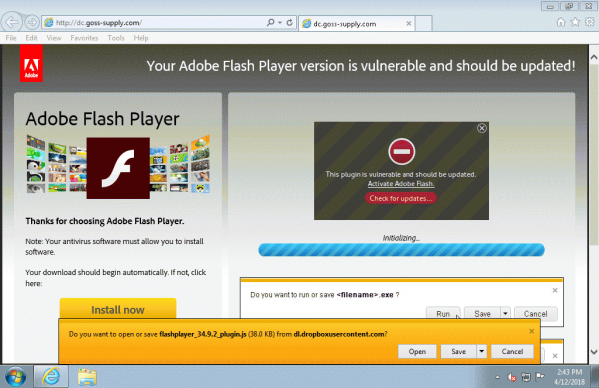 A compromised site running Joomla serving a Dropbox-hosted .js file masquerading as a Flash Player update. (Thanks to Adrian Luca for the screenshot.)
A compromised site running Joomla serving a Dropbox-hosted .js file masquerading as a Flash Player update. (Thanks to Adrian Luca for the screenshot.)
Though technically not very advanced, this threat might not be picked up by many automatic analysis systems since it requires user interaction. Moreover, to further frustrate researchers, the dialog is shown only once per IP address.
One of the leading researchers in web-based malware, Jérôme will speak at VB2018 on another recent trend in web-based malware: drive-by cryptocurrency miners. VB2018 takes place in Montreal, Canada 3-5 October this autumn. The programme was published last week; registration will open soon.