Posted by Martijn Grooten on Feb 15, 2018
The organisers of the Pyeongchang Winter Olympics have confirmed a malware attack against their computer systems. Though the attack affected the Wi-Fi during Friday's opening ceremony and knocked the event's website offline for a few hours, no permanent damage appears to have been done.
Cisco Talos researchers Warren Mercer and Paul Rascagneres have performed a thorough analysis of the malware, which is noteworthy because of the way in which it handles stolen credentials: after stealing credentials from various locations on the system, the binary is patched with these new credentials added to the existing list. The malware then uses the legitimate PsExec tool to move laterally within the target network. The abuse of PsExec for lateral movement isn't new; we have seen it used, for instance, in (Not)Petya.
The attack may be related to a reconnaissance attack against Atos, the Olympics' IT provider, a few months before the start of the Games. Interestingly, at VB2017 in Madrid, Warren and Paul spoke about such reconnaissance attacks.
Another analysis of the malware was performed by researchers at Endgame, who looked at how another legitimate tool, notepad.exe, was leveraged for shellcode injection.
It doesn't take a great insight into geopolitics to think of some obvious nation states that might be behind the attack. But even Recorded Future – which, unlike many other security firms, often doesn't hesitate to link a malware attack to a particular group or nation state – says the attack remains unattributed.
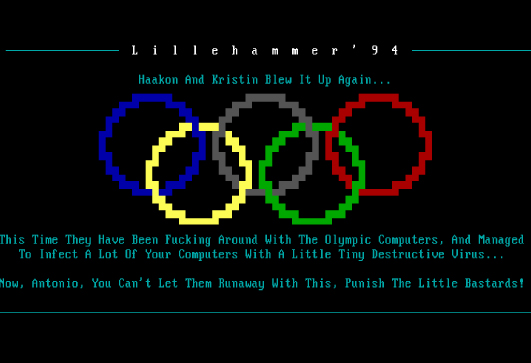
This isn't the first time that the Winter Olympics has been the target of a malware attack. 24 years ago, the Lillehammer Olympics were both the subject and the suspected target of the 'Olympic' or 'Olympic Aids' virus, though in the end it turned out that the destructive virus had not infected the computer systems used by the organisation.
In March 1994, Mikko Hyppönen of F-Secure (then known as Data Fellows) wrote an analysis of the virus for Virus Bulletin. We republished it in 2016 in both HTML and PDF formats and thought it worth highlighting again.
Back in 1994, attribution was easy, as the typical virus was written as an 'ego trip for [a] gang of teenagers'. The 'Olympic' virus was written by the Sweden-based 'Immortal Riot' crew.
As far as I know, in 1994, there was no doping scandal involving Swedish athletes, and the separation of the Olympics organising country, Norway, from Sweden in 1905 was not considered a politically sensitive issue.