Posted by Martijn Grooten on Nov 24, 2017
Over the last few years, the infamous FinFisher government spyware (already the subject of a VB2013 paper) has done a good job of staying under the radar. Recently, however, it made the news because of its use of the then zero-day CVE-2017-8759 and the likely involvement of ISPs in targets getting infected.
In a well-received VB2017 last-minute paper, ESET researcher Filip Kafka took a close look at the malware itself, including its anti-disassembly features, as well as at its new infection mechanism.
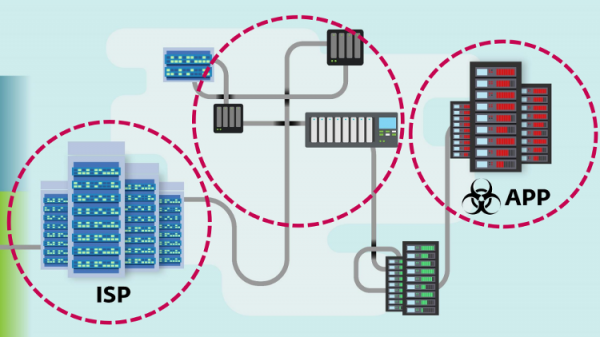
Today, we have uploaded Filip's paper to our YouTube channel, and also published his slides.
In two weeks' time, Filip will speak again on the same subject, at AVAR 2017 in Beijing, China.