Posted by Martijn Grooten on Jul 18, 2017
It is a truth generally acknowledged that there is no such thing as absolute security. Security is always a compromise with usability, and good security is about finding the right kind of compromise for the particular threat model you're defending against.
Password security is a good example. Ideally, one should use a very strong unique password for every account and then make sure one remembers them all. In practice, this would require superhuman capabilities.
Overheard password advice "Pick something you can't remember, then don't write it down"
— Mikko Hypponen (@mikko) August 15, 2011
To compromise on these unworkable requirements, many people drop the uniqueness element and use the same, very strong password for all their online accounts and then make sure they memorise it. To security experts the dangers of this are obvious, and an article in the Sunday Telegraph showed how costly this can be, but is our advice helping users?
There are many websites and blog posts that explain how to choose a secure password, and while they tend to give sensible advice they often miss the most important point: barring obvious choices such as '123456' or 'password', the strength of a password plays a role in only a very limited number of attacks. Rather, password reuse or (and often combined with) phishing attacks play a much bigger role. The strength of John Podesta's password stopped mattering the moment he entered it into Fancy Bear's phishing page.
Although two-factor authentication (2FA) is again no silver bullet, and may not have deterred attackers of Fancy Bear's capabilities, it raises the bar for attackers significantly. For this reason, it should be used on accounts that matter, even if the only 2FA option uses SMS, which we know has been broken, it's still much better than using only a password.
Next to using 2FA wherever possible, a password manager can help you manage strong and unique passwords for all your accounts: putting all but the most important passwords in such a tool can take away most of the pain of managing passwords.
Password managers do come with an important weakness though: a single point of failure through which an adversary can access all your passwords if they manage to obtain your master passwords. For most accounts that is an acceptable risk, but if you think it isn't, maybe you are able to memorise a few dozen half-decent passwords. If it would help you, writing them down in a notebook isn't as bad an idea as it is purported to be against most (but not all!) adversaries. Just don't ever reuse them!
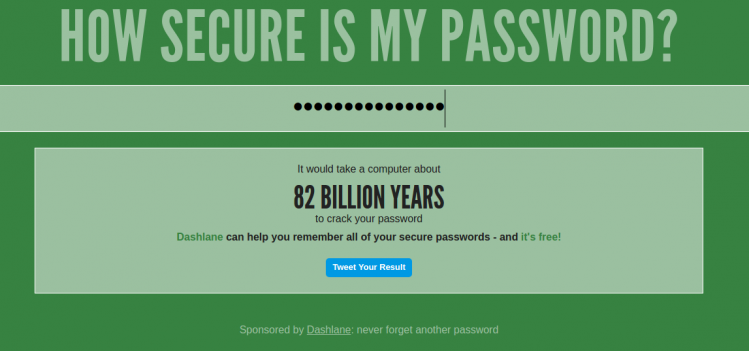
There are plenty of sites where you can check the strength of your password. But shouldn't these have a tickbox where you need to state you're not using the password anywhere else?