Posted by Martijn Grooten on Jul 5, 2016
Keyloggers have long been a popular tool for cybercriminals, something made worse by the fact that many of them are sold commercially.
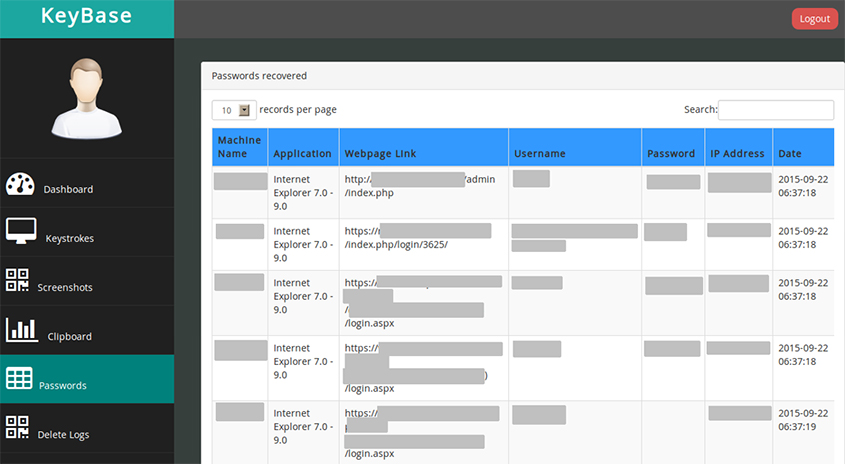
Today, we publish a paper (here as a PDF) by Sophos researcher Gabor Szappanos, in which he studies the 'KeyBase' keylogger. Though the product has officially been discontinued, allegedly because of abuse by criminals, it remains widely used and spreads via Office exploit kits.
Gabor looks at how KeyBase exfiltrates data from a target machine and also shows what it looks like from the other side, by taking a look at the keylogger's admin panel.
If you like this paper, make sure you also read MWI-5: Operation HawkEye, another paper by Gabor we published last year, in which he looks at the use of the HawkEye keylogger by cybercriminals.