Posted by Virus Bulletin on Apr 2, 2015
Details of malware to be discussed at VB2015.
Researchers at Check Point have revealed details of a cyber-espionage campaign, dubbed 'Volatile Cedar', that has been active since at least 2012.
The campaign, whose motive appears to be political rather than financial, revolves around a custom-made remote access trojan named 'Explosive', which is separated into a main binary and a DLL file.
This separation allows the attacker to quickly patch the trojan, both to update functionality and to avoid heuristic detection. Indeed, it appears that every time the malware started to become detectable by anti-virus solutions, a new version was created. The most recent version is still active.
To control the infected machines, Explosive's authors set up a command and control (C&C) infrastructure which includes both static and dynamic C&C servers, the latter using domain generation algorithms.
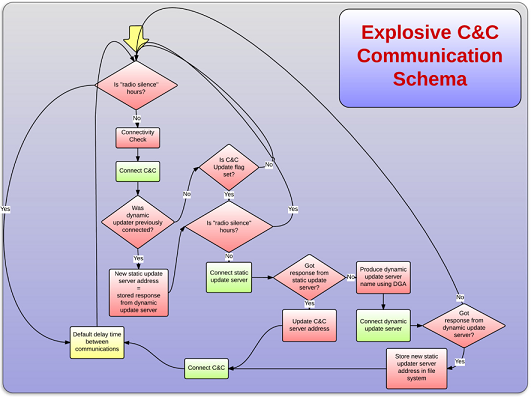
Targets of the campaign appear to be carefully selected, and based on these as well as some circumstantial evidence, the researchers believe the attacker group to be based in Lebanon and to have political ties.
Interestingly, rather than using spear phishing, as is common among so-called APT attacks, Explosive's initial targets were public-facing Windows servers. From there, attackers would look for further targets on the same internal network.
Full details on the malware can be found in a technical report (pdf) published by Check Point, while researchers from Kaspersky Lab wrote a blog post on their findings based on sinkholing the malware.
This campaign will also be the subject of the presentation 'The Unbearable Lightness of APTing' at VB2015, the programme for which we announced yesterday. VB2015 takes place 30 September to 2 October in Prague, Czech Republic. Registration for the conference will open soon.
Posted on 02 April 2015 by Martijn Grooten