Posted by Virus Bulletin on Feb 20, 2015
Shared root certificate makes for easy man-in-the-middle attacks.
What is Superfish?
Superfish is a product that offers 'Visual Search'. Say, for example, you are looking at cat photos on the Internet. Superfish inserts photos of similar cats into your browser, with links to places where you can buy them.
Sounds like something that enhances my browsing experience. How can I get it?
It is installed for free on many Lenovo laptops!
Awesome. Nice one, Lenovo! So how does it insert those images?
It runs a web proxy on the computer that intercepts and, if necessary, manipulates the requests.
Clever. But if I'm connecting to a site using HTTPS, it won't be able to intercept the requests, right?
Actually, it is able to do so. Superfish installs a root CA certificate on the computer that allows it to intercept HTTPS requests as well.
Is that a good idea?
No, it is — with apologies for the bad pun — super fishy.
Touching an HTTPS connection should only be done when there is a very good reason for doing so. Showing ads is never a good reason.
Still, the creators of Superfish could use a different certificate, with a different key pair, for each installation, thus keeping the attack vector pretty small.
So?
They didn't. They used the same certificate for all installations.
What can an attacker do?
An attacker can extract the private key of the certificate, set up a public Wi-Fi network (or perhaps apply to Starbucks to become a barista) and read all the supposedly encrypted HTTP traffic from Lenovo users connecting to it.
And what about the NSA?
In the coffee shop that is the Internet, the NSA is your barista.
Is Superfish malware?
Superfish is like the neighbour to whom you have given your house keys in order to look after your plants while you're away - who then opens your front door to let your cat in. You don't even have a cat. And she doesn't bother to close the door afterwards, let alone lock it.
Your neighbour isn't a thief though, and likewise, Superfish isn't malware. It is very bad and unwanted though.
Do anti-malware products block Superfish?
Many of them do, and they also let you remove the product. Yet that doesn't solve the actual problem: if the root certificate is present on your system, you remain vulnerable even if the product is removed.
Moreover, as F-Secure's Sean Sullivan points out, prompting customers about software that has been pre-installed on the PC is a nightmare for customer support.
Surely certificate pinning prevents these kinds of man-in-the-middle attacks?
Certificate pinning 'pins' the certificate used by a remote website. Should a site suddenly present a different certificate to the browser, it will show an error, even if the certificate itself is valid.
Unfortunately, certificate pinning doesn't work for private certificates. This may seem counterintuitive, but doing so would cause problems when a user deliberately installs a private root certificate — perhaps that of a corporate web gateway. For this reason, pinning wouldn't have prevented abuse of the Superfish certificate.
How did Lenovo respond?
Its CTO admits that the company didn't do enough and promises to wipe the product off all affected PCs. The company also provided instructions on how to remove Superfish and the root certificate.
Well, that's nice, isn't it?
It is. But the firm's initial response was a lot more dismissive, and they still speak of 'theoretical concerns'. Moreover, while it is practically impossible to be absolutely certain that third-party software doesn't engage in malicious behaviour, the installation of a root CA certificate should have been detected.
Is anyone actually abusing it?
There have been no reports of abuse so far, but abuse won't be easy to detect - certainly not for the average user. Moreover, even if no one has abused it, your door is still wide open. Calling that a 'theoretical concern' is a bit of an understatement.
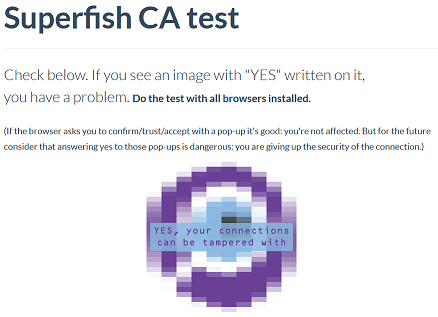
How do I know if I am vulnerable?
Several people have built websites that let you check if you are vulnerable. This one is from CloudFlare researcher Filippo Valsorda.
Filippo points out that in some cases, a user is reported to be vulnerable not because of this issue, but because certificates aren't verified at all.
So who is behind this?
The SSL interception product is based on the Komodia SDK. Unfortunately, Superfish isn't the only product that makes use of it.
Komodia's website is here. The site doesn't support HTTPS. Earlier today, it was suffering from a DDoS attack.
What laptops are affected?
Lenovo lists dozens of PC models that may have included Superfish. These are all consumer PCs. Devices for the corporate market are not affected.
Will everyone follow the instructions to remove the software and the certificate?
If only. If even ten per cent of the affected users removed the software and certificate, it'd be a big win for the security community. Thankfully, there are some options, both for Microsoft and for browser developers, to solve this problem remotely for all affected users. Matthew Green looks at these.
Why did Lenovo install Superfish in the first place? Do users like it so much?
Some users will no doubt like it. Many others will not mind it too much and will like the fact that it allowed Lenovo to make its laptops slightly cheaper.
Shouldn't we just pay a bit extra to have PCs with just the operating system installed (if at all) and nothing else?
Sure, that is the sensible thing to do. But not everyone has a well-paying job in IT security. For some, the add-ons, much as they are unwanted, could make laptops affordable.
Is Superfish the only dodgy adware product?
Unfortunately not. Many adware products stay well within the lines of what is acceptable and implicitly enhance the user experience by making products cheaper. Several others do not.
Have you performed research into misbehaving adware products? Why not share it with the security community and submit an abstract for VB2015?
Posted on 20 February 2015 by Martijn Grooten