Posted by Virus Bulletin on Sep 10, 2014
Use of single XOR key leaves ransomware open to known-plaintext attack.
It has been said many times before: cryptography is hard. Earlier this year, the authors of the 'Bitcrypt' ransomware discovered this too, when they confused bytes and digits and made their encryption keys easy to crack.
'TorrentLocker' is a new kind of encryption ransomware that was first discovered by iSIGHT Partners last month. It uses components of both 'CryptoLocker' and 'Cryptowall', possibly the two biggest ransomware 'success' stories of the past year.
However, in a guest post for Sans Digital Forensics, three researchers from NIXU in Finland revealed that they have discovered that TorrentLocker makes a fairly basic cryptography blunder, making it relatively easy to recover encrypted files.
The researchers, Taneli Kaivola, Patrik Nisén and Antti Nuopponen, explain how TorrentLocker uses XOR to encrypt the files. XOR is a very simple operation between two sequences of bits; the output of the operation is a sequence that denotes whether the two input bits differ. If they do, the output bit is 1, otherwise it is 0.
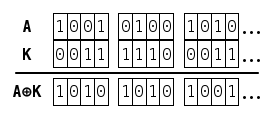
In the case of a file A, seen as a series of bits, TorrentLocker uses a keystream K to produce the output A ⊕ K and uses this as the encrypted file, while the original file is discarded. If the keystream K is pseudo-randomly generated, the 'adversary' (in this case someone trying to retrieve the files) has no way of getting the content of the file A.
XOR is a very simple and fast operation, which has the nice property that ( A ⊕ K ) ⊕ K = A, so that decryption is easy for someone who does possess the keystream K.
Fortunately for victims of the ransomware, the malware authors made two basic mistakes. The first is that they only encrypted the first 2MB of each file; parts of the file beyond 2MB were left unencrypted. Moreover, and crucially, they used a single keystream for all files.
This makes TorrentLocker vulnerable to a known-plaintext attack: an 'attack' whereby someone possesses both an unencrypted file A and its encrypted equivalent A ⊕ K. This is actually rather likely - some of the encrypted files will have been sent to or received from third parties.
Using these two files, and the formula ( A ⊕ K ) ⊕ A = K, one can thus retrieve the keystream K. Moreover, if file A is at least 2MB in size, the full keystream is retrieved and all files can be decrypted.
It is always something of a relief that malware authors are humans too and make mistakes just like everyone else. Still, this isn't something one should count on: the best proactive measure against ransomware remains keeping backup copies of all important files.
Posted on 10 September 2014 by Martijn Grooten