Posted by Virus Bulletin on Aug 27, 2014
Patrick Wardle shows that OS X users really have something to worry about.
In the weeks running up to VB2014 (the 24th Virus Bulletin International Conference), we will look at some of the research that will be presented at the event. Today, we look at the paper 'Methods of malware persistence on Mac OS X', by Patrick Wardle (@patrickwardle), Director of Research at Synack.
The very first in-the-wild virus, Elk Cloner, targeted Macs (in particular the Apple II). Yet over the course of time, many Mac users came to believe that they were immune to malware - a belief no doubt strengthened by an Apple marketing campaign.
In recent years, this belief has been proven wrong, for instance by the prevalent 'Flashback' trojan, or the 'Crisis' rootkit, allegedly used by some governments. And indeed, Apple has built a number of tools into OS X with the explicit purpose of keeping malware at bay.
However, as Patrick shows in his paper, tools such as XProtect and Gatekeeper are relatively easy to bypass. OS X's verification of binary signatures, and even the fact that kernel extensions need to be signed, don't provide the protection they promise. In the latter case, the fact that verification takes place in user mode certainly doesn't help.
Getting a piece of malware to run once usually isn't what its authors are after though: they want the malware to persist, by running in the background as a daemon or by being launched every time the user logs in. Patrick's paper describes various methods that can be used to make this happen.
Turning a binary into a launch daemon or agent (non-application binaries that run in the background), for instance, is as simple as inserting an XML file into a particular directory. This is how Flashback managed to infect more than 600,000 devices, making it the most successful OS X malware to date. Crisis, which was delivered via targeted exploits and employed some sophisticated stealth capabilities, also persisted as a launch agent.
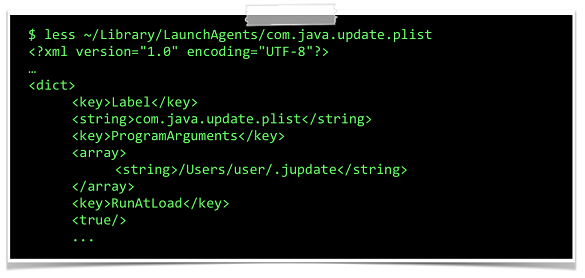
A different persistence method is used by 'Kitmos', another malware family that targets activists. To ensure the spyware is executed every time the user logs in, it registers itself as a 'login item', the 'Apple-approved' way for applications to persist. Again, it requires a single file for an app to become a login item.
Patrick's paper - which contains many more examples of persistence techniques - should convince even the most stubborn members of the "Macs can't get viruses" brigade that, in fact, there are a number inherent weaknesses in OS X's anti-malware mechanisms that help those creating malicious software.
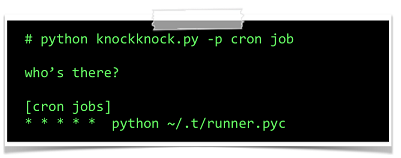
Thankfully, there is a positive conclusion to the paper: Patrick has created a tool, known as KnockKnock, which shows users which persistent binaries are running on the system. The tool is open source and is available from Synack's Github page.
You can now register for VB2014. And if you have some research that you want to share with the security community, why not submit an abstract to fill one of the seven remaining 'last-minute' presentation slots? (Deadline 28th August 2014.)
Posted on 27 August 2014 by Martijn Grooten